High-speed multiple-point operation method for elliptic curve passwords
An elliptic curve cryptography and computing method technology, applied in the field of elliptic curve cryptography, can solve the problems of decreased system cost performance, increased energy consumption, inability to perform parallel operations, etc., to achieve improved throughput, improved system performance, optimal performance and resource utilization Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be further described below in conjunction with specific embodiment:
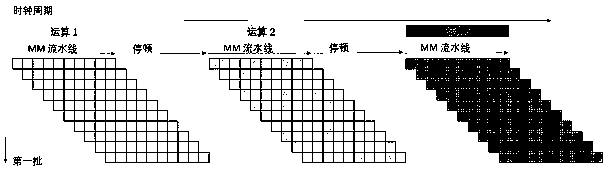
[0059] Such as Figure 4 , under the Jacobian projection coordinates, one doubling operation executes 9 modular multiplication operations, using a double-pipelined Montgomery modular multiplier and four pipelined adders. Multiple operation requests can be continuously accepted each time, and each request is in a different clock cycle. Until the first request result of the batch is output, the point multiplier will not accept new operation requests. The steps of the operation method are Serially, the specific steps are as follows:
[0060] S0: idle until input data (x, y, z) is obtained;
[0061] S1: In the first calculation cycle, the calculations of each step are performed simultaneously, the adder 1 calculates t3=y+z, the modular multiplier 1 calculates d=z*z, and the modular multiplier 2 calculates g=y*y;
[0062] S2: In the second calculation cycle, the calculations o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com