Application access method, device and equipment
An access method and access request technology, applied in the computer field, can solve problems such as user information leakage and resource loss, and achieve the effect of reducing resource loss and reducing the probability of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
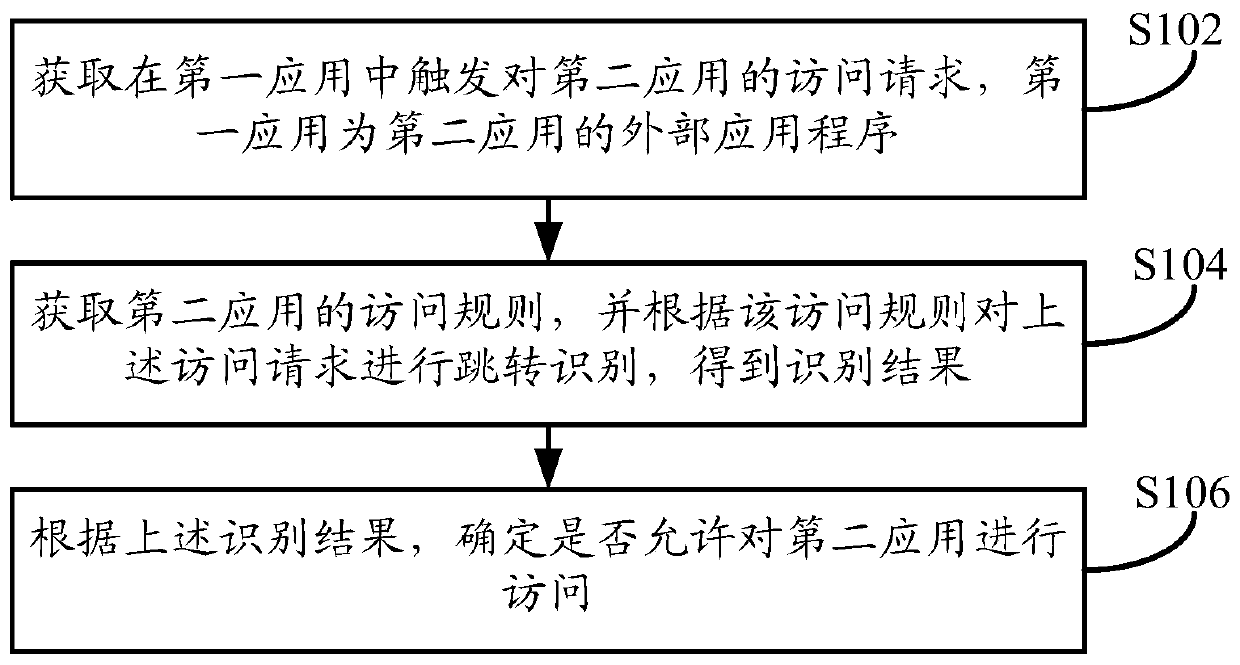
[0077] Such as figure 1 As shown, the embodiment of this specification provides an application access method, and the execution body of the method may be a terminal device or a server, etc., wherein the terminal device may be a mobile terminal device such as a mobile phone or a tablet computer, or a personal computer, etc. equipment. This method can be used in processes such as judging whether to allow access to the redirected application program when the user jumps from one application program to another. The method specifically may include the following steps:
[0078] In step S102, the access request to the second application triggered in the first application is obtained, and the first application is an external application program of the second application.
[0079] Wherein, the first application may be any application, such as an instant messaging application, a shopping application, or a browser. The second application may be any application different from the first ...
Embodiment 2
[0101] Such as Figure 4 As shown, the embodiment of this specification provides a method for accessing an application. The method may be executed by a terminal device and a server, where the terminal device may be a personal computer or the like. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be a background server of a certain business (such as financial services, etc.), or a website (such as an online shopping website or payment application, etc.) background server, etc. This method can be used in processes such as judging whether to allow access to the redirected application program when the user jumps from one application program to another. The method specifically may include the following steps:
[0102] In step S402, the terminal device acquires an access request to the second application triggered by a target link in the first application based on the URL Schemes mechanism.
