Internet malicious domain name detection method based on credibility
A domain name detection and credibility technology, applied in network data retrieval, network data indexing, and other database retrieval, etc., can solve problems such as difficulty in resisting new domain names, obvious degree of model degradation, and inability to obtain comprehensive and accurate results in domain name prediction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
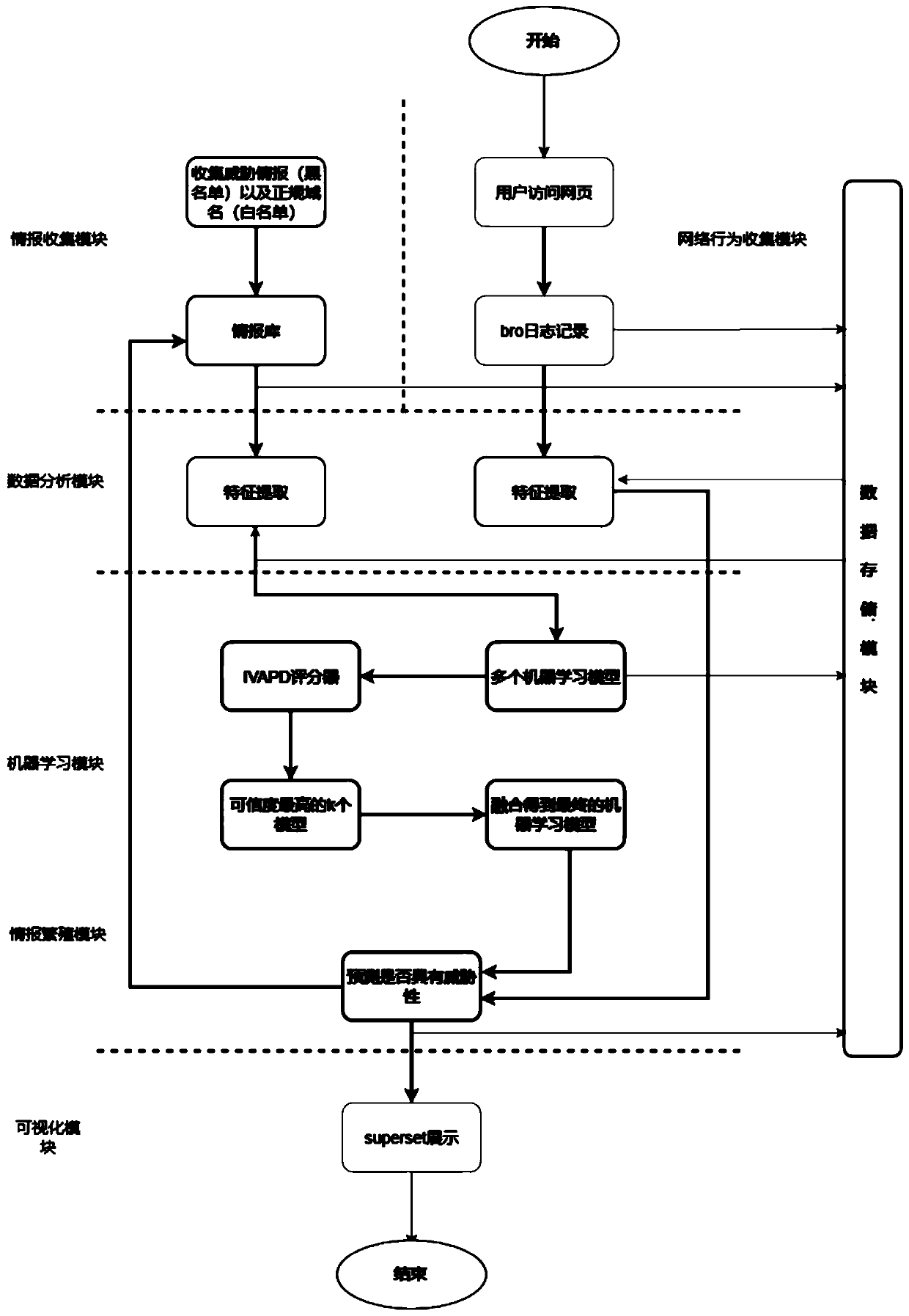
[0068] The present invention takes the realization of feature value modeling as an example for specific description. Any machine learning algorithm that builds a model by inputting the feature value of a domain name set can be used in this method. The method flow is as follows: figure 1 In this embodiment, four machine learning algorithms, XGBoost, LSTM, Bagging, and Support Vector Machine (SVM) are used as examples for illustration. The specific introduction is as follows:
[0069] XGBoost, full name eXtreme Gradient Boosting, is a boosting iterative algorithm and tree algorithm based on GBDT. It is mainly used in classification and regression. It has fast speed and good effect. It can calculate and process large amounts of data in parallel, supports custom loss functions, and can perform Regularization, highly flexible, capable of missing value processing and pruning, built-in cross-validation, and continuous training on the basis of existing models, etc., but the release time o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com