A Link Removal Method for Network Structure Privacy Preservation Against Link Prediction
A privacy protection and network structure technology, which is applied in the field of link deletion of network structure privacy protection, can solve problems such as insufficient protection of important target links, untargeted privacy protection, and reduced availability of network structures, so as to achieve retained availability and strong resistance The effect of link attack capability and good network availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
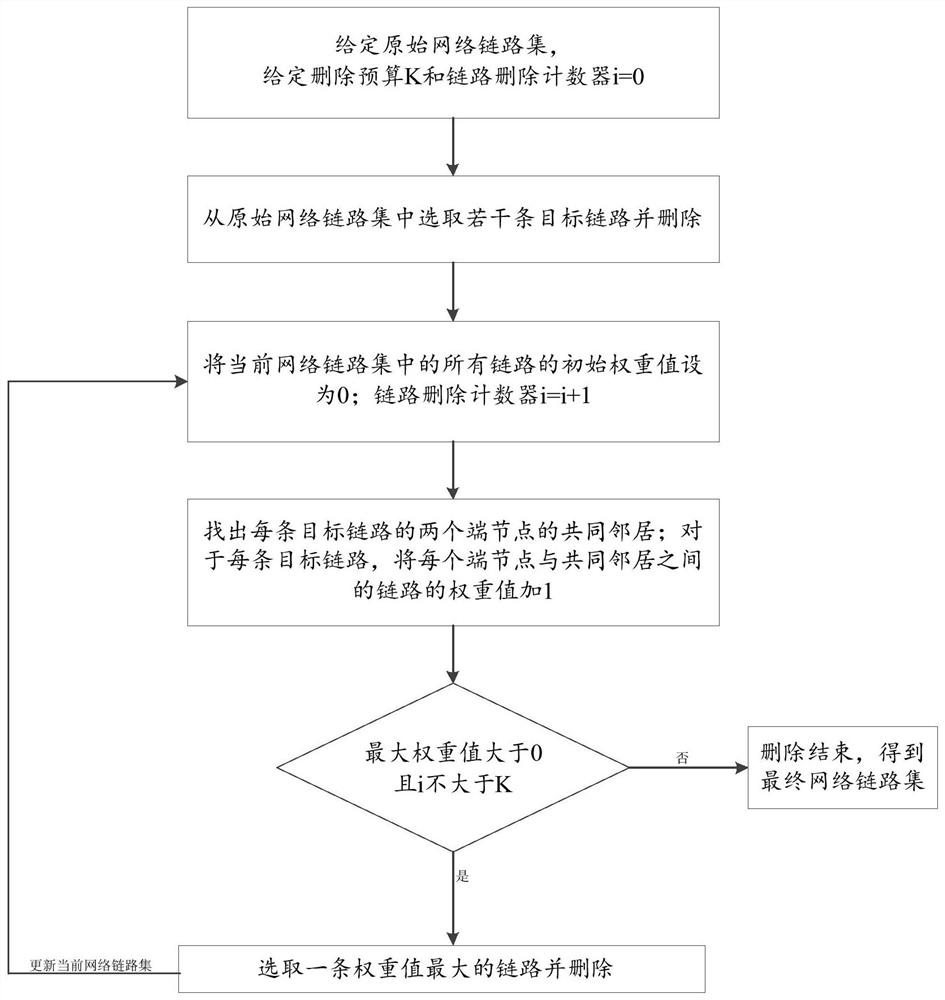
[0052] In this example, see figure 2 , there are 6 nodes in the original network link set, namely a, b, c, d, e and f; there are 9 undirected links, respectively (a, b), (a, c), (b, d), (b,c), (c,d), (d,e), (d,f), (e,c) and (e,f). The dotted line represents the target link, the solid line represents the non-target link, and the deletion budget K=2.
[0053] Set the initial weight values of all links in the current network link set to 0; link deletion counter i=1. Select (b, c) and (d, e) as the target link by random sampling, find out the common neighbors a and d of the two end nodes of the (b, c) target link; find out the (d, e) target The common neighbors c and f of the two end nodes of the link. For (b, c) target link, add 1 to the weight value of the link between b and c end nodes and common neighbors a and d; for (d, e) target link, add d and e end nodes to Add 1 to the weight value of the link between common neighbors c and f; the link with the final weight value ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com