[0103] Wherein, the access ...
Embodiment 3
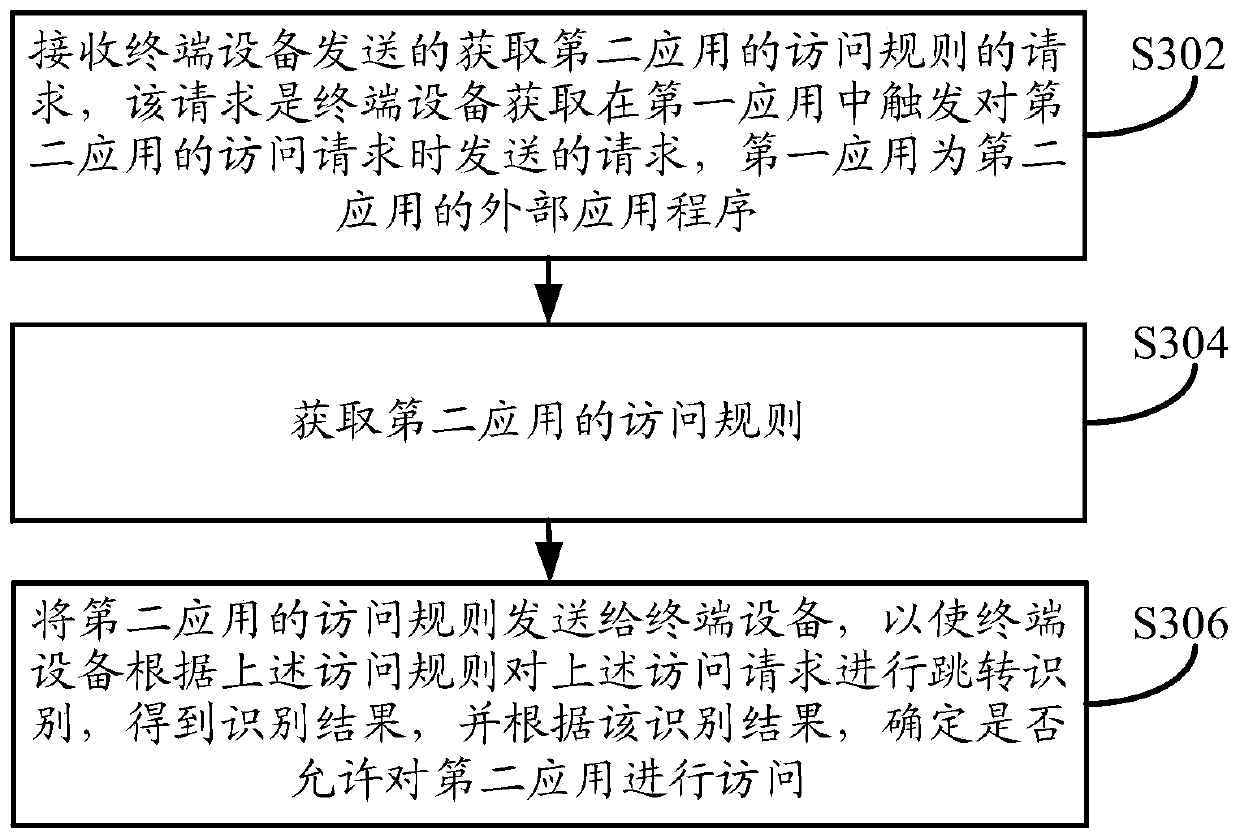
[0127] Such as Figure 5 As shown, the embodiment of this specification provides a method for accessing an application, and the execution subject of the method may be a terminal device, where the terminal device may be a personal computer or the like. This method can be used in processes such as judging whether to allow access to the redirected application program when the user jumps from one application program to another. This embodiment can be a detailed description of the situation where the access rules of an application are stored in the terminal device, and the method can specifically include the following steps:
[0128] In step S502, the terminal device acquires an access request to the second application triggered by a target link in the first application based on the URL Schemes mechanism.
[0129] In step S504, the terminal device obtains the access rule of the second application.
[0130] In step S506, the terminal device verifies the access rule according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com