System for realizing safe user data acquisition and authorization processing and method thereof
A user data and data collection technology, which is applied in user data collection and the Internet field, can solve problems such as increasing data, relying on data automatic sorting, and target websites to obtain customized data, so as to achieve the effect of protecting user data and reducing the risk of data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
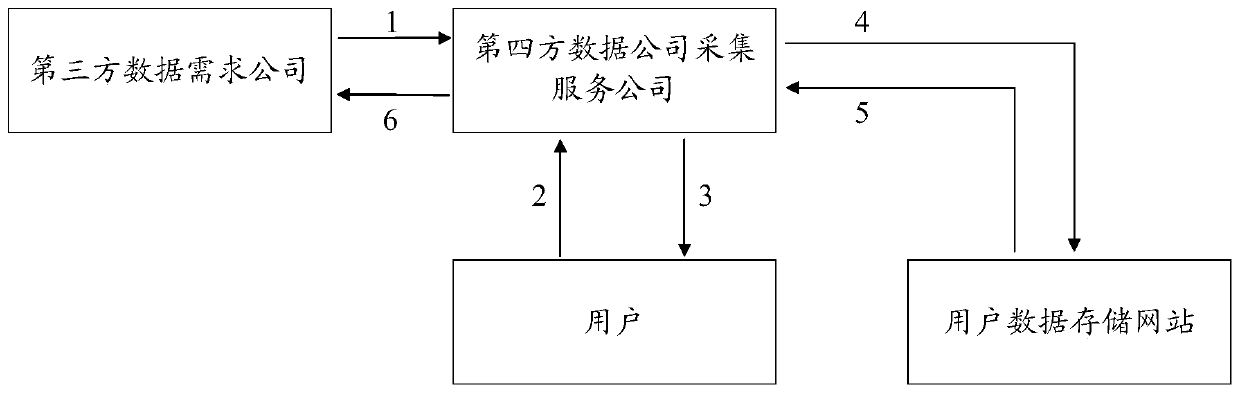
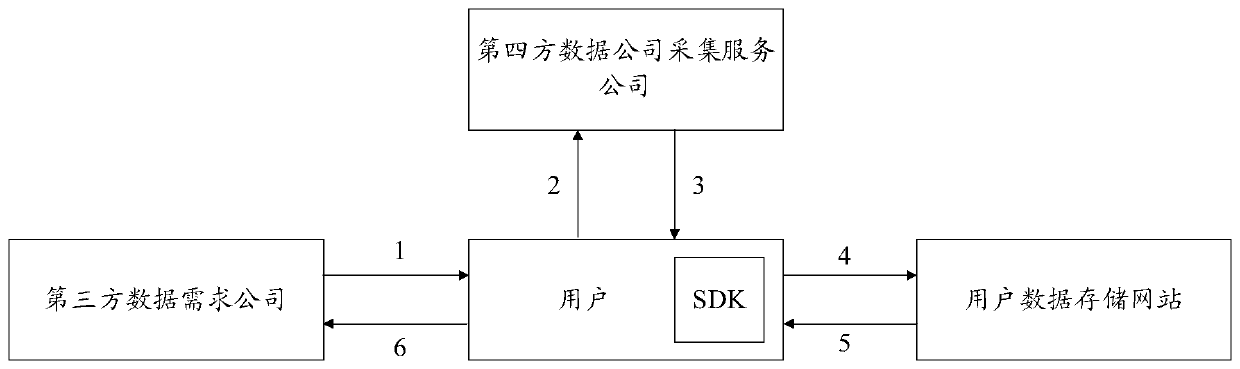
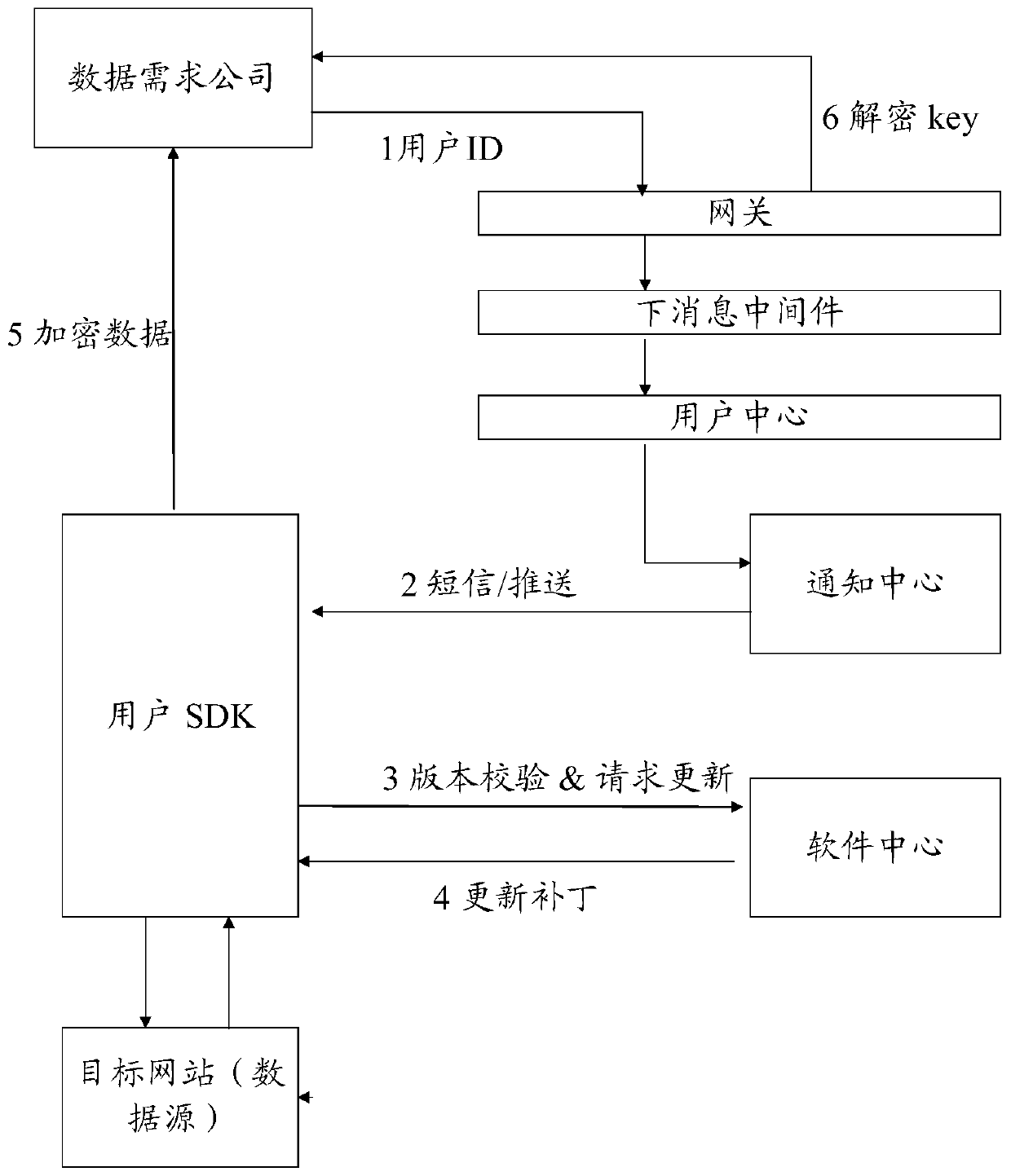
[0053] The system for realizing safe user data collection and authorization processing of the present invention includes:
[0054] User modules, including SDK units, are used to locally load and run scripts that implement data collection, analysis, and processing functions;
[0055] The fourth-party data acquisition module is connected to the SDK unit and is used to check the update status of the SDK without receiving data streams;
[0056] The user data storage module is connected with the user module and used for storing user data.
[0057] As a preferred embodiment of the present invention, the system also includes:
[0058] The third-party data demand module is connected with the user module and is used to directly request data from the user module and obtain authorization data.
[0059] As a preferr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com