Method and system for docking user with application based on universal transfer service
A technology for transferring servers and users, applied in transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
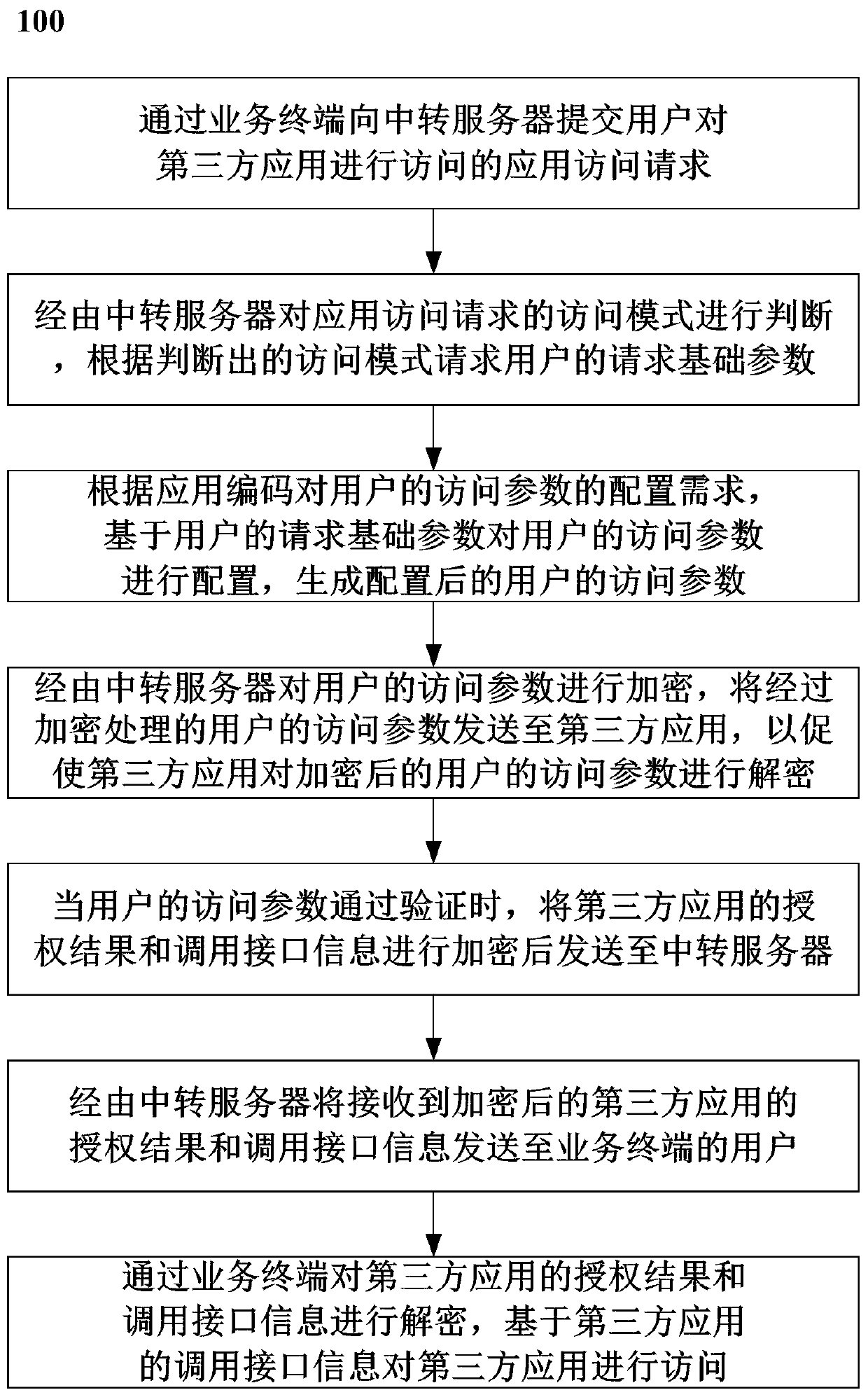
[0052] Example 1 A user A is an enterprise user of a company in region A, and is using the application XYZ provided by the platform. The specific steps are as follows:
[0053] 1. User A runs the platform and clicks to apply XYZ;
[0054] 2. The platform packages and encrypts user A's basic information and application code, and sends it to the transit server, requesting to call application XYZ;
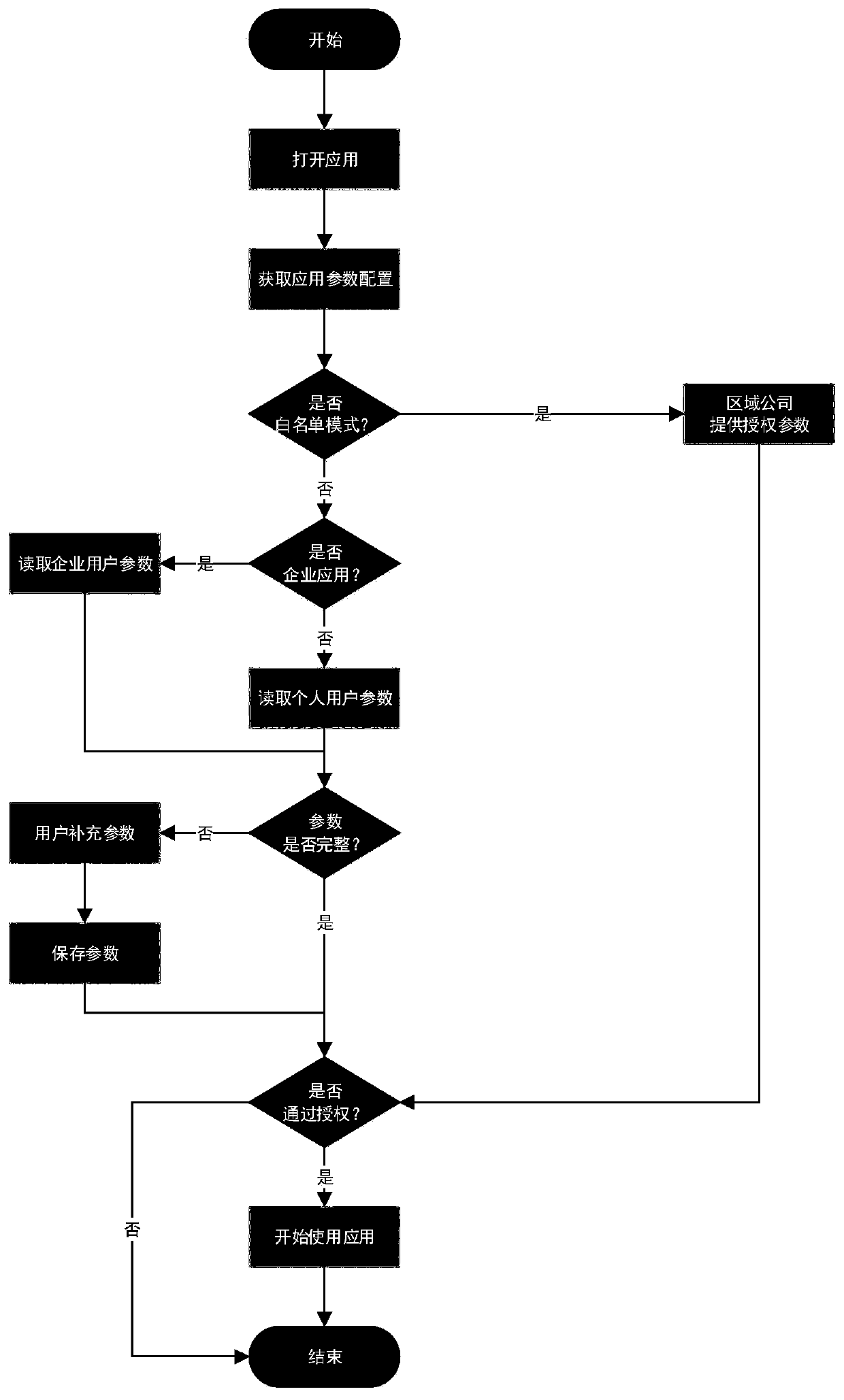
[0055] 3. The transfer server recognizes that the application type of application XYZ is a personal application, and the mobile phone number information is required for application calling. The basic information of user A packaged by the platform only includes enterprise user information such as enterprise name, enterprise tax number, etc. If personal information is missing, the entry is provided by the user A supplements personal user information, and the transfer server saves the information for subsequent use;
[0056] 4. The transfer server encrypts the complete parameters and se...
example 2
[0060] Example 2 A user B is an enterprise user of a company in region B, and is using the application ADC provided by the platform. The specific steps are as follows:
[0061] 1. User B runs the platform and clicks Apply ADC;
[0062] 2. The platform packages and encrypts user B's basic information and application code, and sends it to the transit server, requesting to call the application ADC;
[0063] 3. The transfer server recognizes that the application type of the application ADC is a personal application. The application call requires mobile phone number information, date of birth, and the basic information of user B packaged on the platform only includes corporate user information such as the company name and corporate tax ID. If personal information is missing, the transfer The server has saved the relevant information and automatically supplemented the missing parameters;
[0064] 4. The transfer server encrypts the complete parameters and sends them to the third-pa...
