Active trusted computing method and active trusted computing system based on TrustZone sub-core asynchronous execution
A technology of trusted computing and asynchronous execution, applied in computing, execution paradigm, protection of internal/peripheral computer components, etc., can solve the problem of not considering trusted measurement and control issues, and achieve the effect of preventing interruptions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
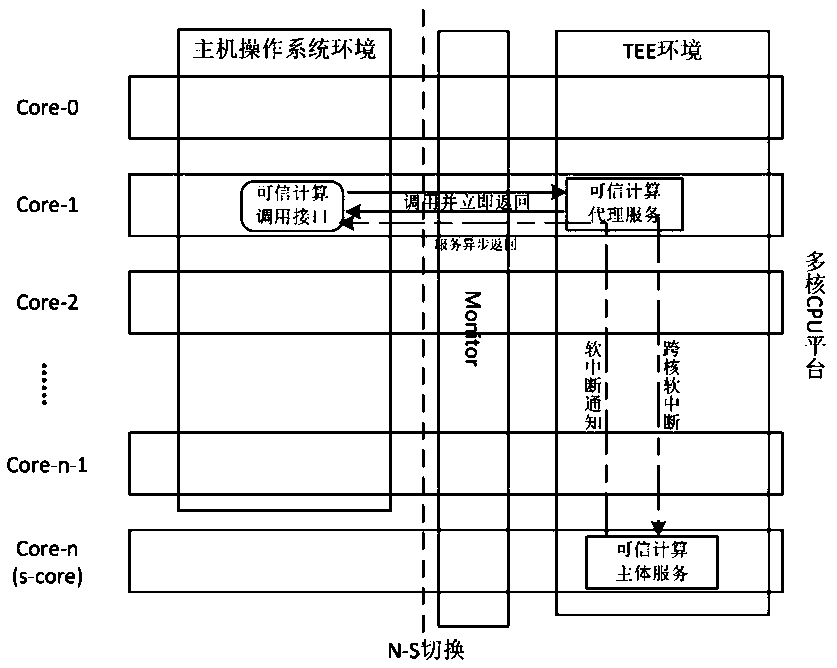
[0032] Such as figure 1 As shown, the implementation steps of the active trusted computing method based on TrustZone sub-core asynchronous execution in this embodiment include:
[0033] 1) Configure and start the active trusted computing service after the computer is powered on, and establish a static trusted chain between the host loading module and the host operating system through a static measurement mechanism during system startup. The active trusted computing service includes trusted computing Main body service, trusted computing proxy service and trusted computing call interface, the trusted computing main body service and trusted computing proxy service are mapped to the running environment TEE, the trusted computing calling interface and the host system are mapped to the running environment In REE, the operating environment TEE and the operating environment REE are two operating environments in which software and hardware resources are isolated from each other based o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com