Information safety sharing method for power industry multi-service subjects
A technology for power industry and information security, applied in the field of information security, can solve the problem that the security of information transmission cannot be effectively guaranteed, and achieve the effect of improving randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
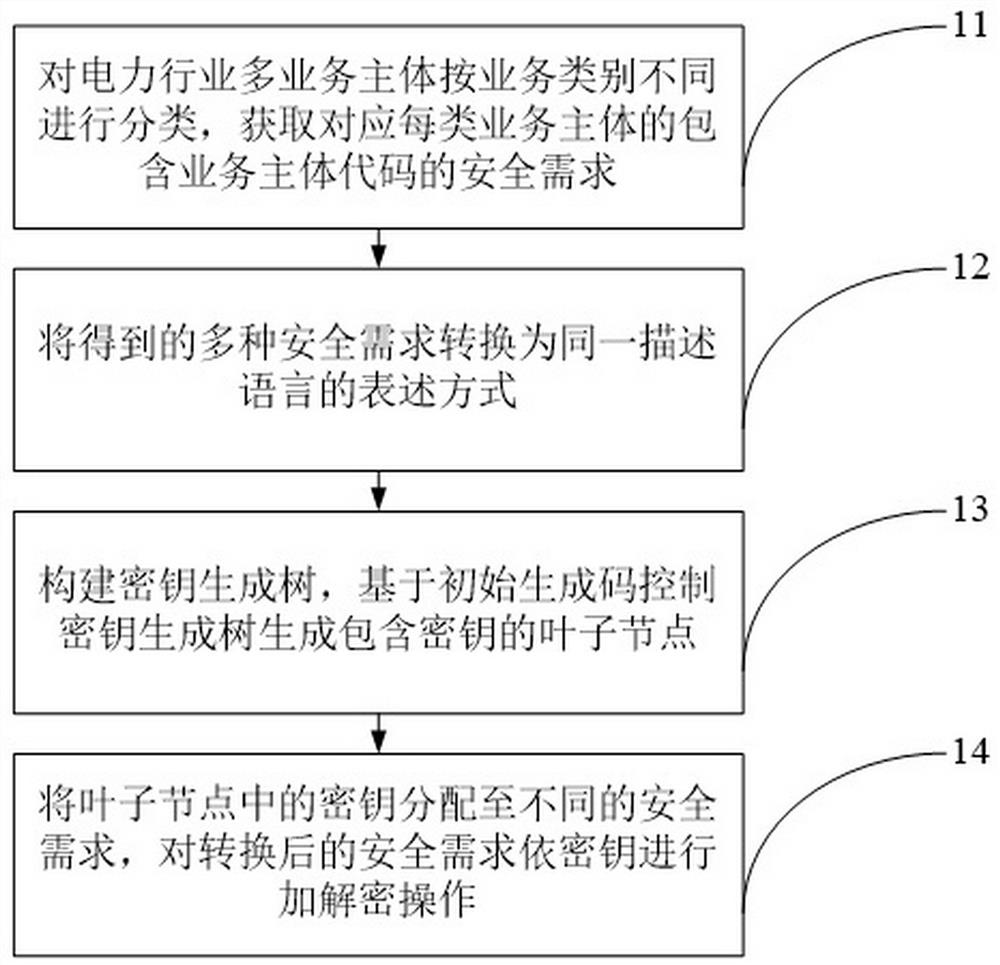
[0053] Specifically, the information security sharing method for multiple business entities in the electric power industry proposed in the embodiment of this application, such as figure 1 shown, including:
[0054] 11. Classify multiple business entities in the power industry according to different business categories, and obtain the security requirements corresponding to each type of business entity, including the business entity code.
[0055] 12. Transform the obtained multiple security requirements into an expression of the same description language.
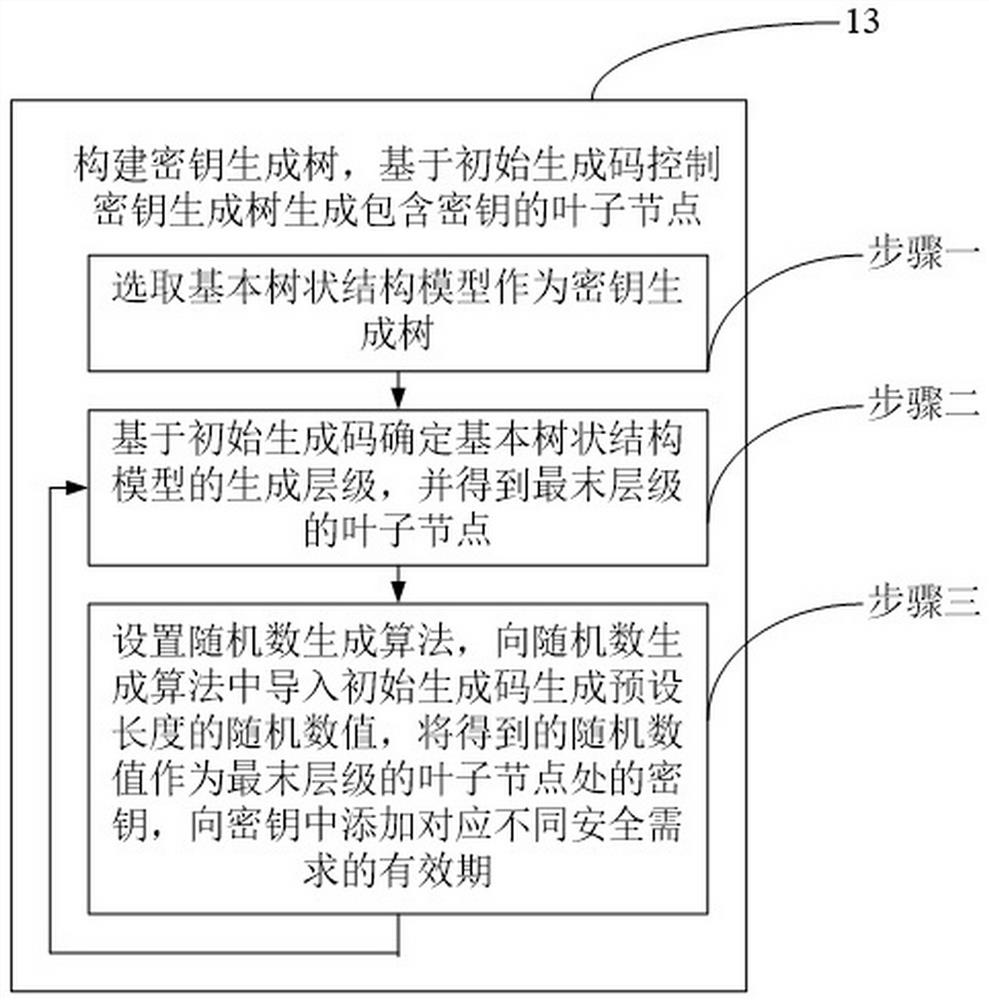
[0056] 13. Construct a key generation tree, and control the key generation tree to generate leaf nodes containing keys based on the initial generation code.
