Expandable lightweight proving method for Internet of Things equipment
A lightweight technology for Internet of Things devices, applied in key distribution, can solve the problems of low-end embedded devices and expensive public key encryption, high memory usage and power consumption, and achieve good application value, low overhead, and attack resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described in detail in conjunction with the accompanying drawings and specific embodiments.
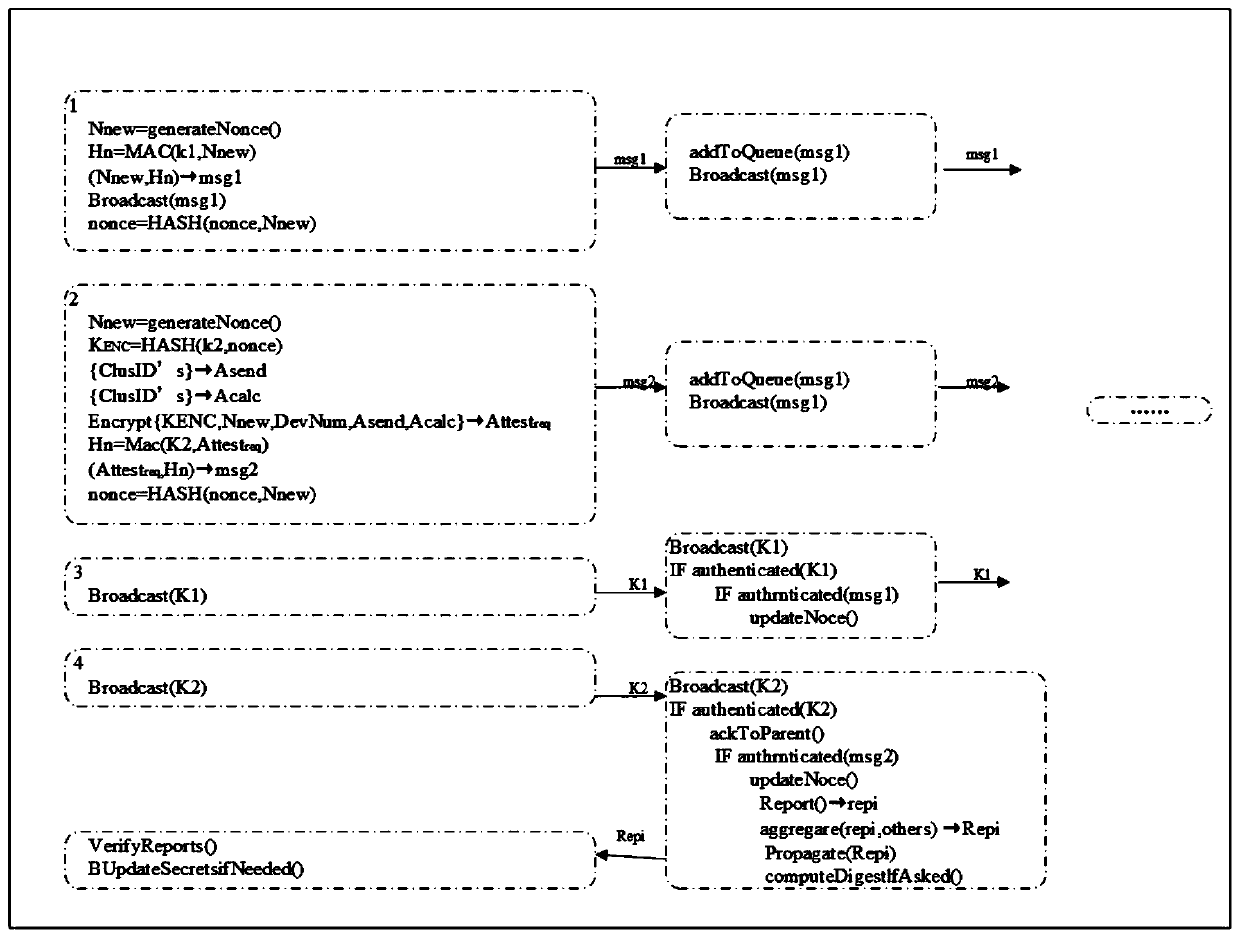
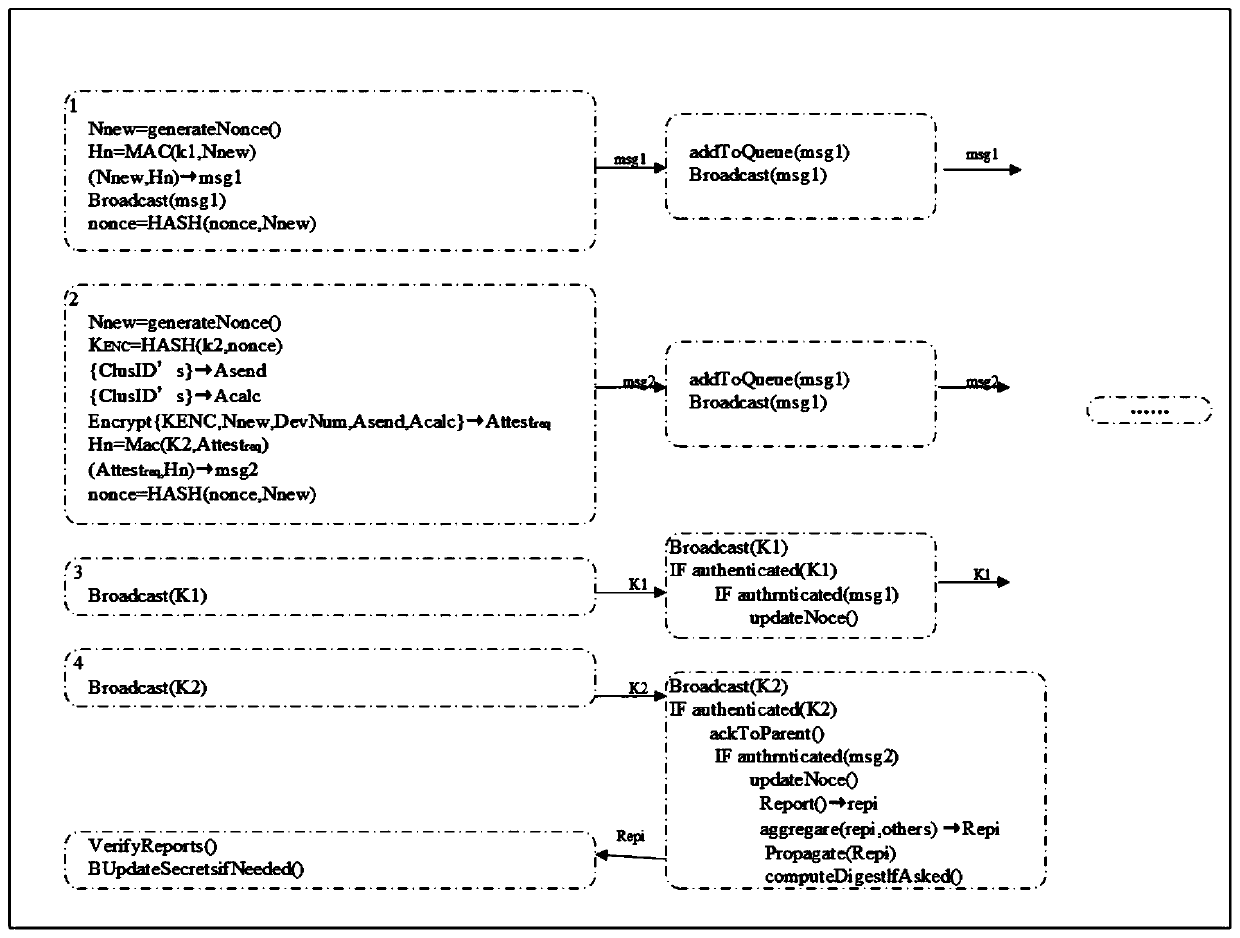
[0022] A scalable lightweight proof method for IoT devices such as figure 1 shown, including the following specific steps:
[0023] 1) Verifier settings, including: the verifier V first randomly selects the last key K j to generate a one-way keystring of length j, and use K 0 Initialize the device as the commitment key and use K 0 Execute F recursively to verify all other keys in the keychain. Press K for the rest of the keys 1 to K j The sequence of is used as a session key to authenticate packets exchanged during the attestation phase. The validator V then divides time into discrete time intervals, one of which has a maximum duration T a Should not last longer than the overall physical attack time T t. Each time interval is divided into a number of unequal discrete time subintervals. The present invention assumes four non-overla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com