Safety verification method and device
A safety verification and safety verification technology, which is applied in the field of safety verification methods and devices, can solve problems such as complex technical solutions, low safety factors, and large investment, so as to reduce the probability of hacker attacks, improve safety, and ensure simplicity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
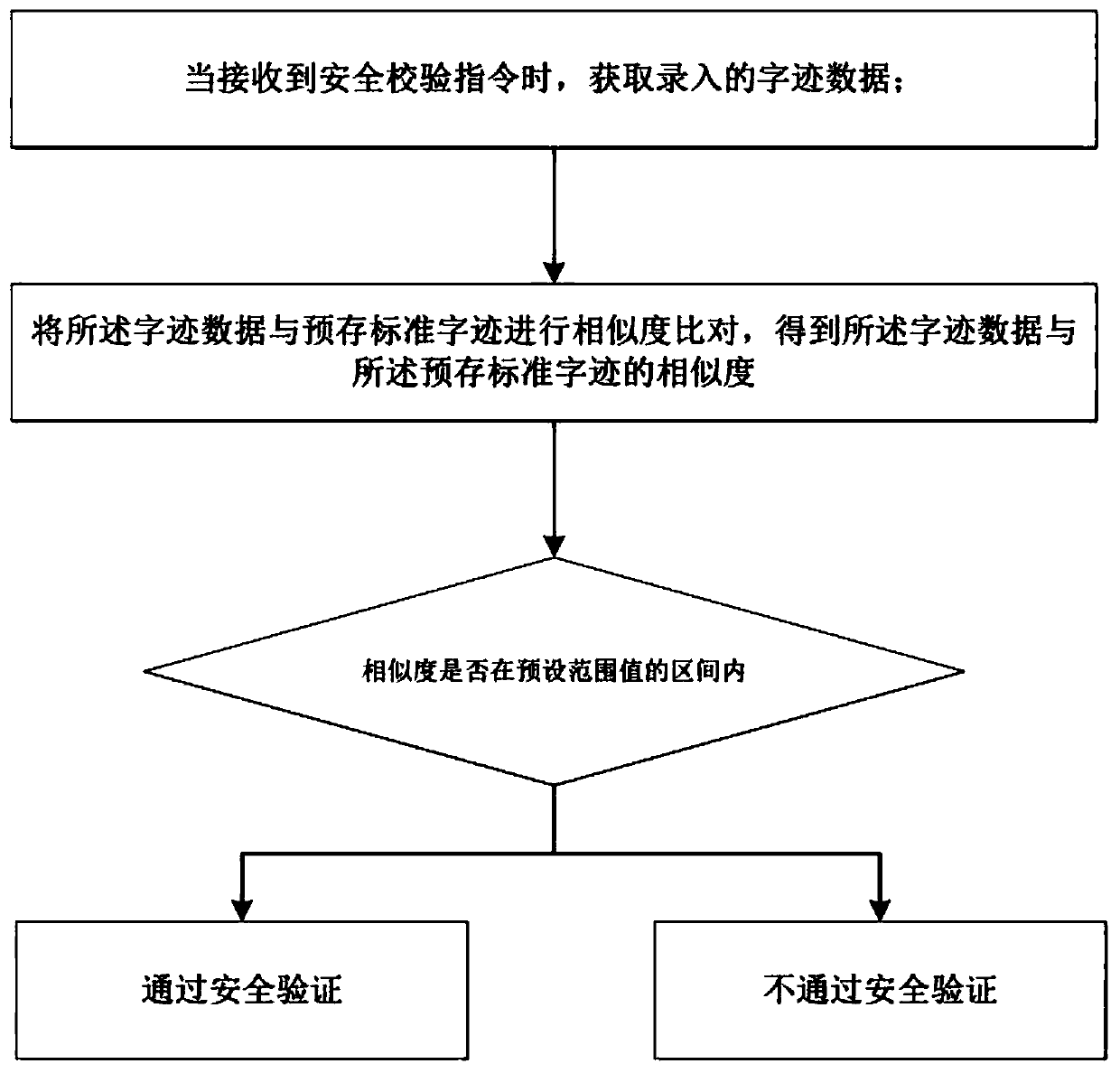
