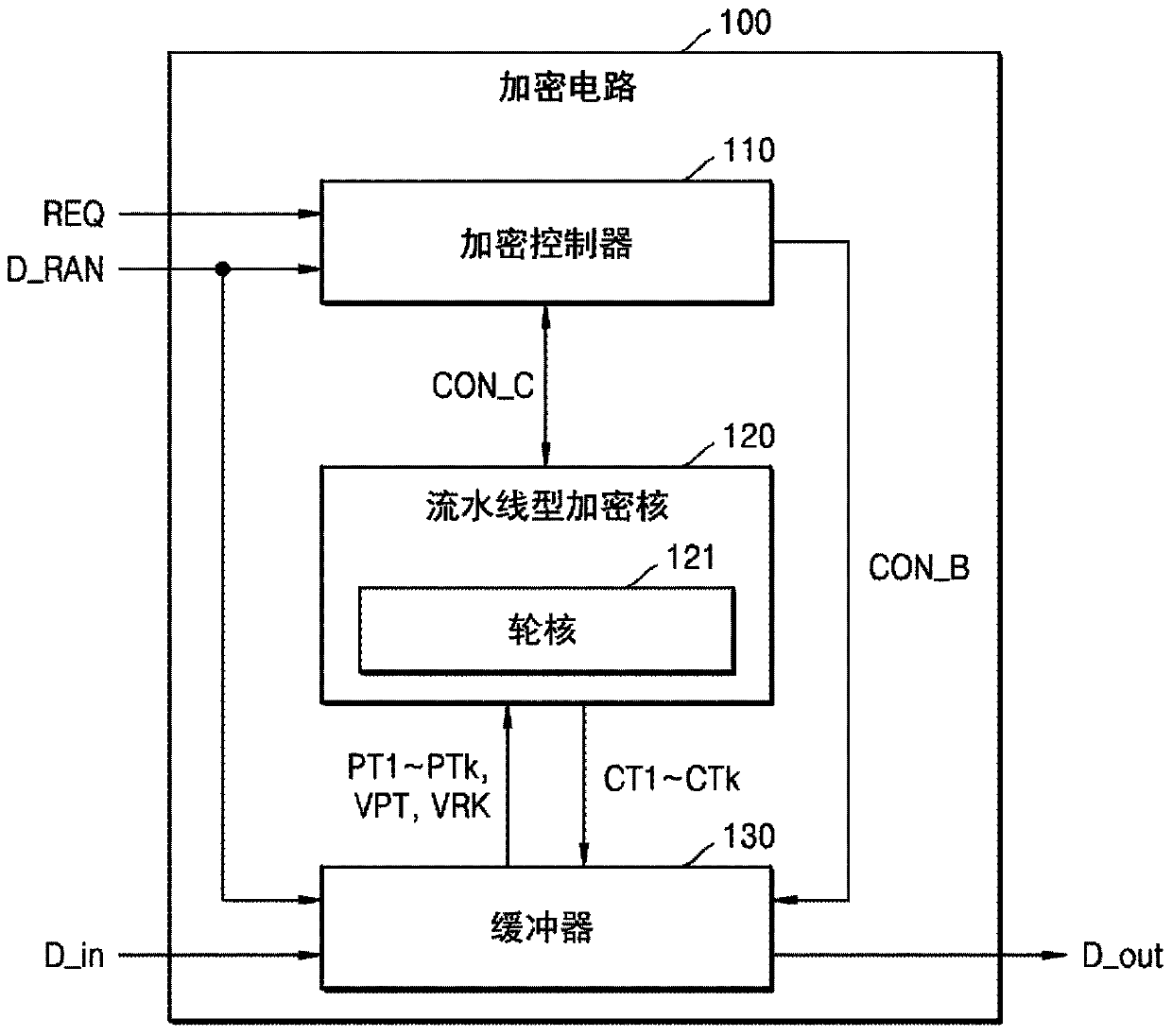
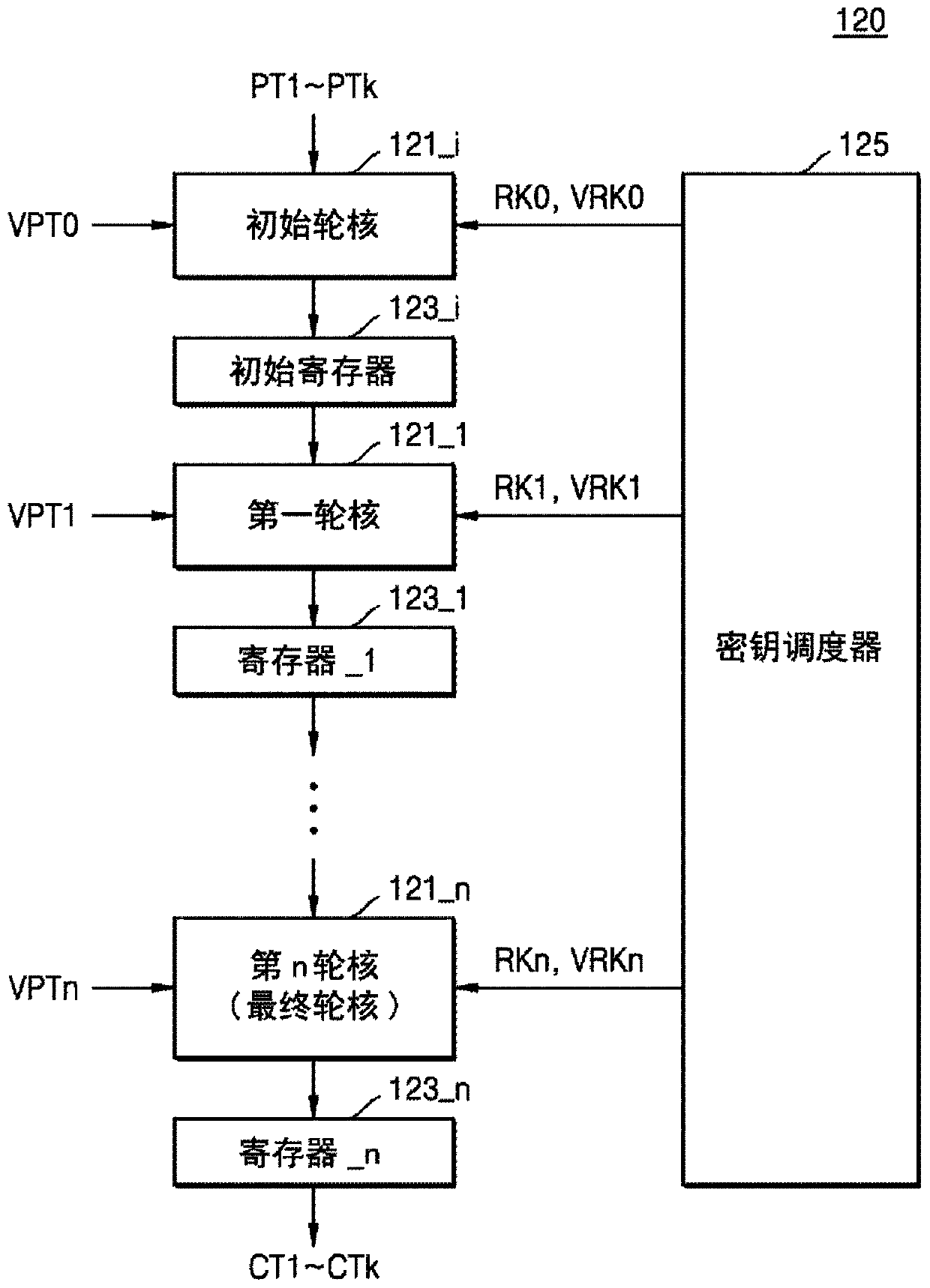
Encryption circuit for performing virtual encryption operation
A technology of encryption circuit and virtual operation, applied in countermeasures against encryption mechanism, encryption device with shift register/memory, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Hereinafter, embodiments will be described in detail with reference to the accompanying drawings.