[0057] 14. Assign the keys in the leaf nodes to different security requirements, and perform encryption and decryption operations on the converted security requirements according to the keys.
[0058] Among them, the key in the leaf node and the leaf node share a val...
Embodiment 2
[0071] The foregoing embodiment 1 proposes a basic framework of an information security sharing method for multiple business entities in the electric power industry. On the basis of the obtained basic framework, this embodiment describes it in more detail.
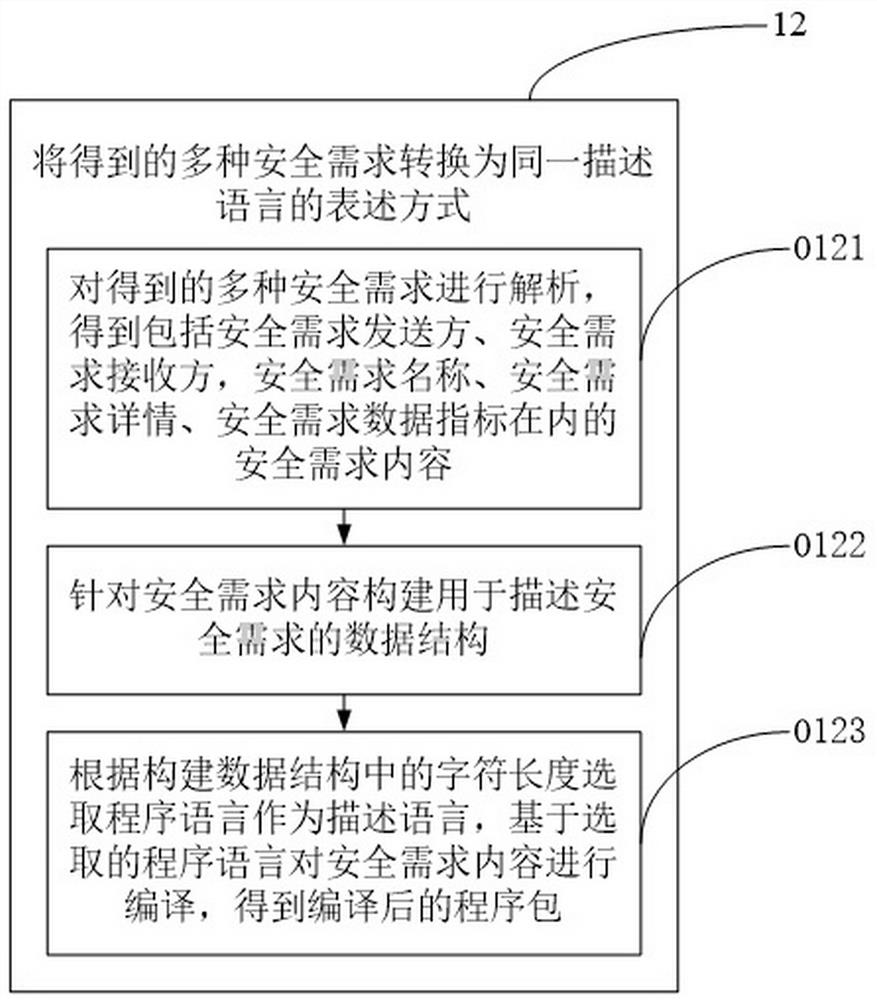
[0072] The aforementioned step 12 proposes the implementation content of converting the obtained multiple security requirements into the expression of the same description language, such as figure 2 shown, including:
[0073] 0121. Analyze the obtained multiple security requirements, and obtain the content of security requirements including security requirement sender, security requirement receiver, security requirement name, security requirement details, and security requirement data indicators.
[0074] 0122. Construct a data structure for describing the security requirements based on the content of the security requirements.
[0075] 0123. Select a programming language as the description language according to the char...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com