Offline authentication system and method thereof
An authentication and system data technology, applied in the field of offline authentication, can solve the problems of inability to solve software and hardware environment cloning, inability to ensure trusted system environment authentication services, etc., and achieve the effect of preventing resource exhaustion attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
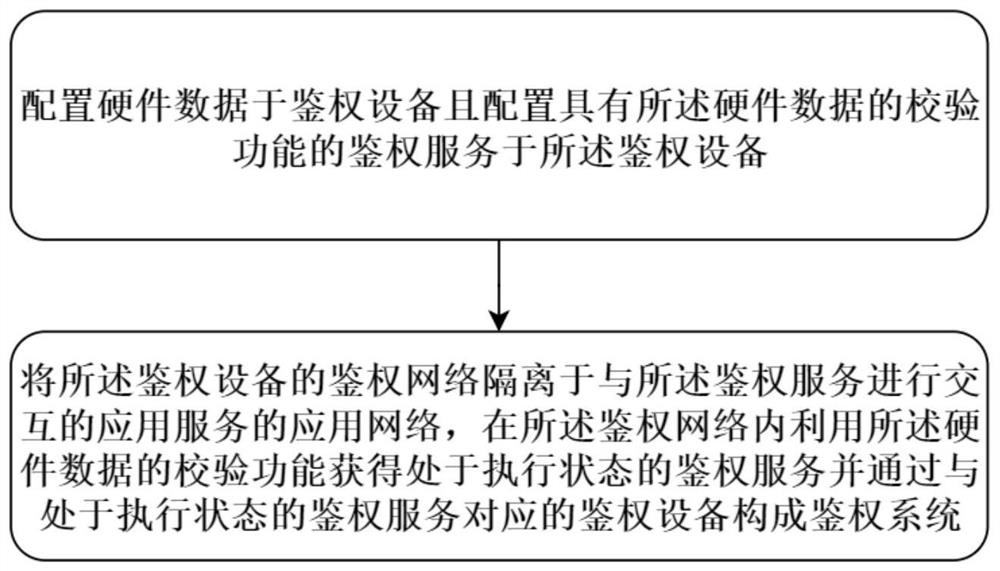
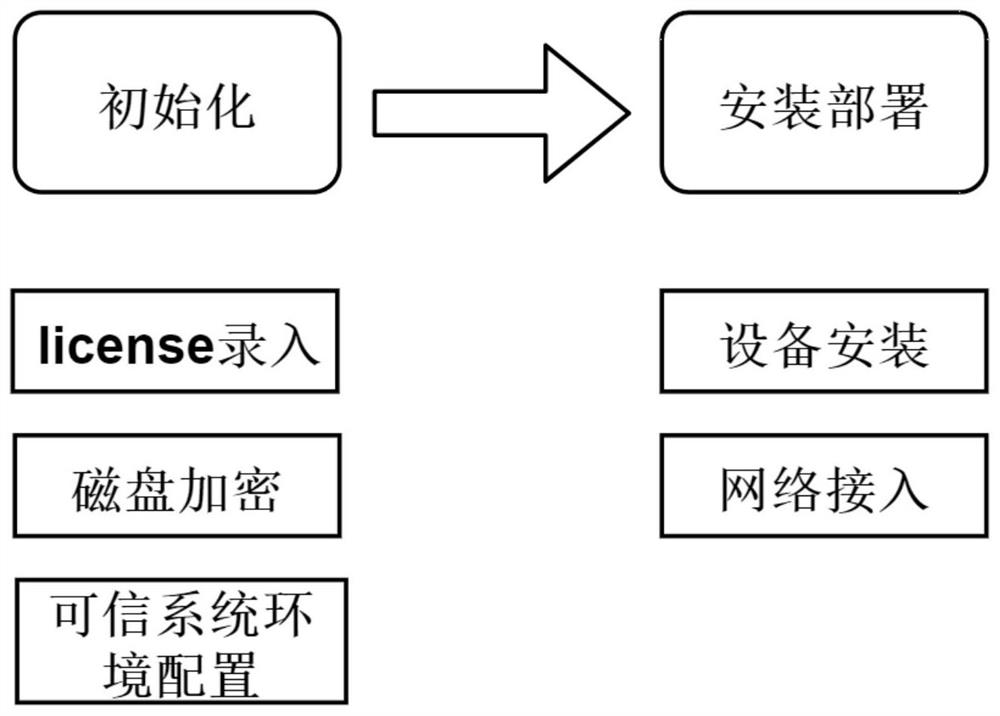
[0088] Such as figure 1 with image 3 , for the method of constructing the authentication system, it can also be called the initialization and installation and deployment of the authentication system, the method includes:
[0089]S1) Configuring hardware data on an authentication device, and configuring an authentication service with a verification function of the hardware data on the authentication device;
[0090] S2) Isolate the authentication network of the authentication device from the application network of the application service that interacts with the authentication service, and use the verification function of the hardware data in the authentication network to obtain the execution state Authentication service, and constitute an authentication system through the authentication device corresponding to the authentication service in the execution state;
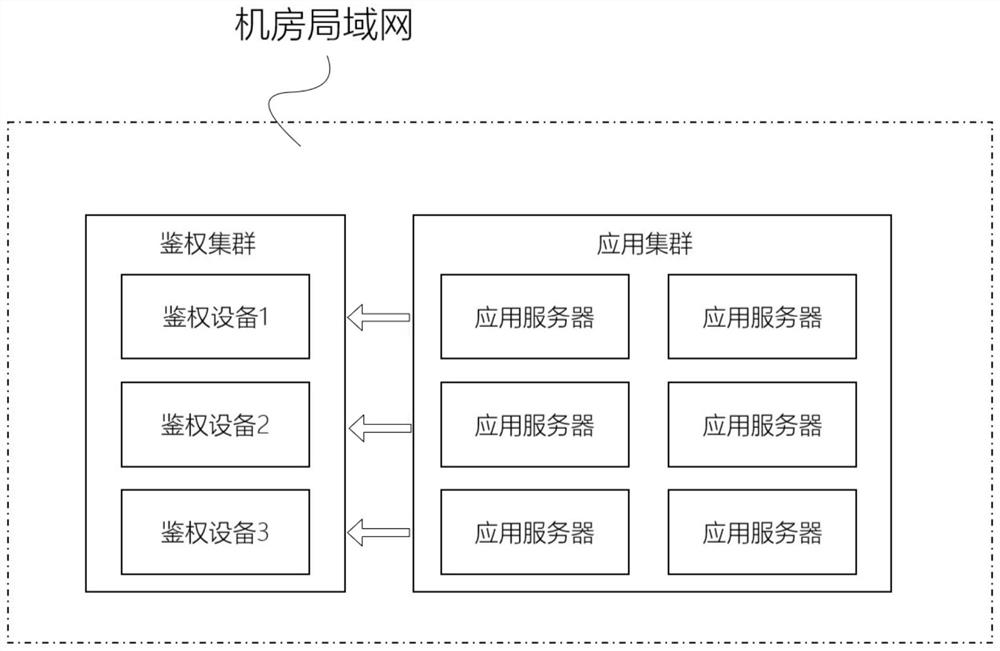
[0091] The authentication device can be a single or a cluster (more than two); the authentication device can have ...
Embodiment 2
[0122] A method for constructing an authentication system through an authentication device cluster, the method comprising:
[0123] A1) Configure hardware data on at least three authentication devices and configure authentication services with the verification function of the hardware data to serve each authentication device, wherein one of the at least three authentication devices is selected arbitrarily The authority device has a historical consensus database of block data that is generated according to a preset probability and conforms to a preset rule over time, wherein the block data includes historical hash data or empty data with a time stamp, and the historical The hash data is configured as hardware data of the at least three authentication devices and has a time stamp;
[0124] A2) Isolate the authentication network of the at least three authentication devices from the application network of the application service interacting with the authentication service, and use...
Embodiment 3
[0127] On the basis of Example 1, such as Figure 4 with Figure 5 , to start the pre-configured authentication system, the startup method includes:
[0128] B1) Start the authentication device, use the verification function of the system data of the authentication device to perform the verification of the system data, and when the verification of the system data passes, proceed to step B2);
[0129] B2) Start the authentication service in the authentication device, use the verification function of the hardware data of the authentication service to perform the verification of the hardware data, and configure the hardware data when the verification of the hardware data passes The above authentication service enters the execution state, and completes the startup of the authentication system.
[0130] Specifically, in step B1), after the authentication device is started and until the system data verification function of the authentication device is used to perform the verificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com