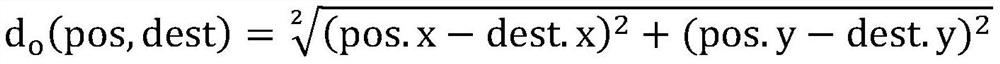Track privacy protection method based on k anonymity
A privacy protection and trajectory technology, applied in location-based services, electrical components, wireless communications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
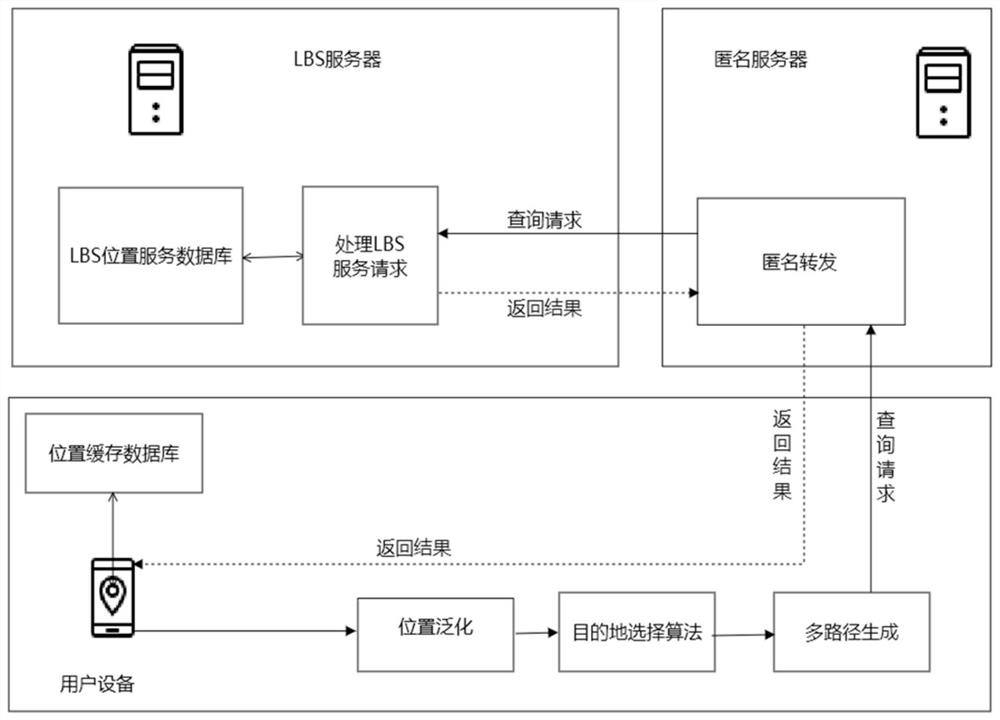
[0049] The technical solution of the present invention mainly includes three elements: user equipment, anonymous server and LBS server. Each element communicates through the communication equipment provided by the mobile operator. The user equipment is mainly responsible for forming a location generalization area, screening the results it needs, and forming query information; the LBS server is responsible for anonymously forwarding the query information sent by the user equipment to the The LBS server sends the query results of the LBS server to the corresponding users; the LBS server provides accurate query results for user queries.
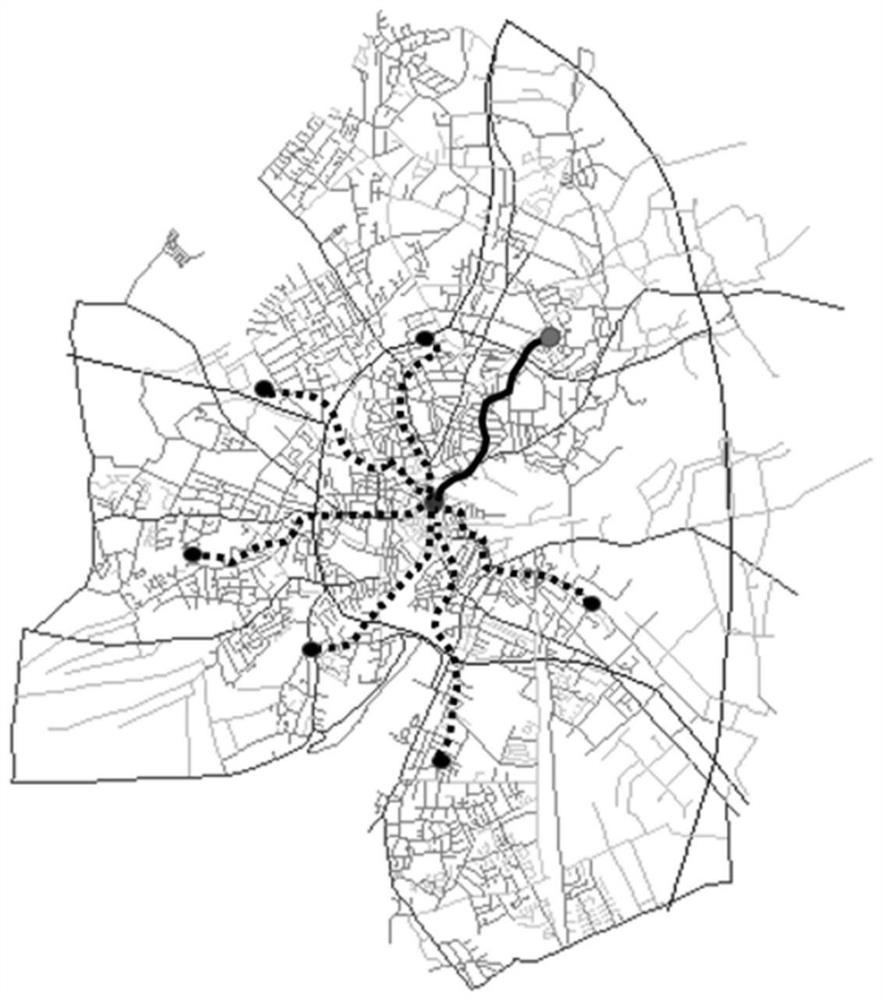
[0050] The method of the present invention includes six stages of system initialization, location generalization, multi-destination selection, anonymous forwarding, multi-path generation and temporary query. Among them, in the system initialization phase, the user registers with the LBS server, the LBS server sends the location cache to the regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com