Method and device for generating decoy-state quantum light pulses
A technology of decoy state quantum and generation method, applied in the field of optics, can solve problems such as inability to apply to a variety of situations and lack of universal communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
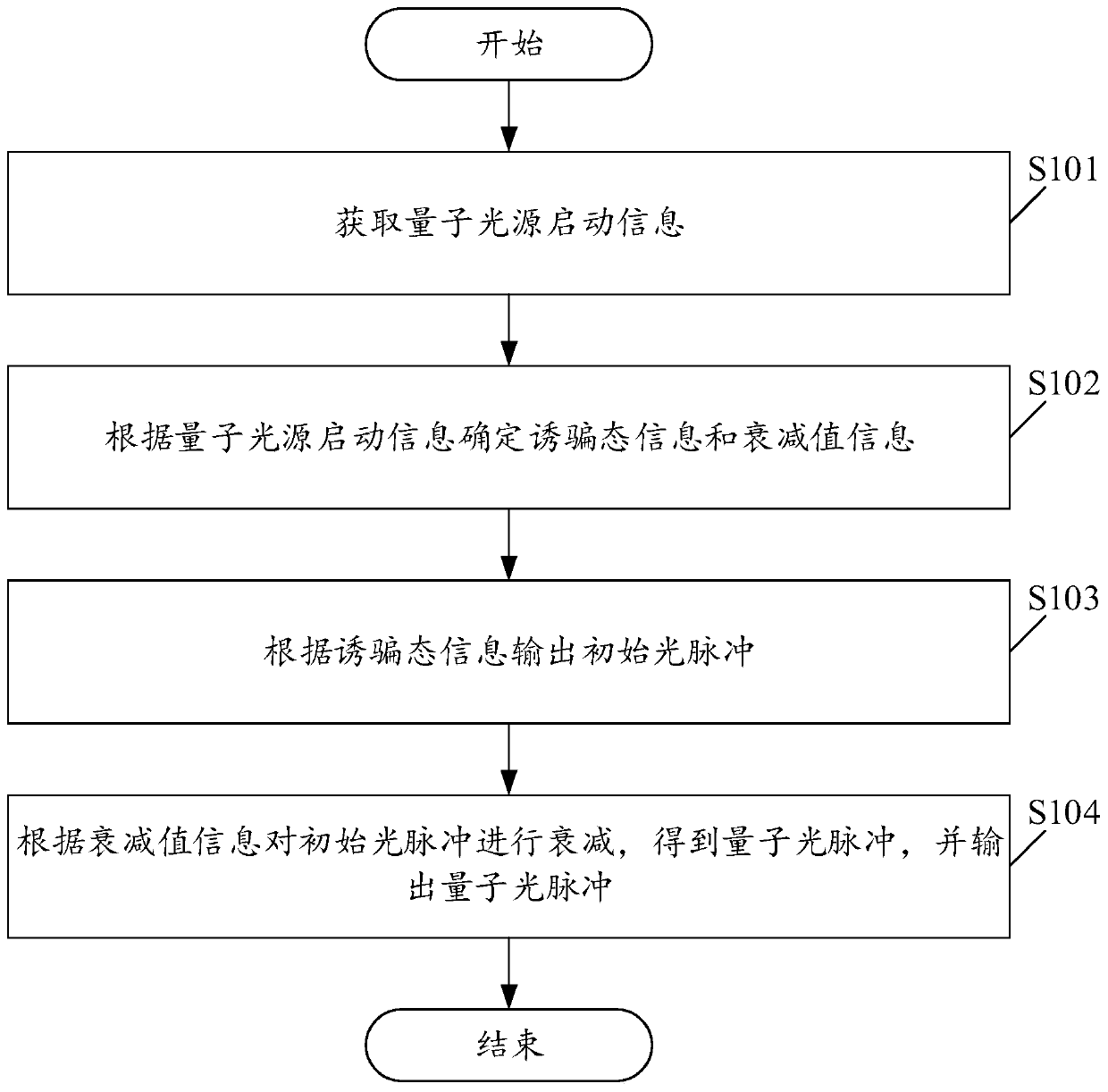
[0048] Please see figure 1 , figure 1 A schematic flowchart of a method for generating a decoy state quantum light pulse is provided for the embodiment of the present application. Depend on figure 1 It can be seen that this method can be applied in the field of optical communication. Specifically, this method can output communication optical pulses with high confidentiality and high stability by setting the quantum light source activation information, so that the corresponding communication can be improved during the communication process. safety and stability. For example, this method can be applied to quantum key distribution to improve security and stability. Wherein, the generation method of the quantum light pulse includes:
[0049] S101. Acquire the start information of the quantum light source.
