A method for authorizing the use of software content
A software and content technology, applied in the field of information security, can solve problems such as inability to realize self-service authorization, inaccurate machine identification, cracking, etc., and achieve the effects of reducing the risk of interception analysis, improving recognition rate, and improving usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0081] An embodiment of the present invention provides a method for authorizing the use of software content, the method may include:
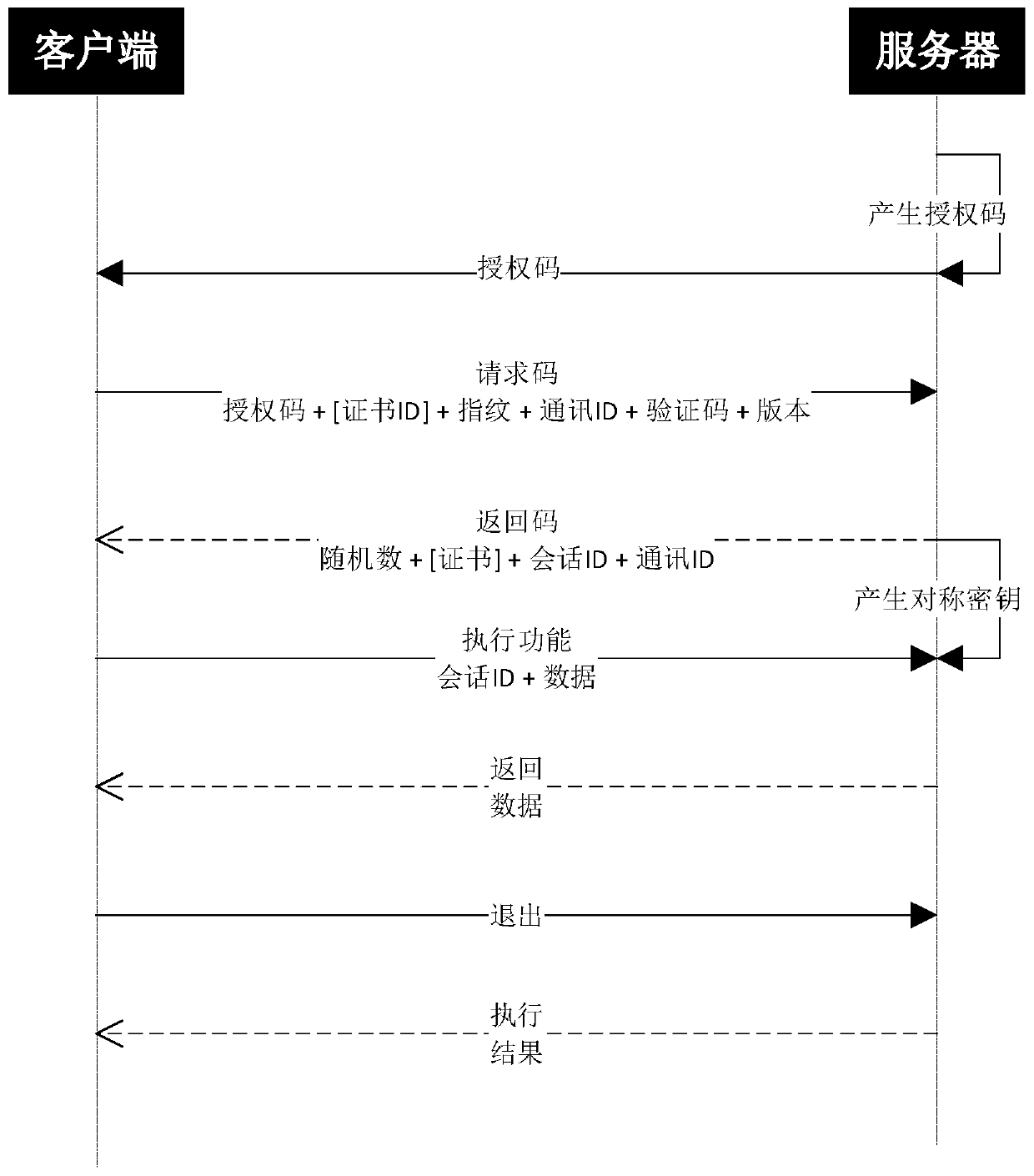
[0082] 101. The Bitcloud server receives a protection instruction associated with software content triggered by the first user through the software content provider client.
[0083] 102. The bitcloud server generates an authorization code for the second user to use the software content based on any device according to the protection instruction.
[0084] The authorization code in this embodiment is sent to the second user along with the software, so that the second user can activate, upgrade or use the software based on the authorization code.
[0085] In practical applications, before step 101, in this embodiment, the bit cloud server also responds to the operation of the first user to obtain the SDK corresponding to the software content, and the SDK is embedded in the software sent by the second user.
[0086] 103. The BitCloud server receiv...
Embodiment 2
[0114] An embodiment of the present invention provides a method for authorizing the use of software content, the method may include:
[0115] 201. The Bitcloud server receives an authentication request sent by a software client in any device, and the authentication request includes authentication information carrying an authorization code of the software content to be used.
