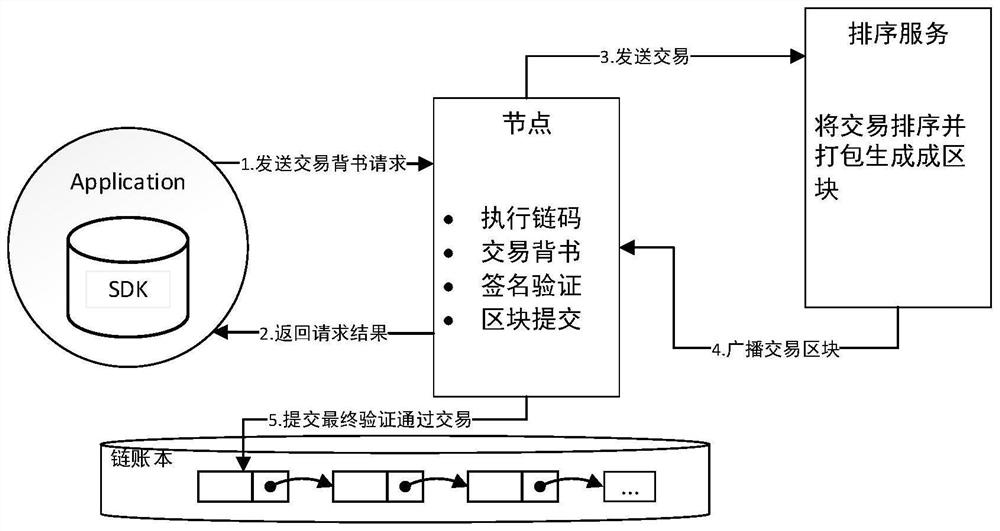
Ring signature method applied to threat intelligence transaction alliance chain
A ring signature and transaction technology, applied in user identity/authority verification, digital transmission systems, secure communication devices, etc., can solve problems such as alliance chain conflicts, and achieve the effect of protecting identity privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings.
[0030] The purpose of the present invention is to provide a ring signature method applied in the threat intelligence transaction alliance chain for the identity privacy protection of the transaction endorsement user in the threat intelligence transaction alliance chain, which is used for the endorsement user in the threat intelligence transaction alliance chain Identity privacy encryption.
[0031] (1) Processing method in the initialization stage: output the system security parameter λ, and initialize the parameters required in subsequent encryption and verification stages. The initialization phase is executed only once, and its initialization parameters remain unchanged in all transactions of the alliance chain.
[0032] (2) Processing method in the key generation stage: After the system initializes relevant parameters successfully, any node E in the endorsement nod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com