Visualized protocol analysis method and system for fire-fighting Internet of Things data
A technology of data analysis and protocol analysis, which is applied in the field of protocol analysis of fire-fighting Internet of Things data, can solve the problems of time-consuming and labor-intensive analysis, and achieve the effects of increasing development time, fast, accurate and efficient development, and increasing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
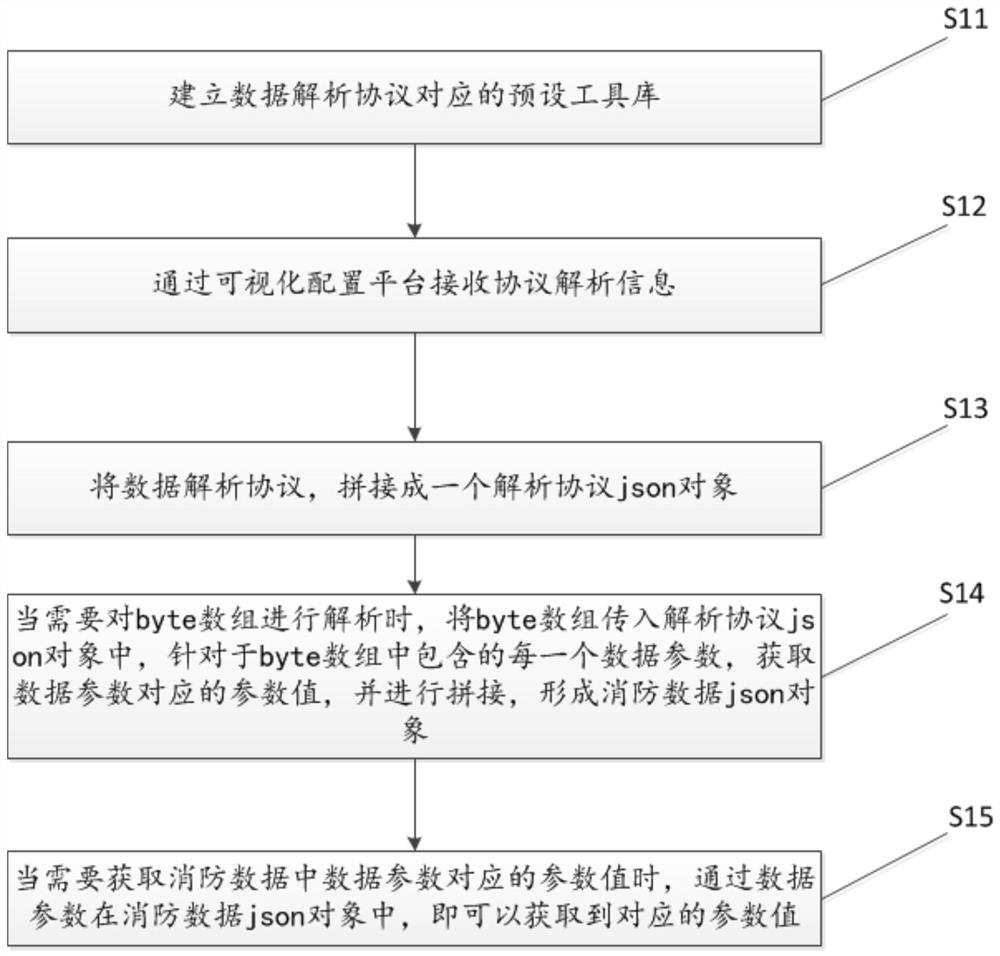
[0065] Such as figure 1 As shown, it is a specific flow chart of a protocol analysis method for visualized fire-fighting Internet of Things data in the present invention. it includes:
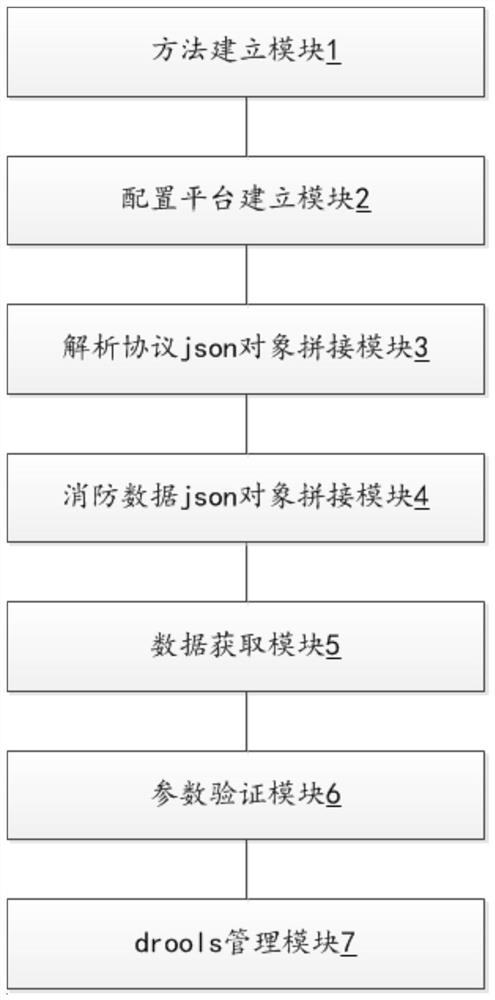
[0066] S11: Aiming at the data analysis protocol for analyzing the fire data transmitted in the fire protection Internet of Things, establish a preset tool library corresponding to the data analysis protocol, and store the preset method applied in the data analysis protocol in the preset in the tool library.