[0116] Wherein, the authorization code can be understood as a code generated by the Bitcloud server for the second user to use the software on any device after receiving the protection instruction associated with the software content triggered by the first user through the client of the software content provider. The authorization code for the content.
[0117] For example, the authentication information in this step may also include: the authorization information of the software content generated by the bit cloud server according to the protection instruction;
[0118] The authorization information incl...
Embodiment 3
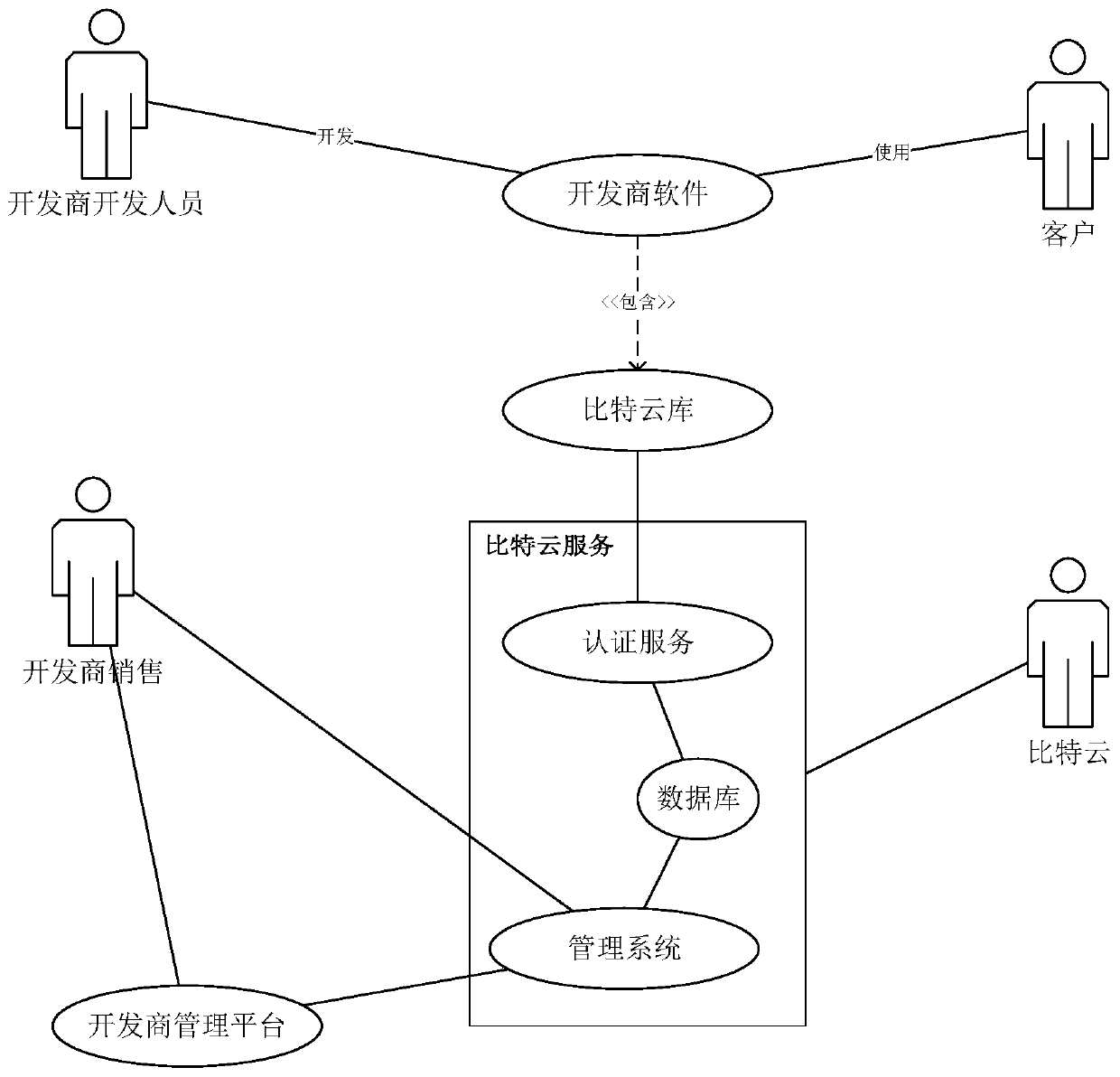
[0148] combine figure 1 As shown, the authorization scheme of the present embodiment includes the following parts: database, authentication service module, management system, client library (i.e. figure 1 Bit cloud library) and some tool software. For a diagram of the relationship between each part, see figure 1 software use case diagram.
[0149] The database is used to store various data such as product information, user information, authorization information and authentication information.
[0150] The authentication service module mainly provides authentication services for customers and completes the generation, activation and upgrading of authorization codes, which is the core of the whole system.
[0151] The management system mainly manages authorization and user information, and is the developer's operation interface; at the same time, it provides a WebService interface for the client program (that is, the client library of Bitcloud) and the management platform, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com