Personal harmful call detection method and device based on streaming data graph and readable medium
A technology of call detection and streaming data, which is applied in monitoring/monitoring/test arrangement, automatic exchange, telephone communication, etc. It can solve the problem of low accuracy of fraudulent gangs, failure to achieve expected results, and inability to accurately analyze fraudulent gangs, etc. problem, achieve real-time and accuracy improvement, and increase the effect of analysis success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
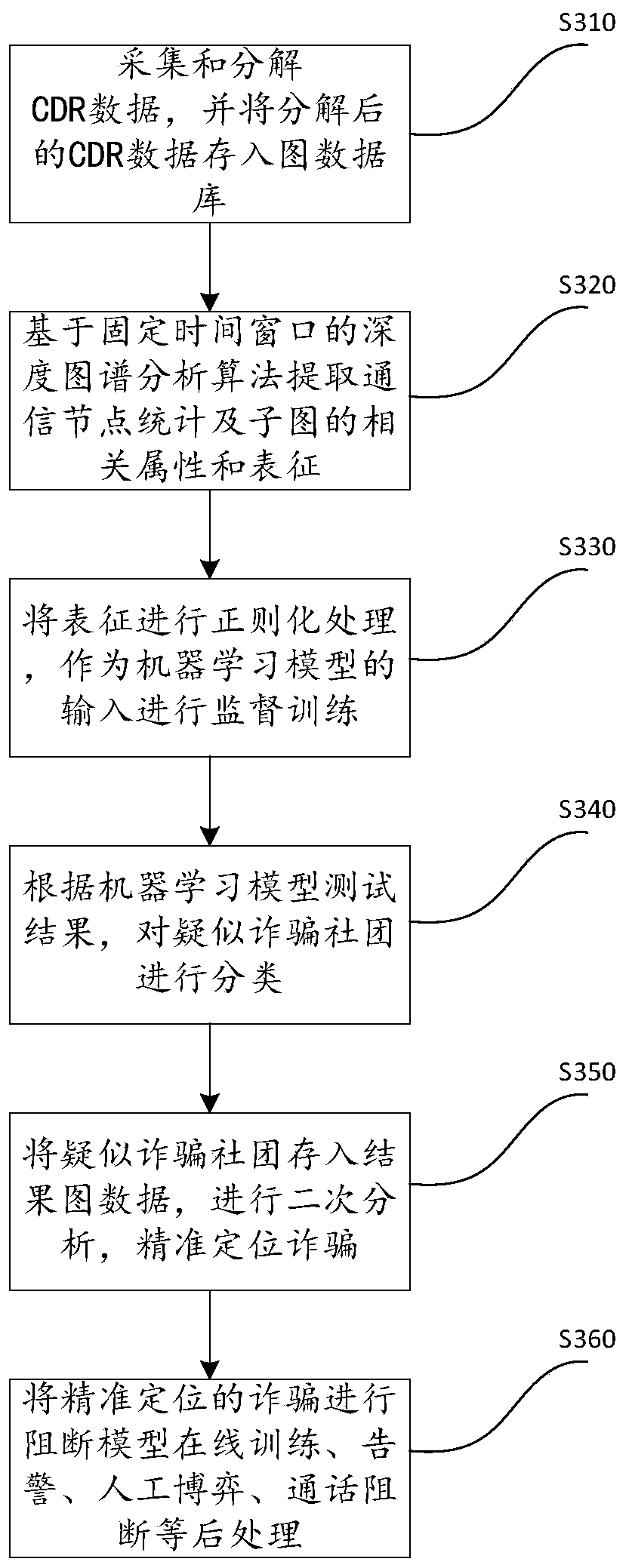
[0021] This part will describe the specific embodiment of the present invention in detail, and the preferred embodiment of the present invention is shown in the accompanying drawings. Each technical feature and overall technical solution of the invention, but it should not be understood as a limitation on the protection scope of the present invention.
[0022] In the description of the present invention, several means one or more, and multiple means two or more. Greater than, less than, exceeding, etc. are understood as not including the original number, and above, below, within, etc. are understood as including the original number. If the description of the first and second is only for the purpose of distinguishing the technical features, it cannot be understood as indicating or implying the relative importance or implicitly indicating the number of the indicated technical features or implicitly indicating the order of the indicated technical features relation.
[0023] In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com