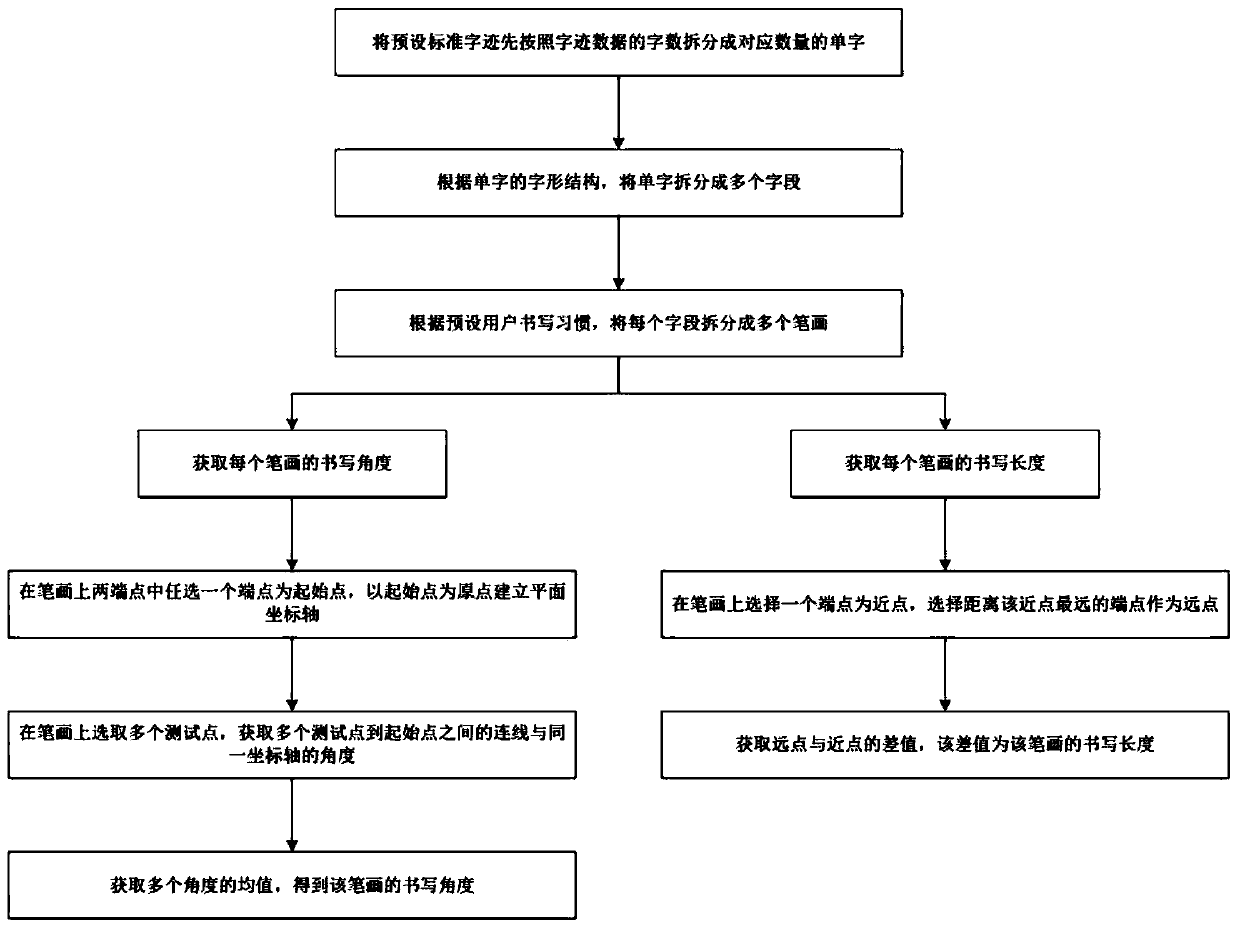
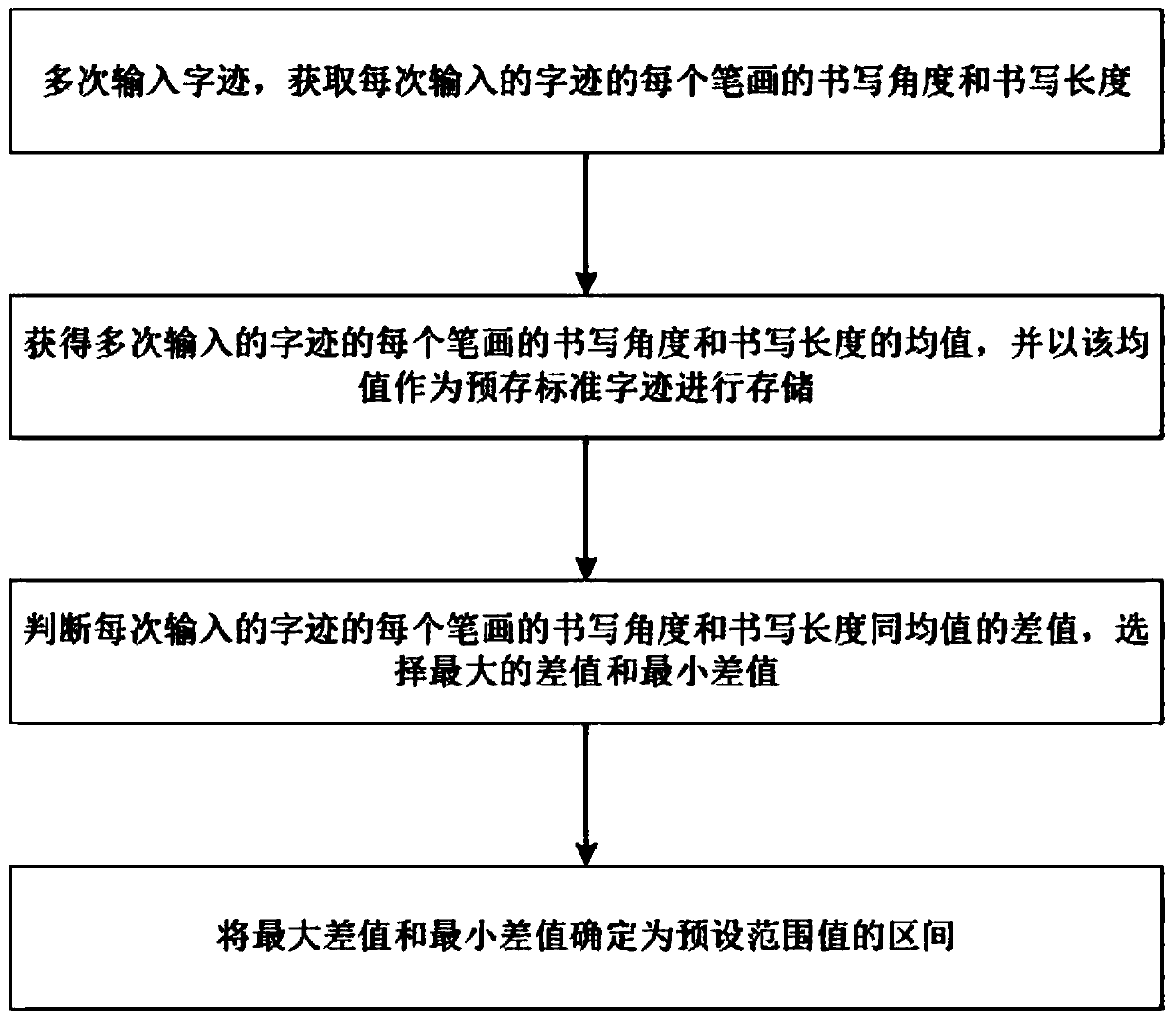
[0039] In order to ensure the security of mobile services and user information, etc., when a user accesses mobile services or user information through a terminal, for example, when a user accesses a mobile terminal or an approval file in the ERP system, it is necessary to Perform security check operations. For example, when a user requests to access a mobile terminal or an approval document in the ERP system, a security verification command is triggered and handwriting data is entered. In this embodiment, the main body that executes the method for handwriting safety verification of the present invention is preferably a mobile terminal, and in other embodiments of the present invention, it can also be an application program in a mobile terminal, a server of a webpage loaded in a mobile terminal, a mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com