[0067] Specifically, in this embodiment, in the data analysis protocol of fire protection data, some preset methods are generally used. The data analysis process is to use a plurality of different or the same preset methods according to the The analysis logic is the process of calling the preset methods one by one to analyze the fire data. A preset tool library is established in the server in advance, and some preset methods are written into the preset tool library. In the follow-up, ...
no. 2 example
[0087] Compared with the first embodiment, the steps are basically the same, and the biggest difference is that in S14, when obtaining the parameter value corresponding to the data parameter in the fire data, it also includes: verifying the data parameter, specifically The steps are:
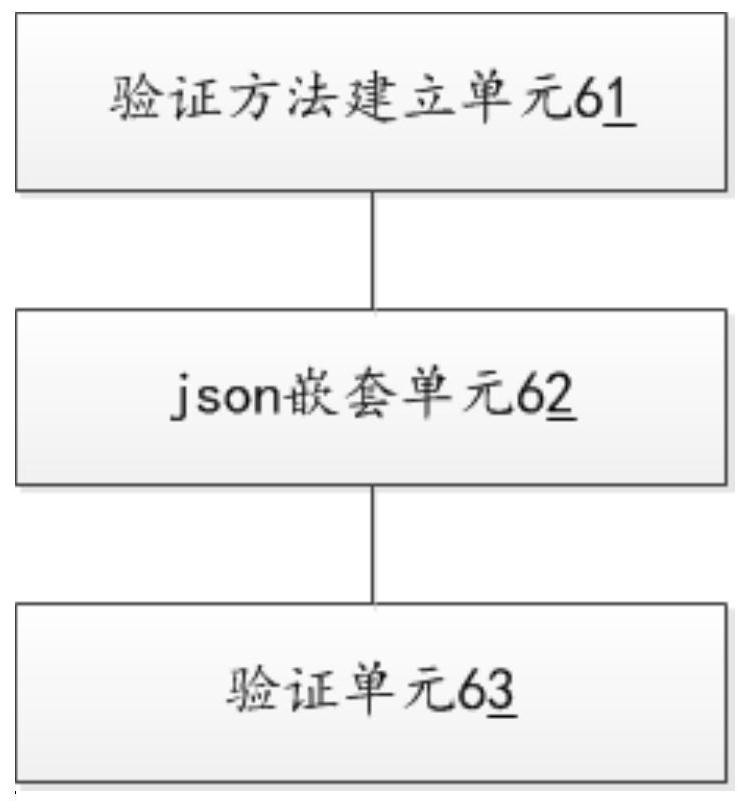
[0088] The preset method for verifying the data parameter is added in the preset tool library.
[0089] In the object value of the data parameter in the parsing protocol json object, an object for verifying the data parameter and an object for parsing after the data parameter is verified are nested, wherein the verification The object value of the data parameter object stores the preset method for verifying the data parameter and the corresponding method parameter for calling the preset method, and the method parameter for calling the preset method is used when the data parameter is verified. The name of the preset method for parsing the data parameter and the corresponding method paramet...
no. 3 example
[0097] Compared with the second embodiment, the biggest difference is that when verifying the data parameters, the drools rule engine is used to manage the process of parsing the fire data through the data parsing protocol, and the data parameters will be verified The part is written into the rule condition part of the drools rule engine, and the part parsing the data parameter is written into the rule result part of the drools rule engine; when executing the drools rule engine, only when the drools rule engine The rule result part of the drools rule engine will be executed only after the execution of the rule condition part is passed.
[0098] Specifically, in this embodiment, when the parameter value of the fire data parameter is obtained during operation, the when part is written into the rule condition part of the drools rule engine, and the result part is written into the rule result part of the drools rule engine. According to the execution mechanism of the drools ru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com