Analysis method, device and system for quickly adapting to protocol change
A technology of protocol analysis and analysis method, which is applied in the analysis field of rapid adaptation to protocol changes, and can solve the problems of unfavorable application end quickly adapting to protocol changes, not disclosing the differences of network protocol processors in detail, and complicated configuration process, etc. Achieve the effect of improving development efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
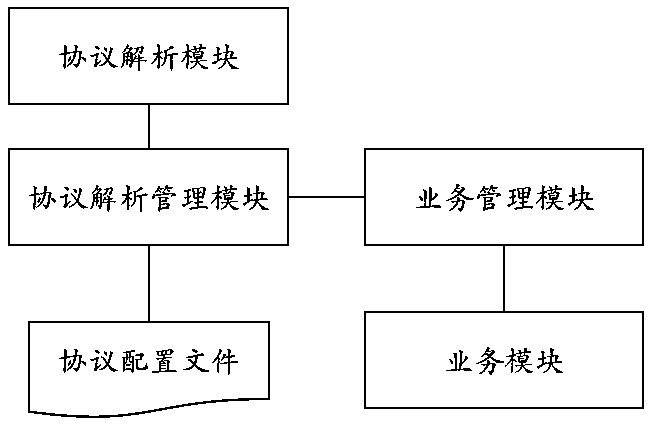
[0042] Embodiment 1: as figure 2 As shown, the present invention is applied to network protocols to keep stable, for example, not limited to protocols such as TCP, UDP, HTTP, etc., in the event of protocol changes, a fast-adapting protocol change analysis system or device includes the following modules:
[0043]Protocol configuration file: This file describes the format of the protocol. According to the definition of the protocol, the protocol configuration file has different description methods. For example, if the content is transmitted in binary format, and different fields occupy different lengths, the example of the protocol configuration file is:
[0044] Field Name Occupied space length (bytes) type of data Message ID 2 value object name 2 text weight 1 value Appearance 1000 image (large object)
[0045] The message format defined by delimiter and formatted text (such as XML) is used as a protocol configuration file in...
Embodiment 2
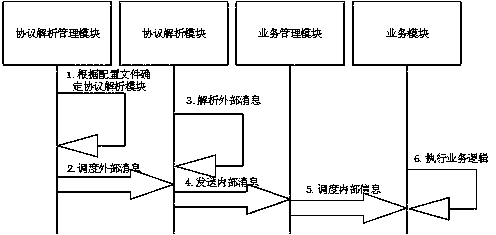
[0050] Embodiment 2: After the service user receives the external message sent by the service provider, the protocol analysis management module analyzes the external message, such as image 3 As shown, the following is the analysis process:
[0051] The protocol analysis management module analyzes the external message, and sends the external message to the protocol analysis module according to the judgment after analysis;
[0052] The protocol analysis module converts external messages into internal messages according to the specification;
[0053] The protocol analysis module sends internal messages to the business management module;
[0054] The business management module manages one or more business modules, and different business modules need to use different internal messages to complete different business functions. With a properly designed business module, when the protocol of the service provider changes, the change of the business module can be minimized. For exampl...
Embodiment 3
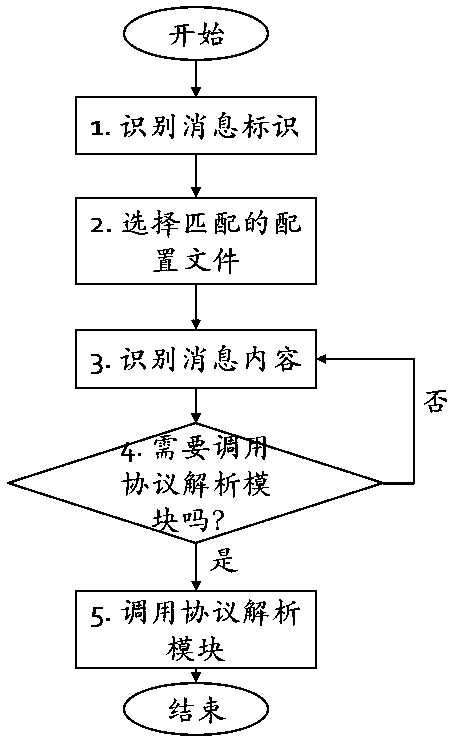
[0056] Embodiment 3: as Figure 5 As shown, plan the configuration file according to the overall situation of the business. For example: a subsystem uses a configuration file, which contains all message format definitions of the subsystem; a configuration file can also be defined for a message, of course, if there are many messages, the number of configuration files is relatively large.
[0057] After the protocol analysis management module obtains the external message from the communication module, it first identifies the message ID of the external message. Usually, this is an agreed behavior in a protocol system, that is, extracts the message ID according to the predetermined protocol, and then finds the message ID according to the message ID. Corresponding protocol configuration file for subsequent processing.
[0058] The advantage of multi-protocol configuration files is that when the protocol is updated, only relevant configuration files need to be modified, and other c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com