Malware sequence detection
A malware and sequence detection technology, applied to instruments, biological neural network models, calculations, etc., can solve problems such as discontinuous event sequences, production level problems, and difficult detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
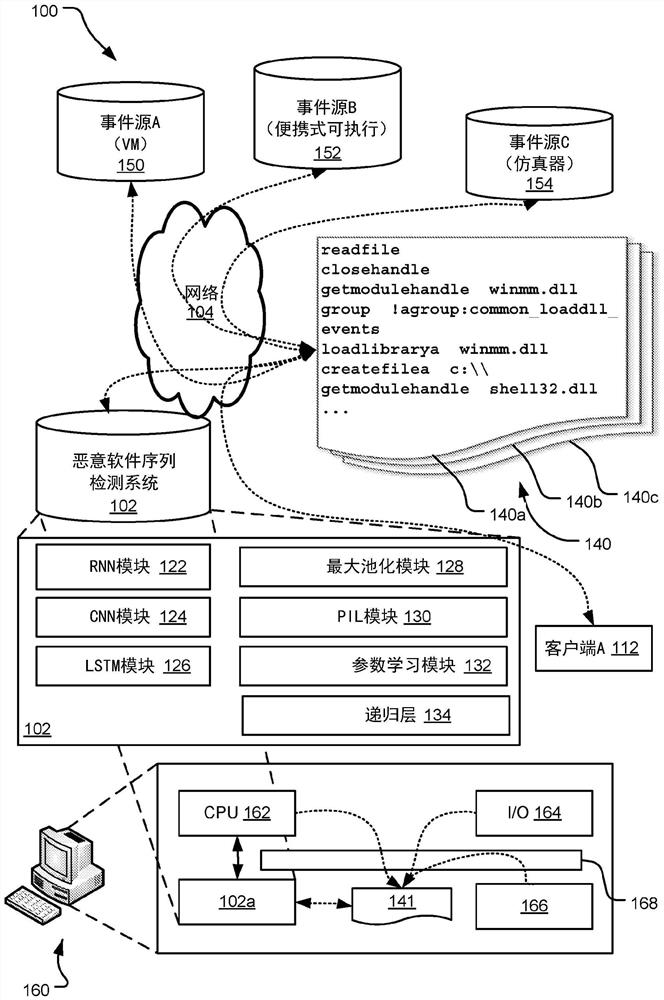
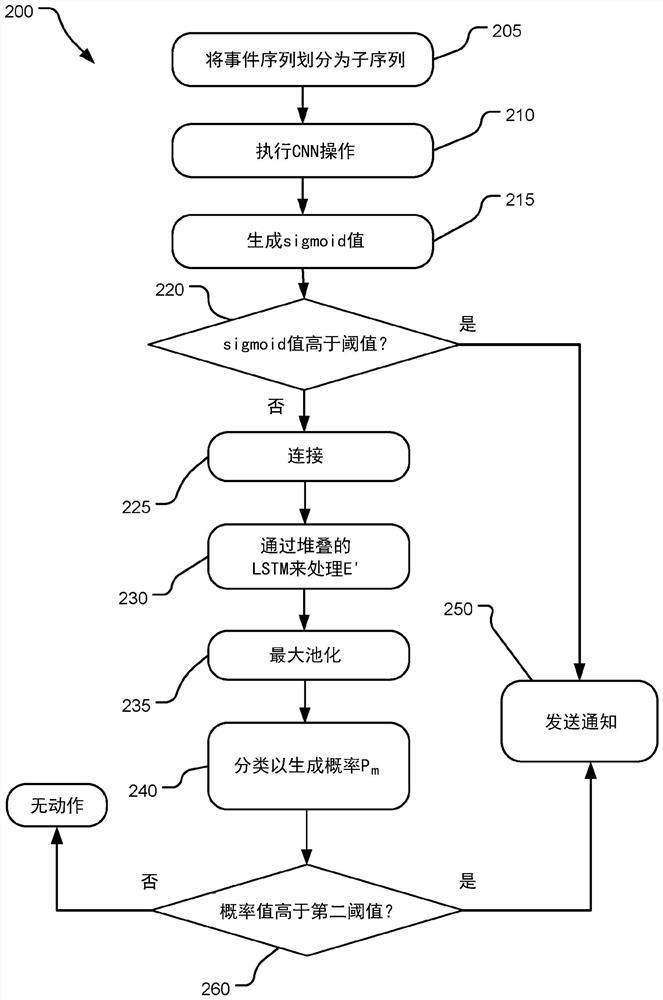
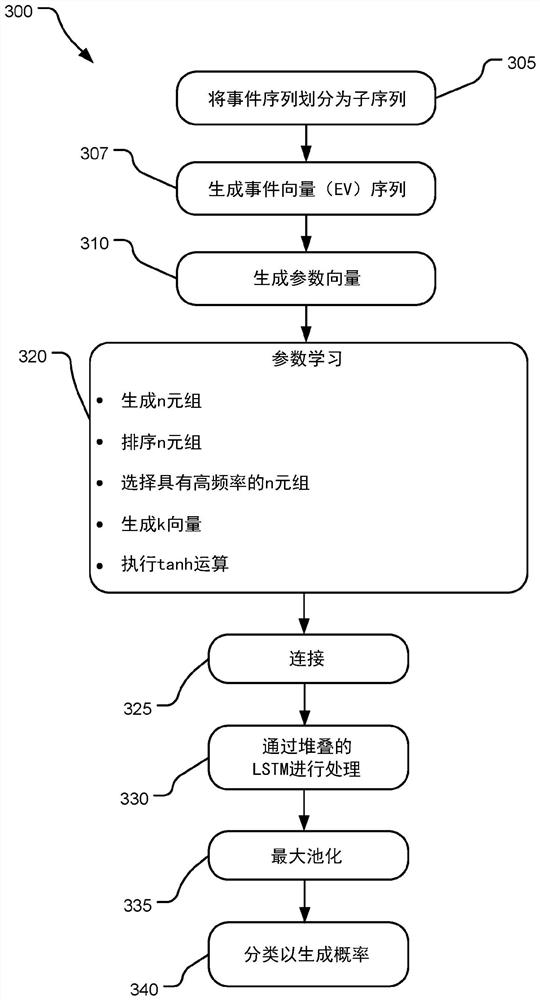
[0016] Malware (or malicious software) is an ongoing and growing problem in computer security. Malware is an act that enables software to perform a series of actions with negative intent, potentially causing serious production-level problems. As used herein, the term "malware" includes malicious files, processes, programs, instructions, data and / or software designed to damage, destroy or disable computers and computer systems, or to cause damage to computer users or computer user data. By embedding certain code snippets in regular software, it can successfully run the desired command without being detected by antivirus software. However, since certain commands must be run in a certain order relative to the malware's functionality, or in combination with some other sequence of malware instructions, for the malware to be effective, if the software can be executed in a secure environment and Malicious behavior can be detected during emulation and can be defended against. Howeve...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap