Threat behavior detection and model establishment method and device thereof, electronic equipment and storage medium
A technology for detecting models and behaviors, applied in the field of network security, can solve the problems of low detection efficiency of internal threat behaviors and occupation of computing resources, and achieve the effects of reducing resource and time consumption, improving modeling efficiency, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
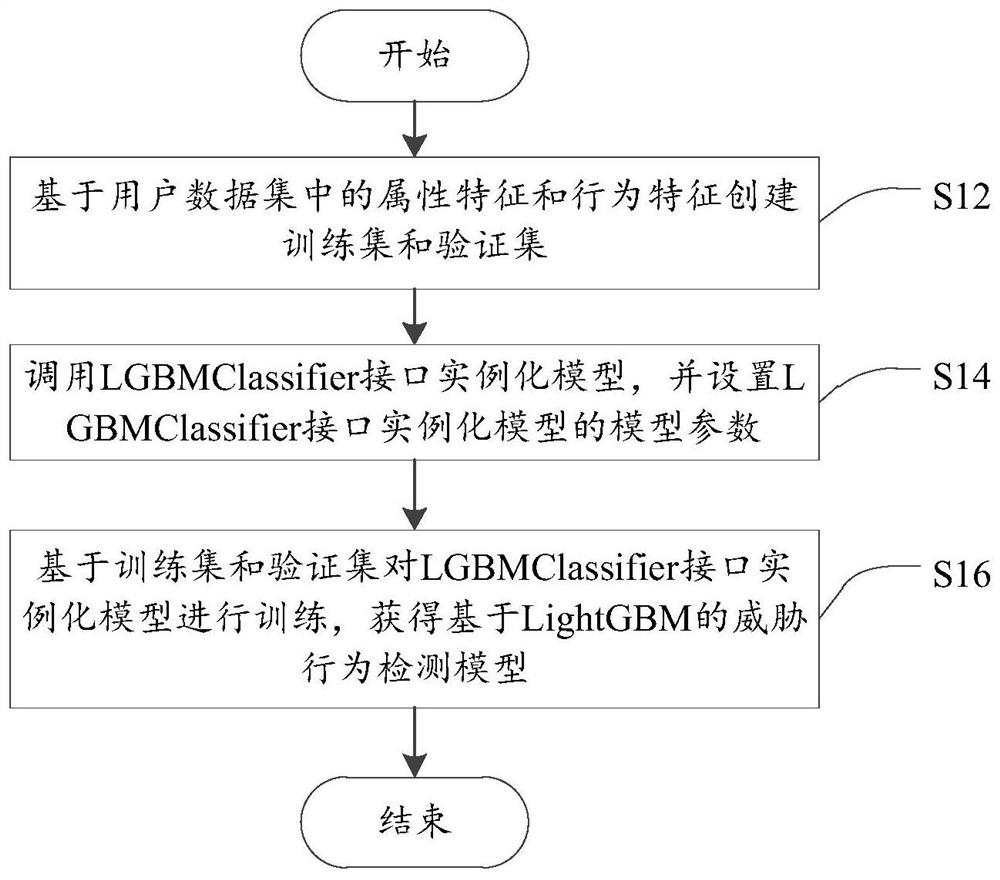
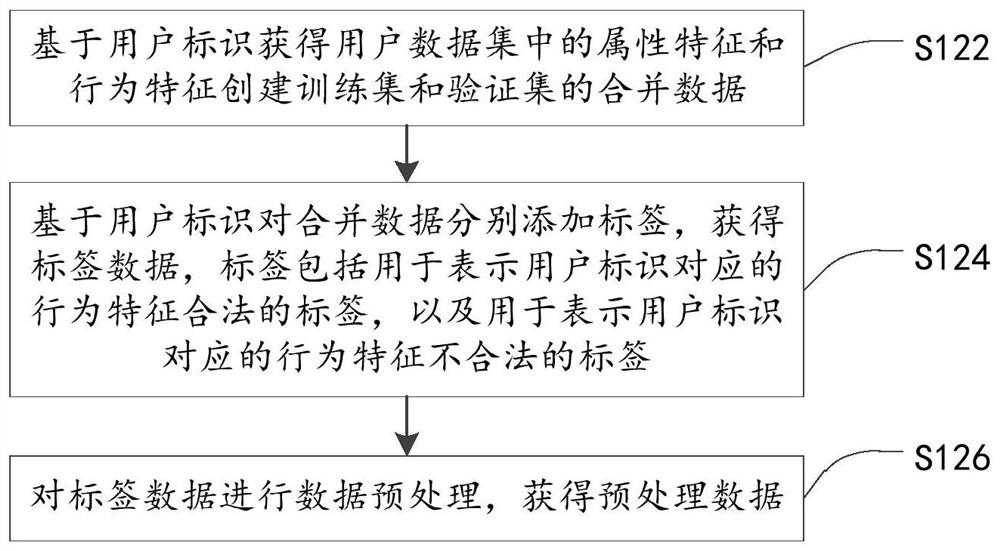
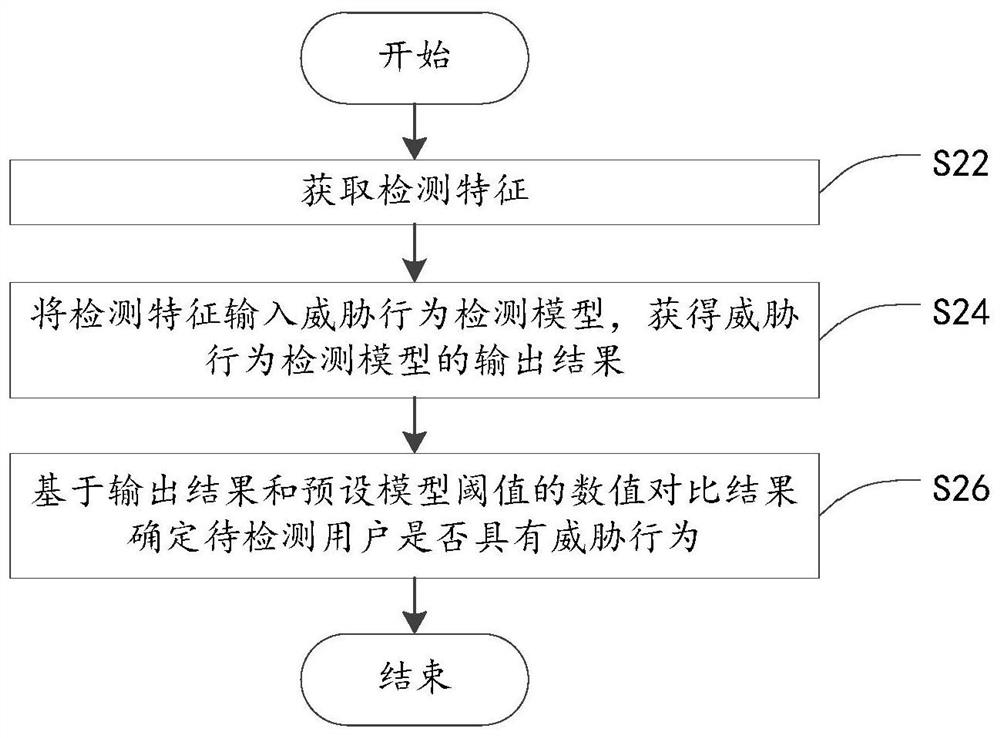
[0038] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
[0039] In the existing network security protection technology, the methods of detecting internal threats include: method 1, collecting user attribute information, including name, age, gender, psychological evaluation, interpersonal communication, work completion quality, job satisfaction, etc.; After the data is cleaned and preprocessed, the similarity between users is calculated through user portraits; the K-Means algorithm is used to cluster user attribute portraits to obtain user groups with similar behavior patterns; the second method is to obtain user behavior information and identification information; According to the user's behavior sample set, train the long-short-term memory network classification model; judge whether the classification is correct according to the user identification inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com