[0050] In this embodiment, the quantum light source activation information includes at least three parts: quantum light source parameters used to control light pulse outpu...
Embodiment 2
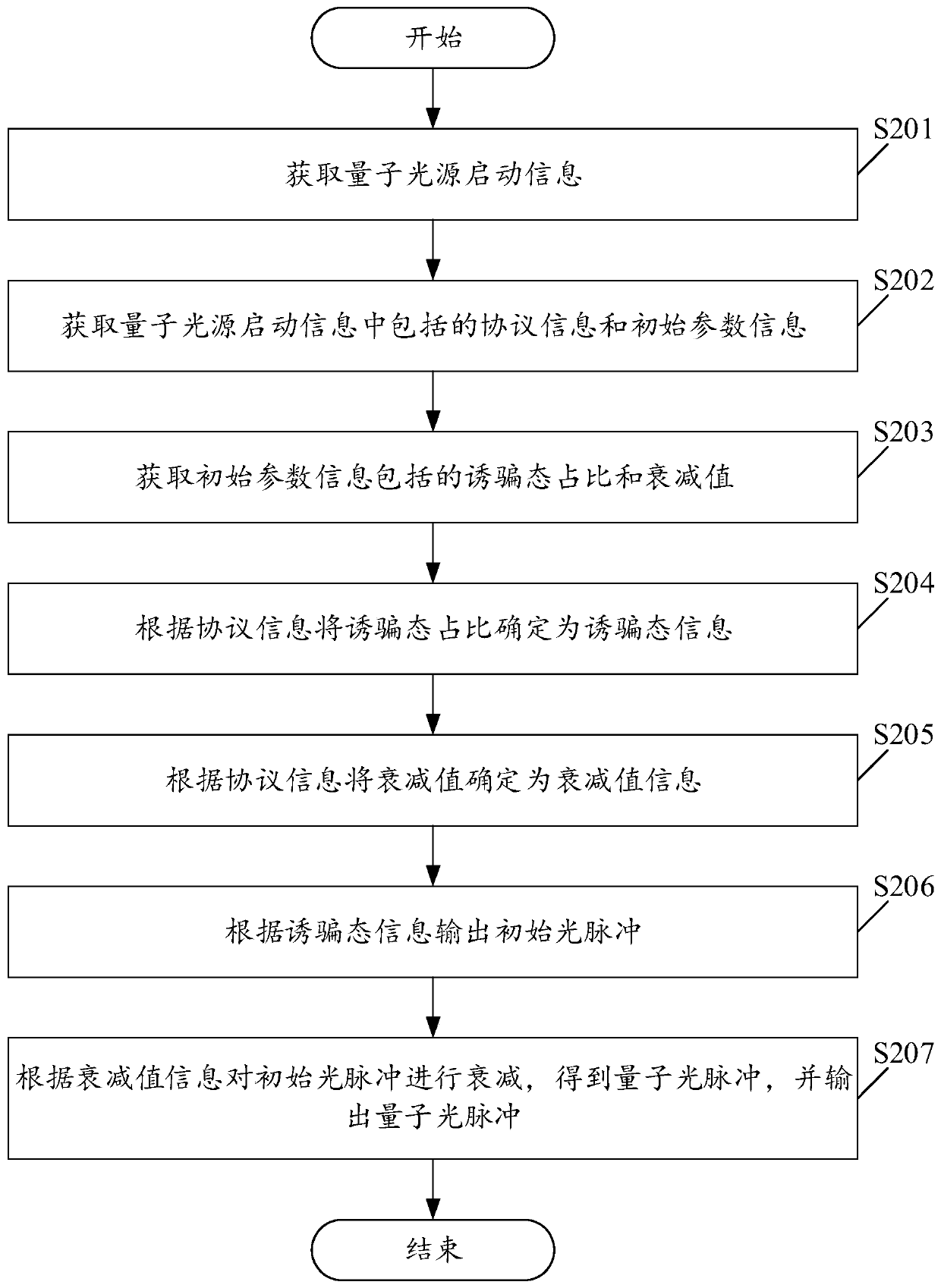
[0077] Please see figure 2 , figure 2 It is a schematic flowchart of another method for generating a decoy state quantum light pulse provided in the embodiment of the present application. figure 2 The flow diagram of the described method for generating the decoy-state quantum light pulse is based on figure 1 The schematic flow chart of the described decoy-state quantum optical pulse generation method is improved. Wherein, the protocol information used in the method for generating quantum light pulses may be COW protocol information, and the method may specifically include:
[0078] S201. Acquire the startup information of the quantum light source.
[0079] In this embodiment, the quantum light source activation information includes at least three parts: quantum light source parameters used to control light pulse output, decoy state information used to construct a decoy state, and attenuation value information used to control attenuation.