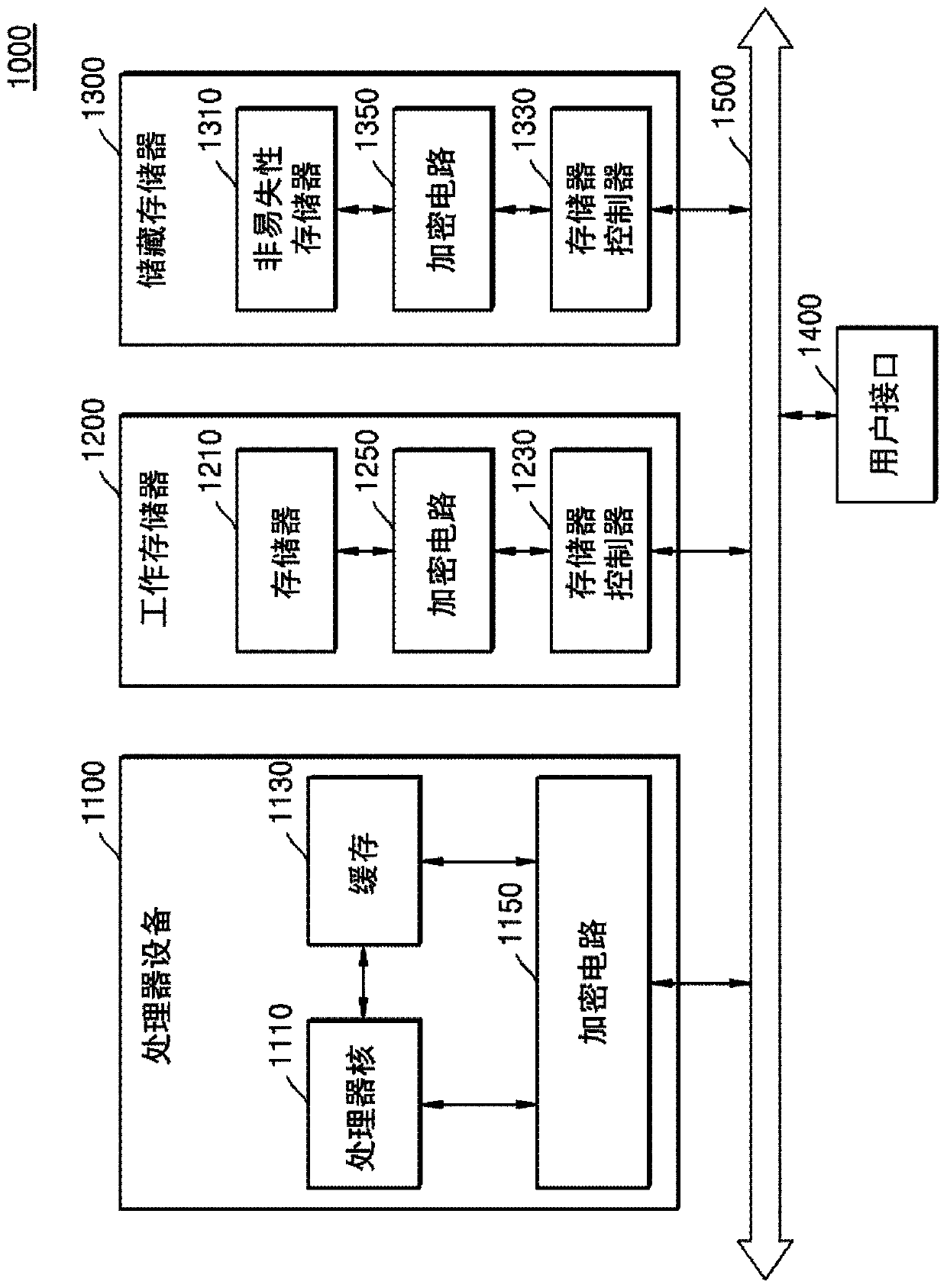
[0023] figure 1 is a block diagram of a computing device 1000 according to an embodiment. figure 1 is a block diagram illustrating a computing device 1000 including an electronic device and an encryption circuit according to an embodiment. In one embodiment, the computing device 1000 may include a processor device 1100 , a working memory 1200 , a storage memory 1300 , a user interface 1400 and a bus 1500 .
[0024] For example, computing device 1000 may be one of various electronic devices, such as a desktop computer, laptop computer, tablet computer, workstation, server, digital television (TV), video game console, smartphone, and wearable device, but the implementation Examples are not limited to this.
[0025] The processor device 1100 may control the overall operation of the computing device 1000 . Processor device 1100 may be configured to perform various arithme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com