Data communication monitoring system and method
A technology of data communication and monitoring system, applied in the field of electronic communication, can solve the problem of occupying network traffic, etc., to achieve the effect of ensuring security, highlighting substantive features, and ensuring safe use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
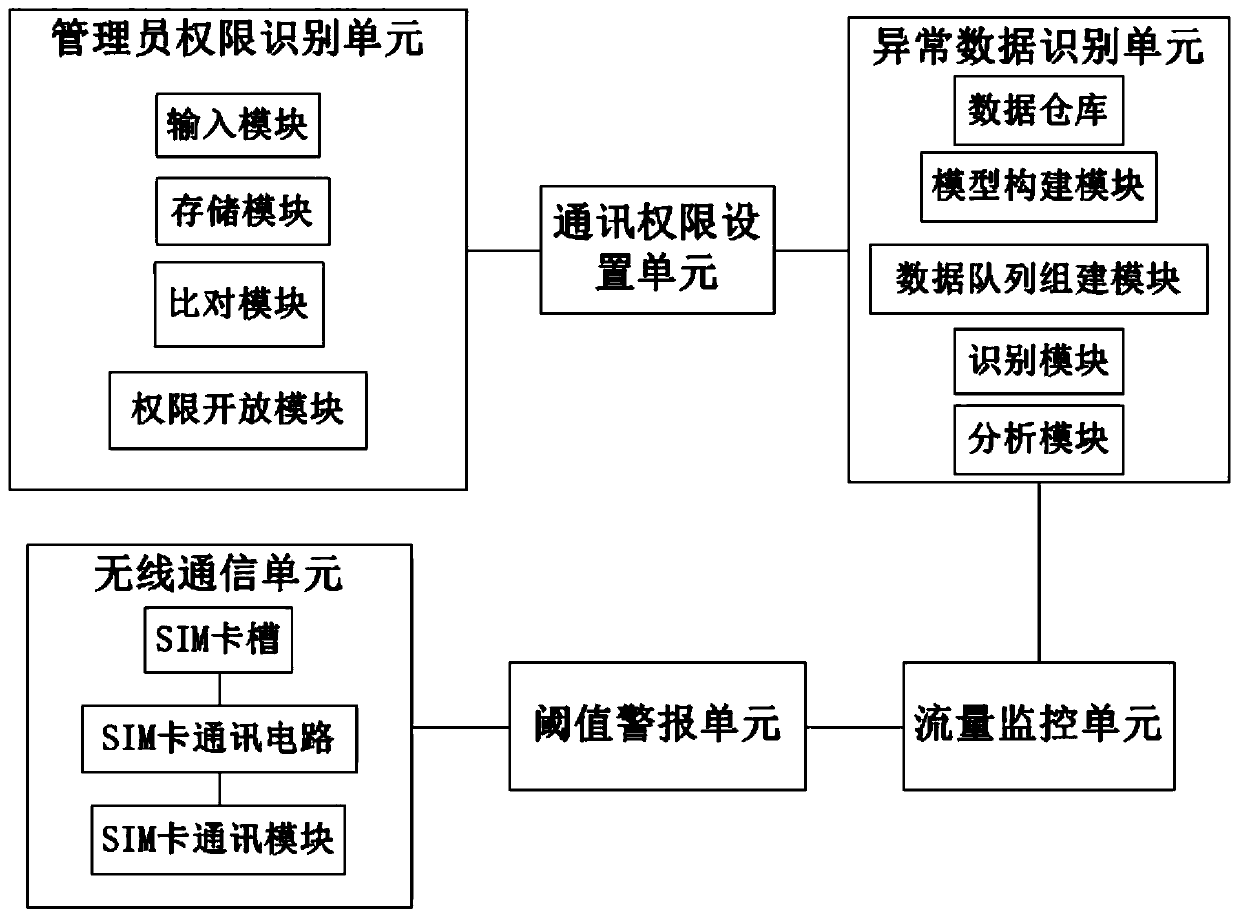
[0044] Such as figure 1 A data communication monitoring system is shown, including: an administrator authority identification unit, a communication authority setting unit, an abnormal data identification unit, a flow monitoring unit, a threshold alarm unit and a wireless communication unit;
[0045] The administrator authority identification unit is used to identify the identity of the system administrator and open the corresponding authority level to the administrator. The administrator authority authentication unit includes: an input module, a storage module, a comparison module and an authority opening module; the input module is used to input the administrator's identity information and identity verification code; the storage module is used to store the administrator's identity information , the corresponding identity verification code and authority level; the identity information and identity verification code of the administrator for multi-input by the comparison module ...
