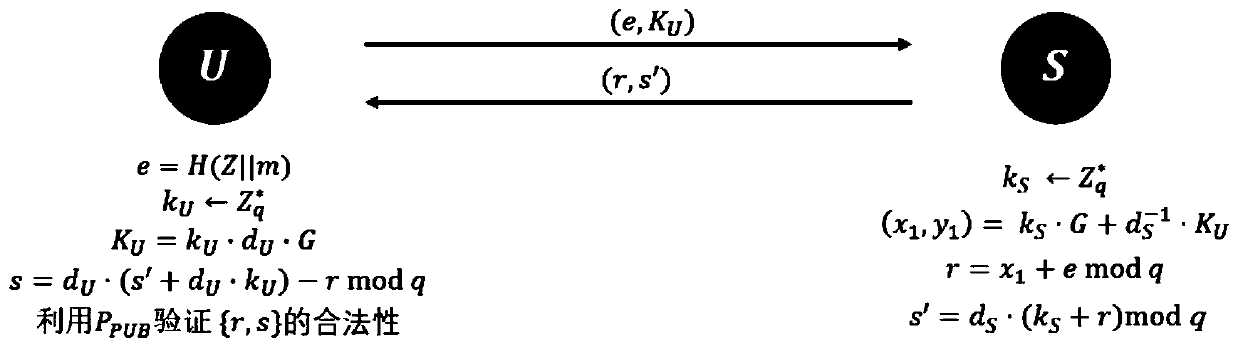SM2 two-party collaborative signature method suitable for lightweight client and medium
A lightweight client and client technology, applied in the field of information security, can solve the problems of loss, theft of signature keys, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0042] The present invention proposes a scheme for two parties to jointly generate SM2 digital signatures. In this solution, when generating the SM2 digital signature, two parties participate together, one is the client U and the other is the server S. At this stage, the client U and the server S use their partial private keys to collaboratively generate the SM2 signature on the message m. The following steps should be implemented:
[0043] 1).U in Select the third random number k U As part of the temporary private key, calculate e=H(Z||m) and the first part of the temporary public key K U =k U ·D U ·G. Finally U sends (e, K U ) To S.
[0044] 2).S in Select the fourth random number k S As part of the private key, calculate the temporary public key Calculate the first part of the signature r=x 1 +e mod q, generate intermediate variable s′=d S ·(K S +r)mod q. Finally, S returns (r, s′) to U.
[0045] 3).U calculates the second part signature s=d U ·(S′+d U ·K U )-rmod q, use P ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com