example 3
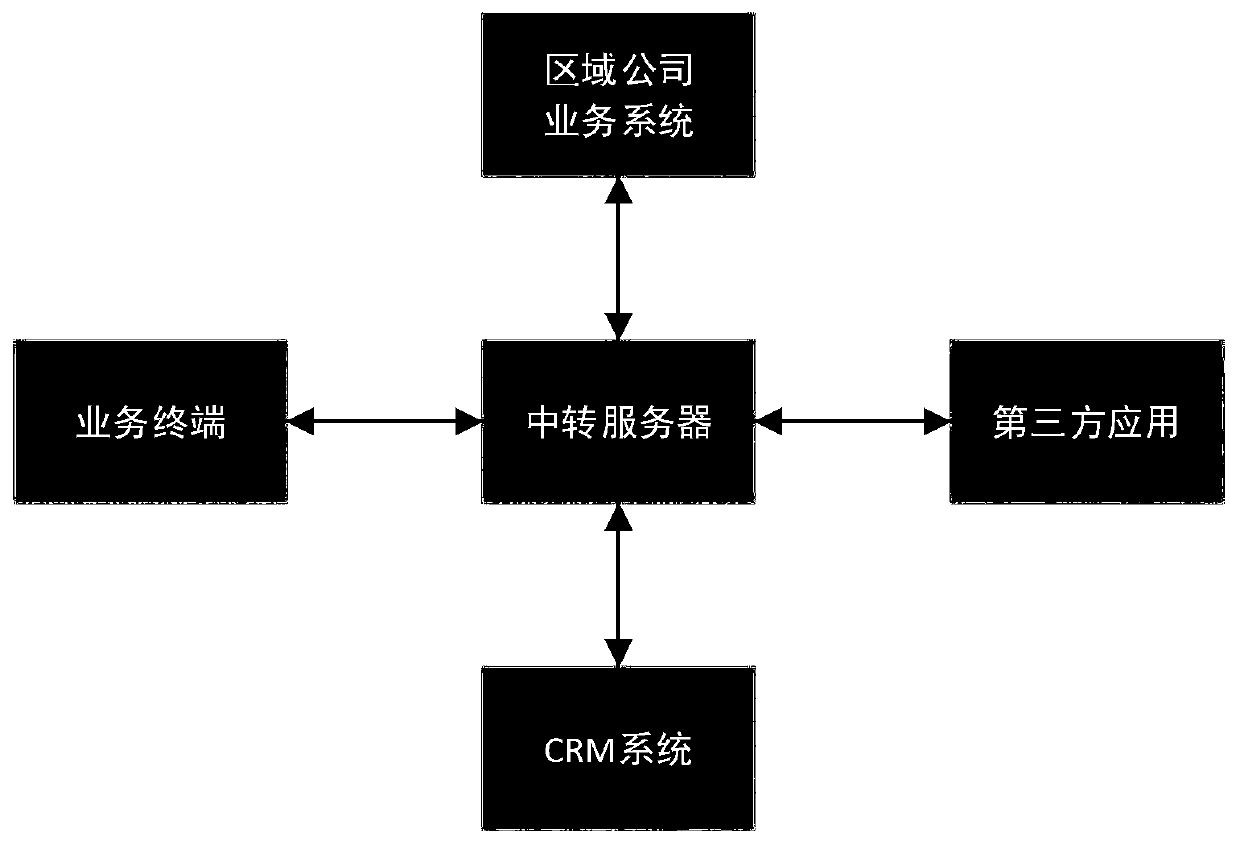
[0068] Example 3 A user C is a potential user of regional company C, and the regional company wants to promote the application of DEF to him. The specific steps are as follows:
[0069] 1. The company in region C collected the personal information of user C and entered it into the business system;
[0070] 2. User C scans the code and applies the DEF QR code;
[0071] 3. The platform packages and encrypts user C's basic information and application code, and sends it to the transit server, requesting to call the application DEF;
[0072] 4. The transfer server recognizes that the application type of the application DEF is a personal application, and the access mode is a whitelist access mode, and the transfer server requests the required parameters from the business system of the regional company;
[0073] 5. The transfer server encrypts the complete parameters and sends them to the third-party application;
[0074] 6. The third-party application performs authorization verifi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com