Embodiment 2
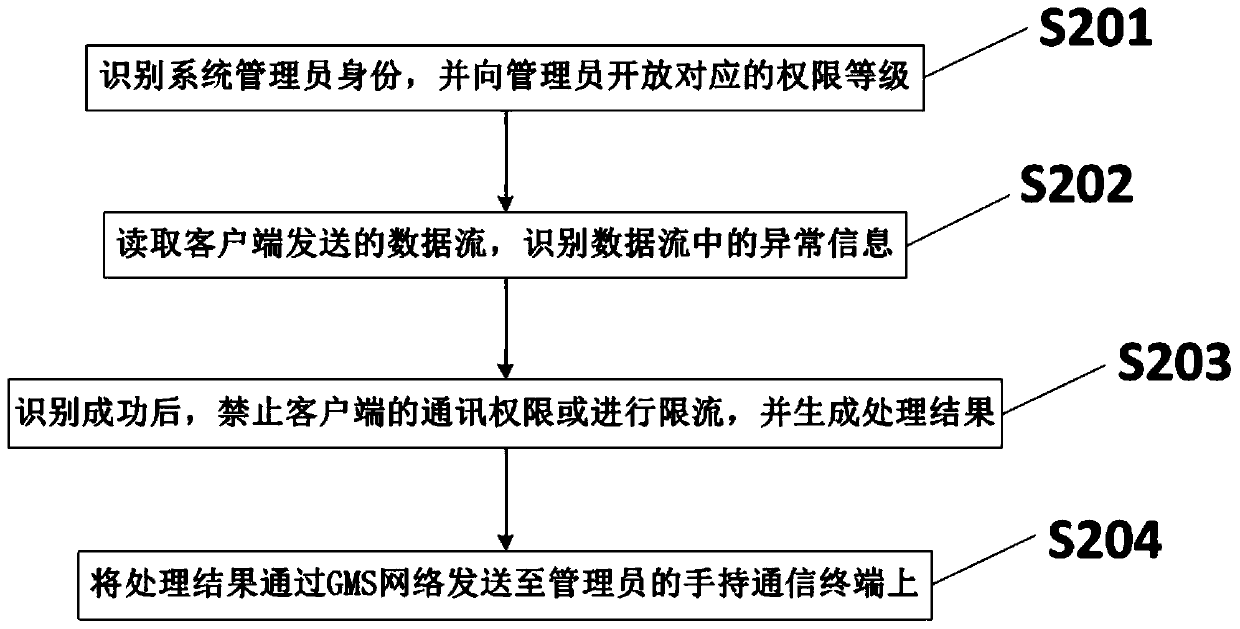
[0058] Correspondingly, such as figure 2 As shown, the present invention also discloses a data communication monitoring method, comprising the following steps:
[0059] S201: Identify the identity of the system administrator, and open the corresponding authority level to the administrator.
[0060] S202: Read the data stream sent by the client, and identify abnormal information in the data stream.
[0061] S203: After the identification is successful, the communication authority of the client is prohibited or the flow is limited, and a processing result is generated.
[0062] S204: Send the processing result to the administrator's handheld communication terminal through the GMS network.
