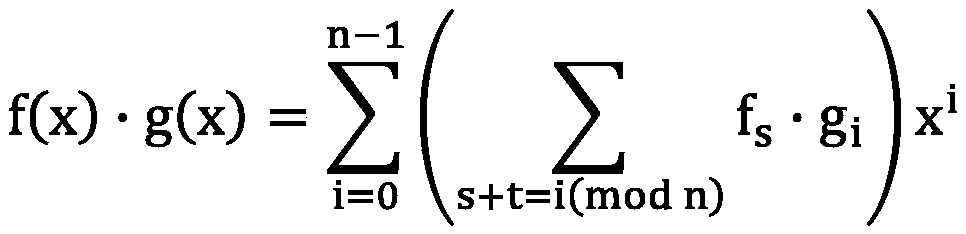NTRU encryption method based on R-LWE and security certification method thereof
An encryption method and security technology, applied in the field of NTRU encryption method and its security proof based on R-LWE, can solve the problems of lack of security, key generation algorithm lattice attack, etc., to improve security and avoid lattice attacks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The technical solution of the present invention will be described in further non-limiting detail below in conjunction with preferred embodiments.
[0046] A kind of NTRU encryption method based on R-LWE, it comprises the following steps:
[0047] 1. Define parameters:
[0048] Define n as a power of 2 and n≥8;
[0049] define p = 2;
[0050] Define q as a prime number, q≥5 and q≤poly(n), q=1mod 2n to ensure that ((x n +1) modq) has n different linear factors;
[0051] The operation result of mod q is limited to Inside, mod(x n The operation result of +1) is a polynomial whose degree does not exceed n-1;
[0052] definition ring For elements in the ring R
[0053] f(x)=f 0 +f 1 x+…+f n-1 x n-1 , g(x)=g 0 +g 1 x+…+g n-1 x n-1 and k∈Z, define the operation as:
[0054] k·f(x)=kf 0 +kf 1 x+…+kf n-1 x n-1
[0055]
[0056] 2. Key pair generation:
[0057] In the ring R=Z(x) / (x n +1) Obtain the private key through Gaussian sampling, the specific s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com