A security device data communication protocol for cooperative network defense
A technology of security equipment and data communication, applied in the direction of security communication devices, digital transmission systems, electrical components, etc., can solve the problems of responding to network threats, whether it can handle unpredictability, etc., and achieve the effect of flexible change and accurate content.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
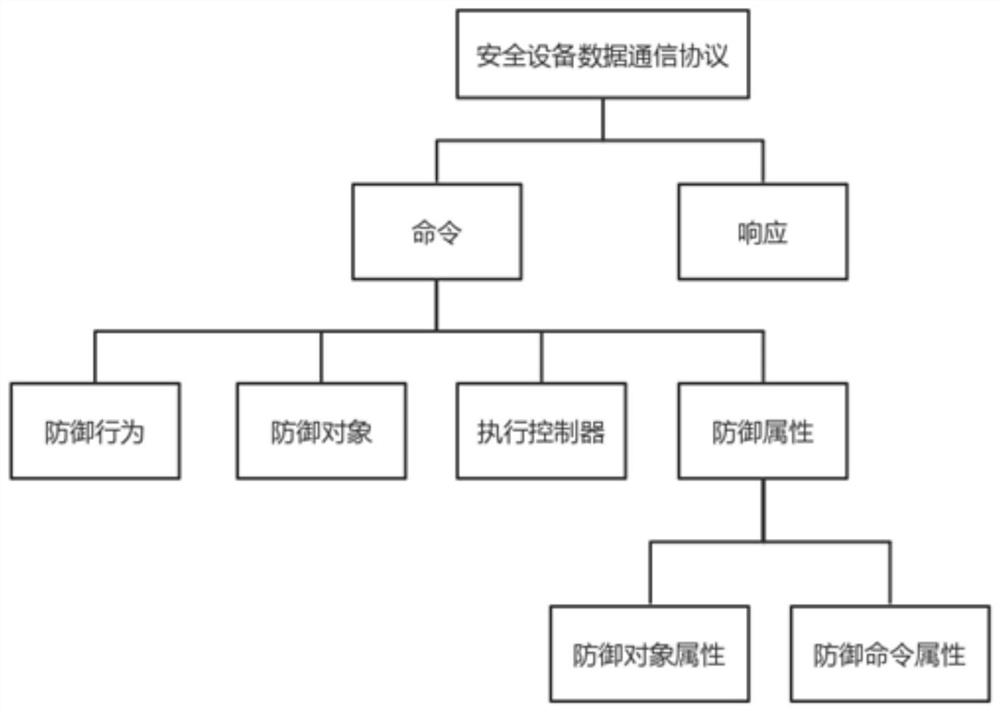
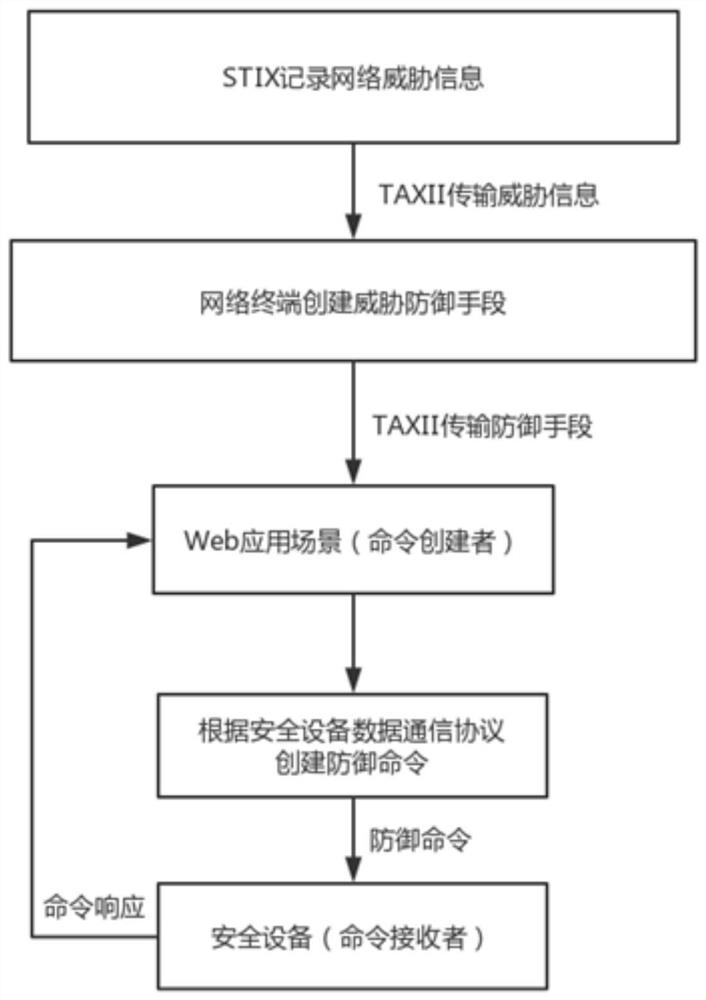
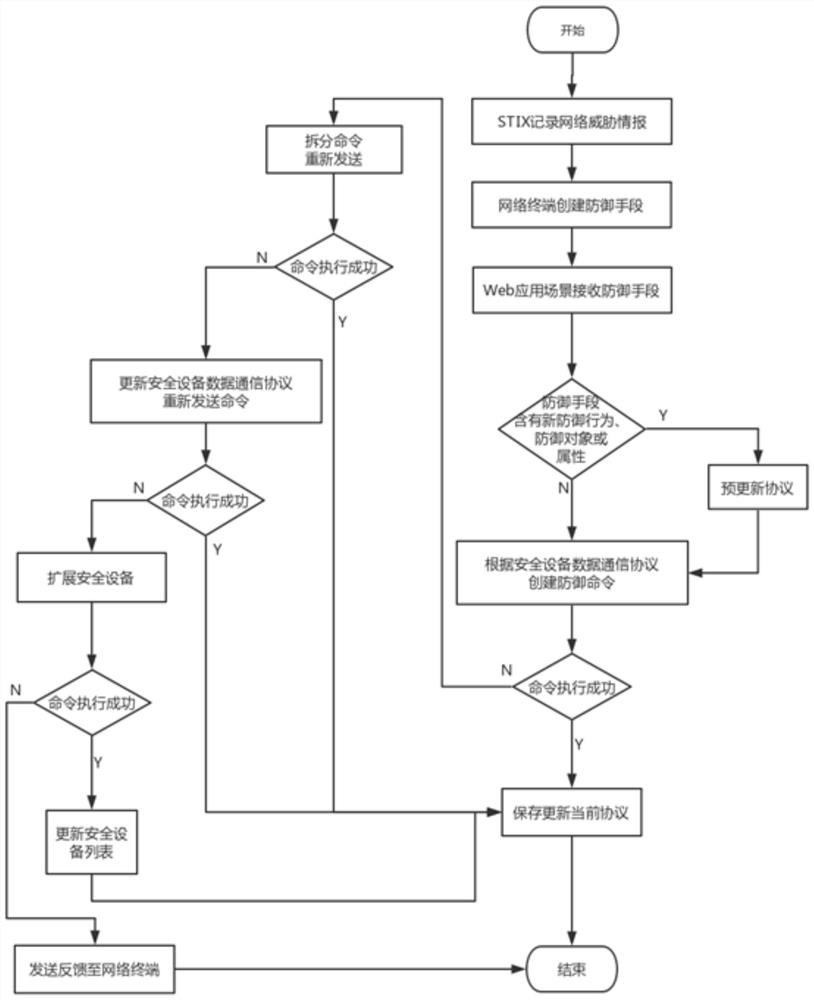
[0024] A security device data communication protocol for collaborative network defense, which accelerates the speed of existing network defense through the data communication between the creator of the collaborative network defense command and the command receiver. This protocol creates a network defense command and sends it to the command receiver. After the command receiver successfully receives the command, it creates a command response to the received command according to this protocol and sends it back to the command creator; in this protocol, the command receiver is a security For devices, the protocol defines a language for creating cyber defense commands and responses, and supports updating of content.
[0025] The protocol defines the language for network defense command creators to create commands and command receivers to receive commands, and supports content updates.
[0026] Among them, the network defense command consists of a four-tuple:
[0027] , the element ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com