Trusted LBS service protocol implementation method based on privacy protection
A service agreement and privacy protection technology, applied in the field of car networking security, which can solve the problems of group member key leakage and excessive permissions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0131] In order to clearly illustrate the technical features of the solution, the solution will be described below through specific implementation modes.
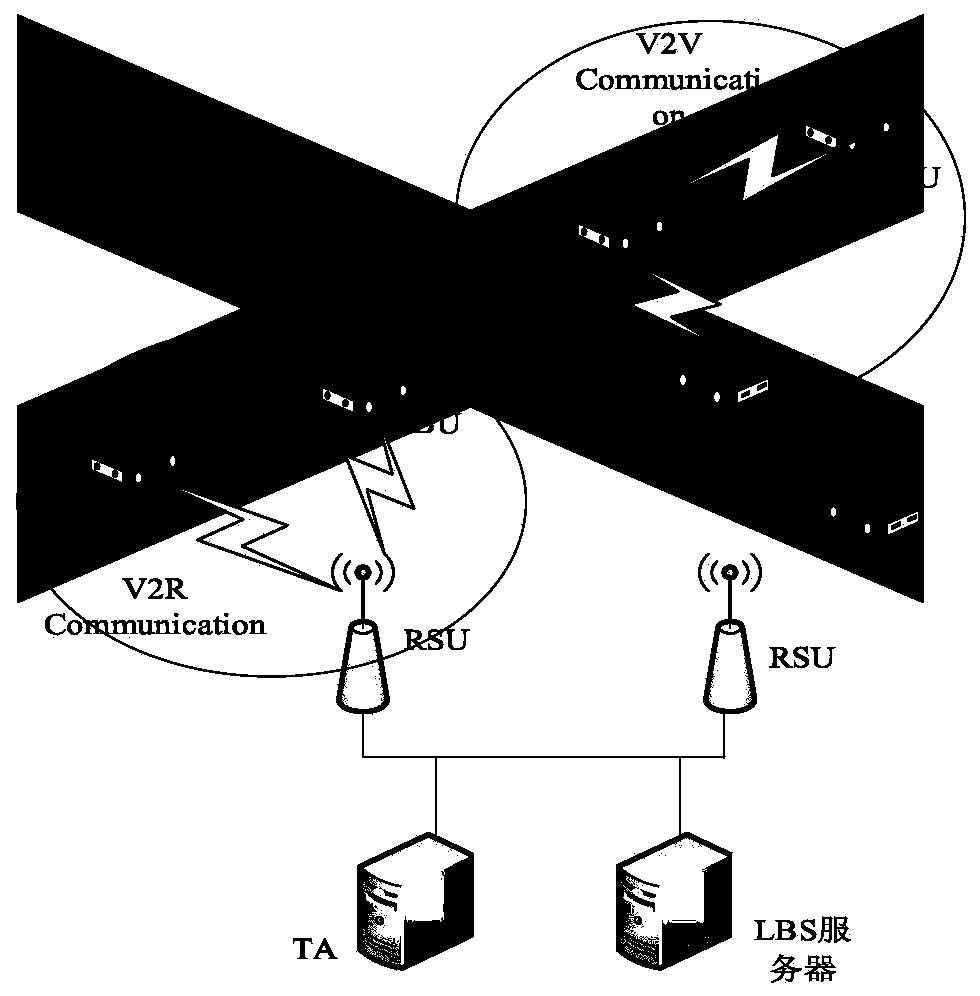
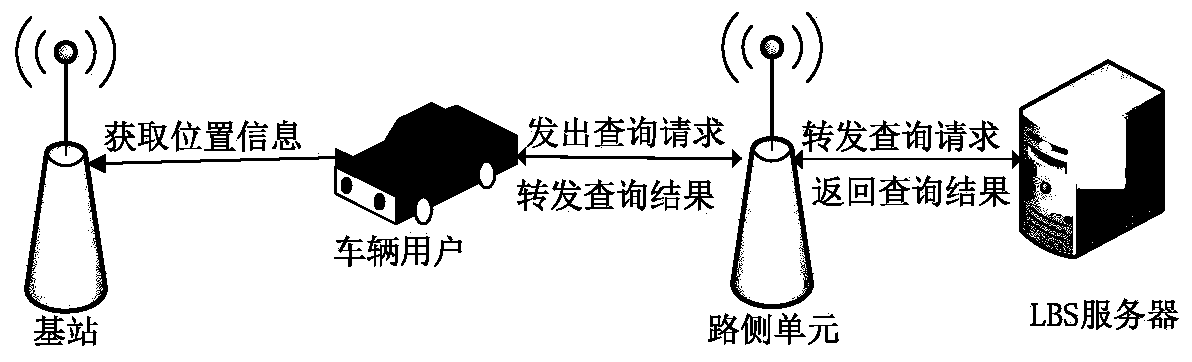
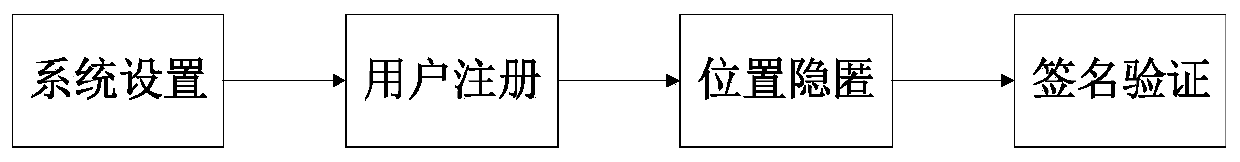
[0132] see Figure 1 to Figure 6 , the present invention is: a kind of trusted LBS service protocol implementation method based on privacy protection comprises the following steps:
[0133] Step 1, system settings:
[0134] The key generation center (PKG) deployed in the traffic authority (TA) constructs the addition group and the same factorial group, and then uses the ring signature technology to prepare for system initialization, and publishes the public parameters for the ring signature.
[0135] Step 2, user registration:
[0136] All users, including vehicles, roadside units and LBS servers, must register with the local traffic authority before joining the Internet of Vehicles. The traffic authority is responsible for checking and verifying the user's identity information, and registering for it after passing the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com