Application layer DDoS attack detection and defense method based on multiple feature entropies
An attack detection, multi-feature technology, applied in electrical components, transmission systems, etc., can solve problems such as single dimension and no consideration of resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
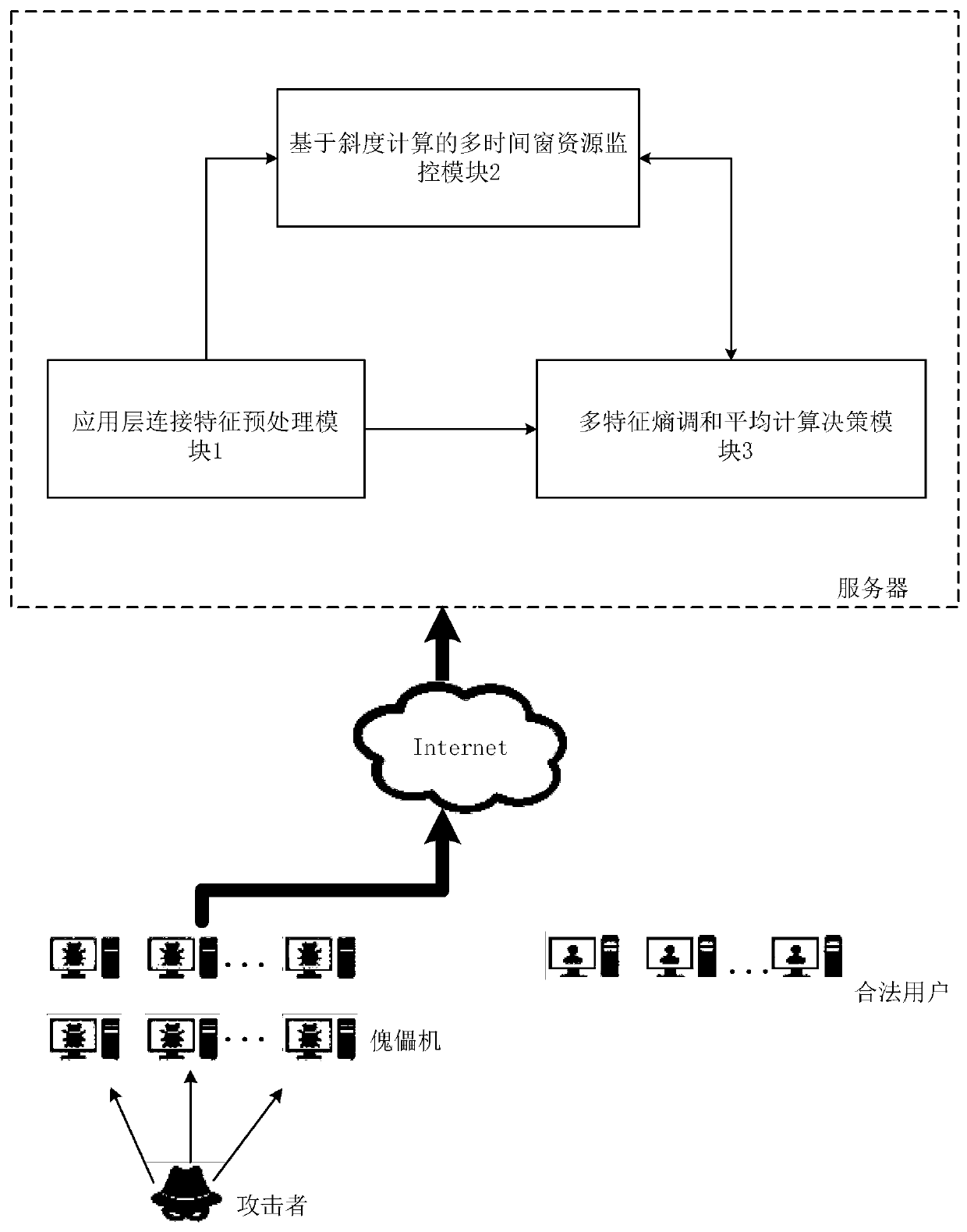
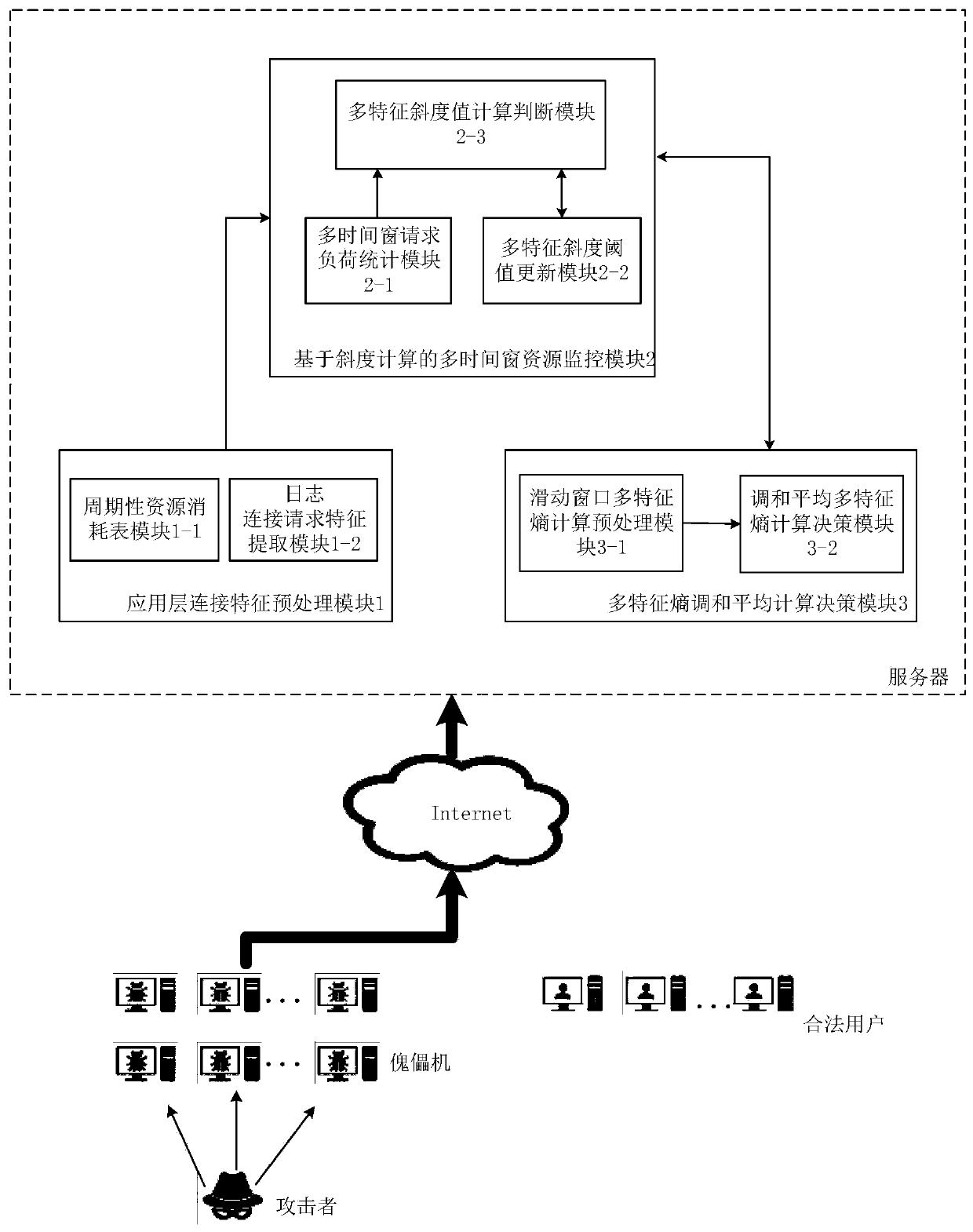
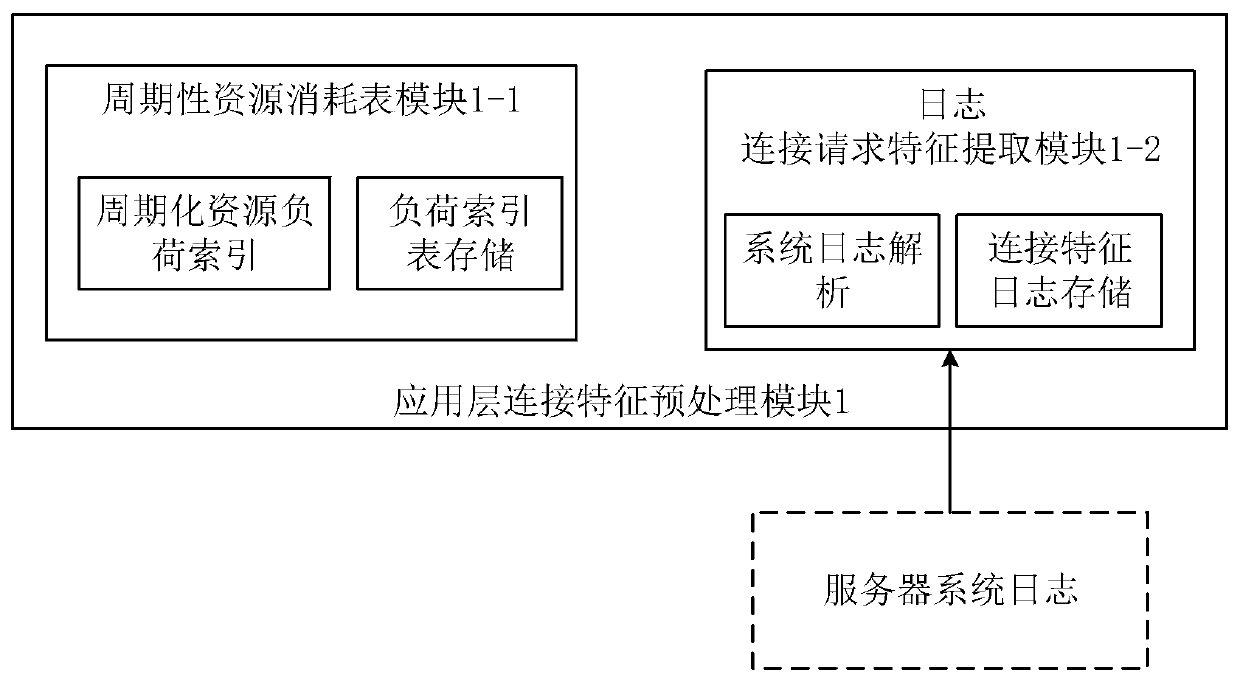
[0040] Based on the self-designed server connection request load slope algorithm and the self-designed multi-feature entropy harmonic average algorithm, the present invention provides a network server-oriented application layer DDoS attack detection method, and the present invention can be run on the server as a separate module, As a normal business independent of the server, at the same time monitor the consumption of server memory resources and CPU resources by the application layer connection request in real time, and make a preliminary decision based on the dynamic threshold whether there is an application layer DDoS attack, and on this basis, through the connection characteristics in the The final decision is made by reconciling and averaging multi-feature entropy values within a multi-window time, so as to effectively detect application-l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com