Embodiment 3
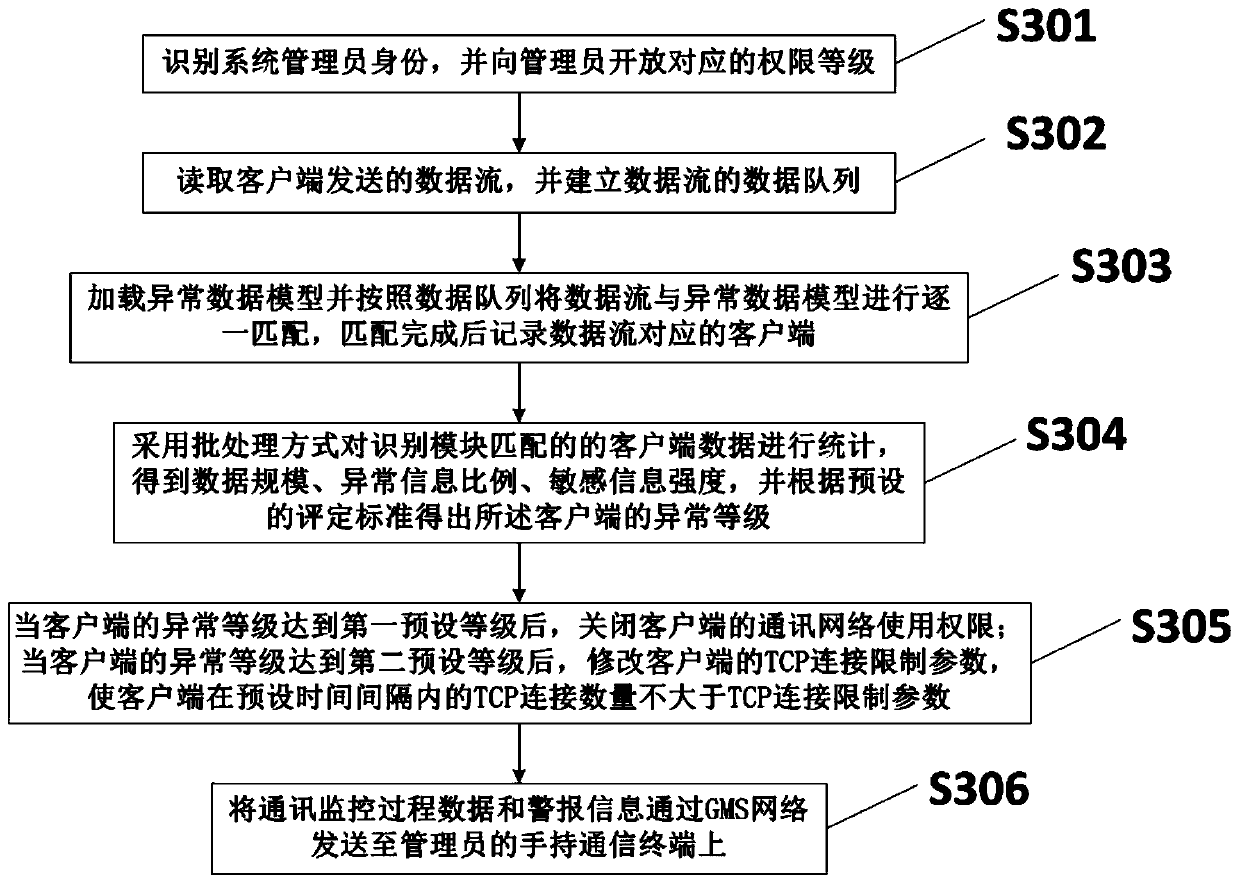
[0064] On the basis of the above examples, if image 3 As shown, this embodiment also discloses a data communication monitoring method, including the following steps:
[0065] S301: Identify the identity of the system administrator, and open the corresponding authority level to the administrator.
[0066] S302: Read the data flow sent by the client, and establish a data queue of the data flow.
[0067] S303: Load the abnormal data model and match the data flow with the abnormal data model one by one according to the data queue, and record the client corresponding to the data flow after the matching is completed.
[0068] S304: Use batch processing to count the client data matched by the identification module, obtain the data size, abnormal information ratio, and sensitive information intensity, and obtain the abnormal level of the client according to the preset evaluation standard.
[0069] S305: When the abnormality level of the client reaches the first preset level, close ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com