[0080] In this embodiment, the q...
Embodiment 3
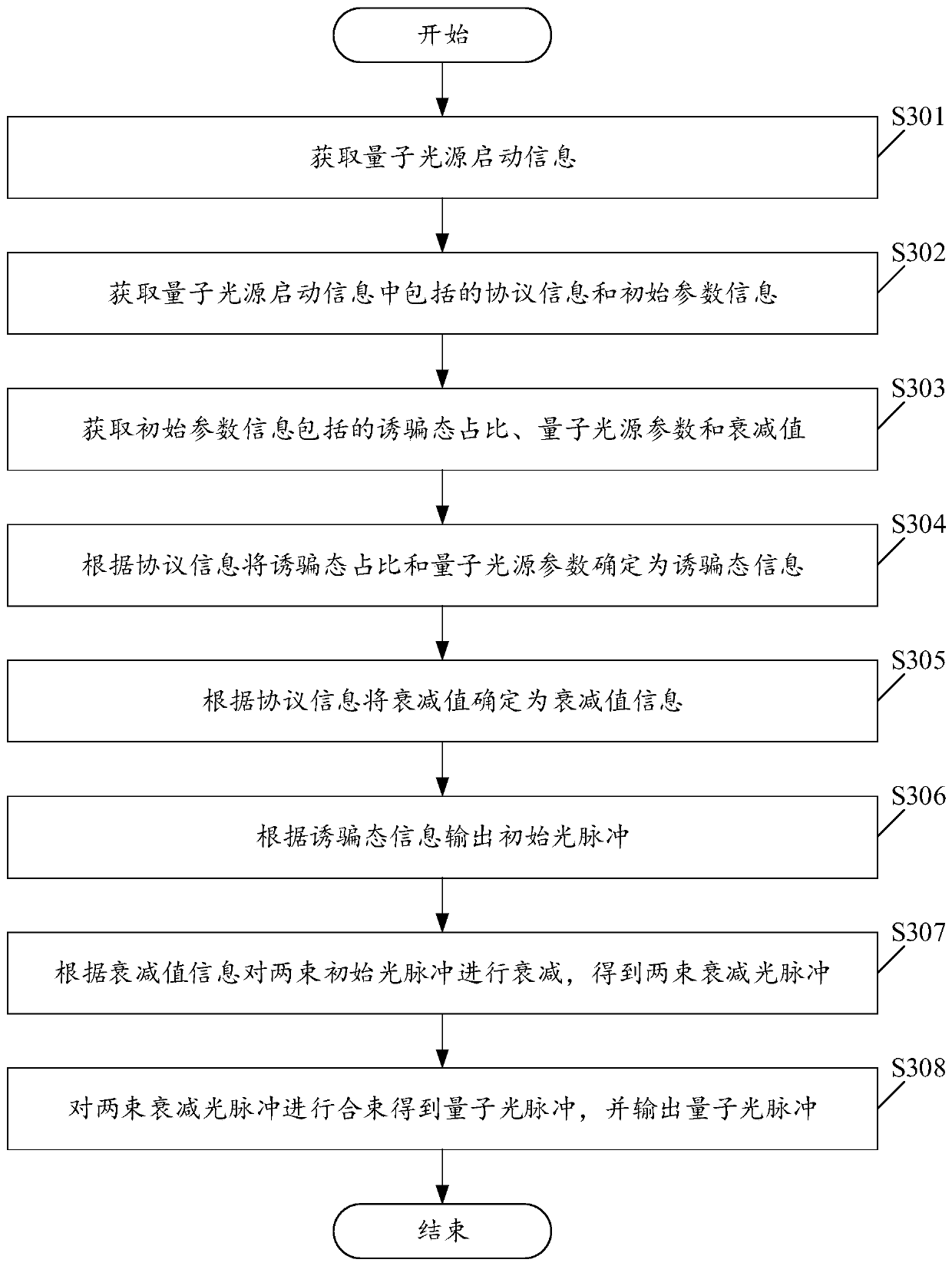
[0117] Please see image 3 , image 3 It is a schematic flowchart of another method for generating a decoy state quantum light pulse provided in the embodiment of the present application. image 3 The flow diagram of the described method for generating the decoy-state quantum light pulse is based on figure 2 The schematic flow chart of the described decoy-state quantum optical pulse generation method is improved. Wherein, the protocol information used in the quantum optical pulse generation method may be BB84 protocol information, and the method may specifically include:
[0118] S301. Acquire the startup information of the quantum light source.
[0119] In this embodiment, the quantum light source activation information includes at least three parts: quantum light source parameters used to control laser output from the laser, decoy state information used to construct a decoy state, and attenuation value information used to control attenuation.
[0120] In this embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com