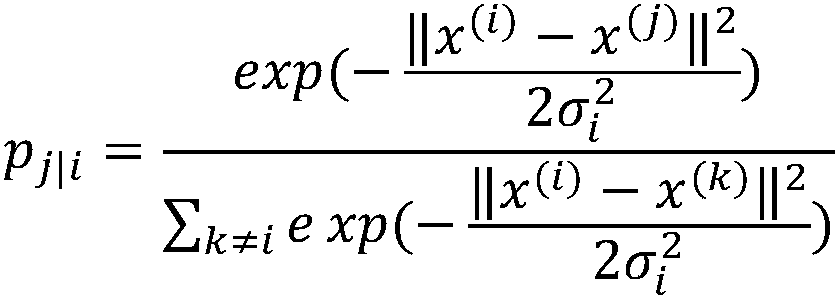Malicious code family clustering method and system
A malicious code and clustering method technology, applied in character and pattern recognition, instruments, computing, etc., can solve the problems of consuming computing resources, huge amount of calculation, and large value range, so as to increase the accuracy of clustering and reduce the number of values. range of values, effect of reducing computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
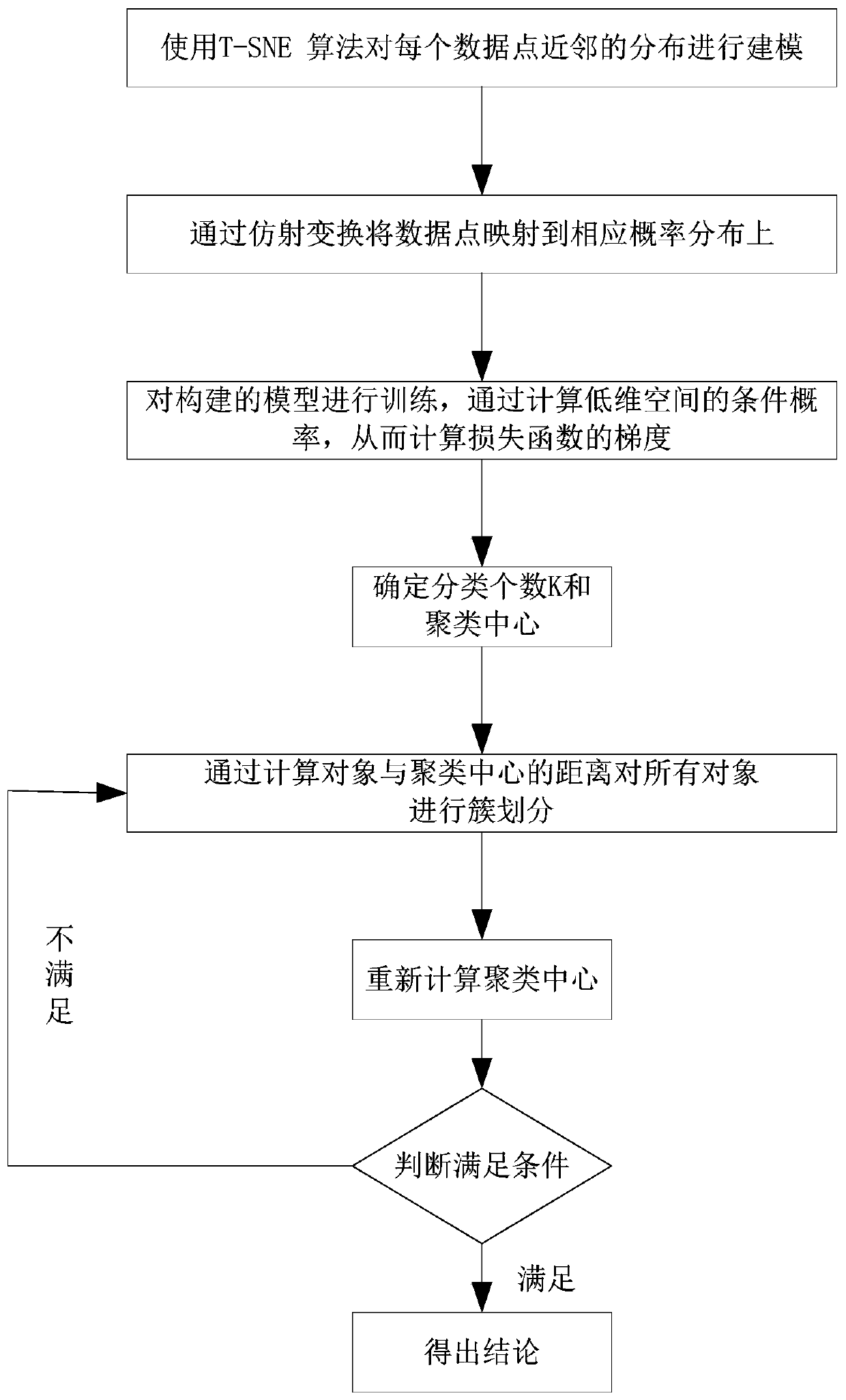
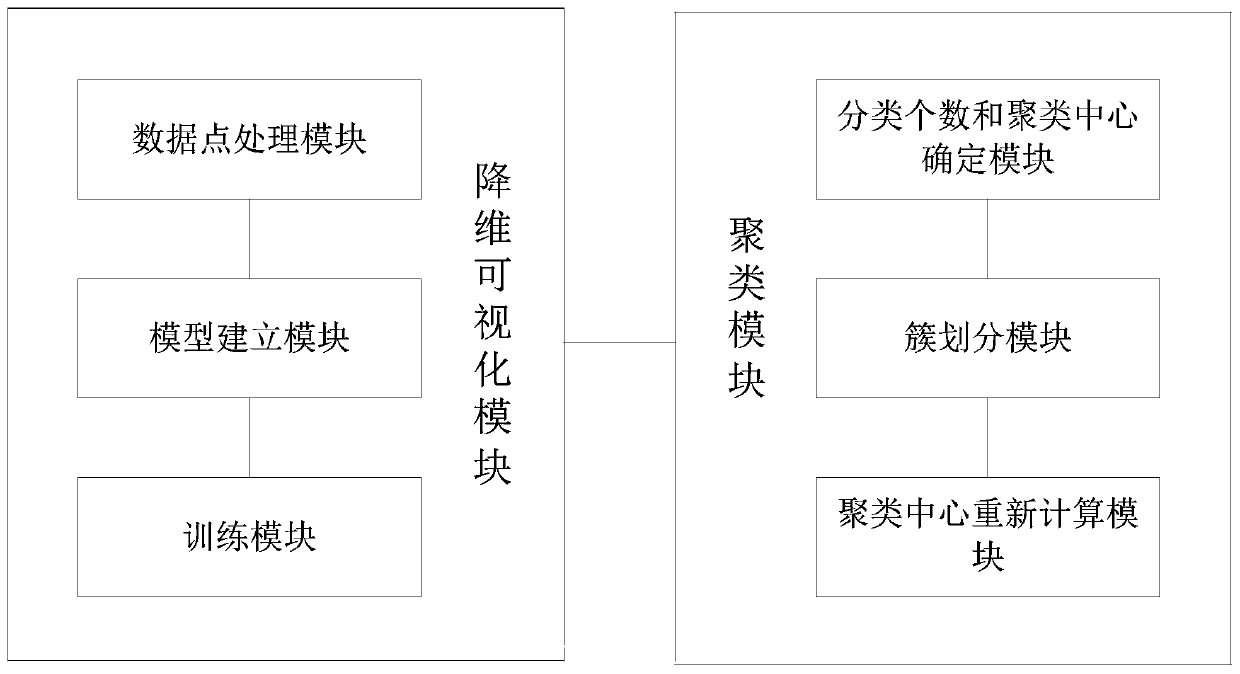
[0069] like figure 1 As shown, a malicious code family clustering method in this embodiment is an effective malicious code family clustering method based on the T-SNE and K-means algorithm. The method mainly uses the malicious code execution sequence as an original feature, and adopts The T-SNE algorithm visualizes the number of clusters of malicious code families, and then uses the K-means algorithm to cluster the malicious code families. Method of the present invention comprises the following steps:
[0070] (1) Using the T-SNE algorithm to perform dimensionality reduction visualization on the original malicious code execution sequence; including the following steps:
[0071] (1.1) Use the T-SNE algorithm to model the distribution of each data point's neighbors, where the neighbors refer to the collection of data points close to each other; in the original high-dimensional space, the present invention models the high-dimensional space as a Gaussian distribution, While in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com