Group authentication method for NB-IoT
A narrow-band Internet of Things and authentication method technology, applied in the field of mobile communications, can solve problems such as MME and HSS signaling congestion, and achieve the effect of reducing the number of signaling interactions and reducing the possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
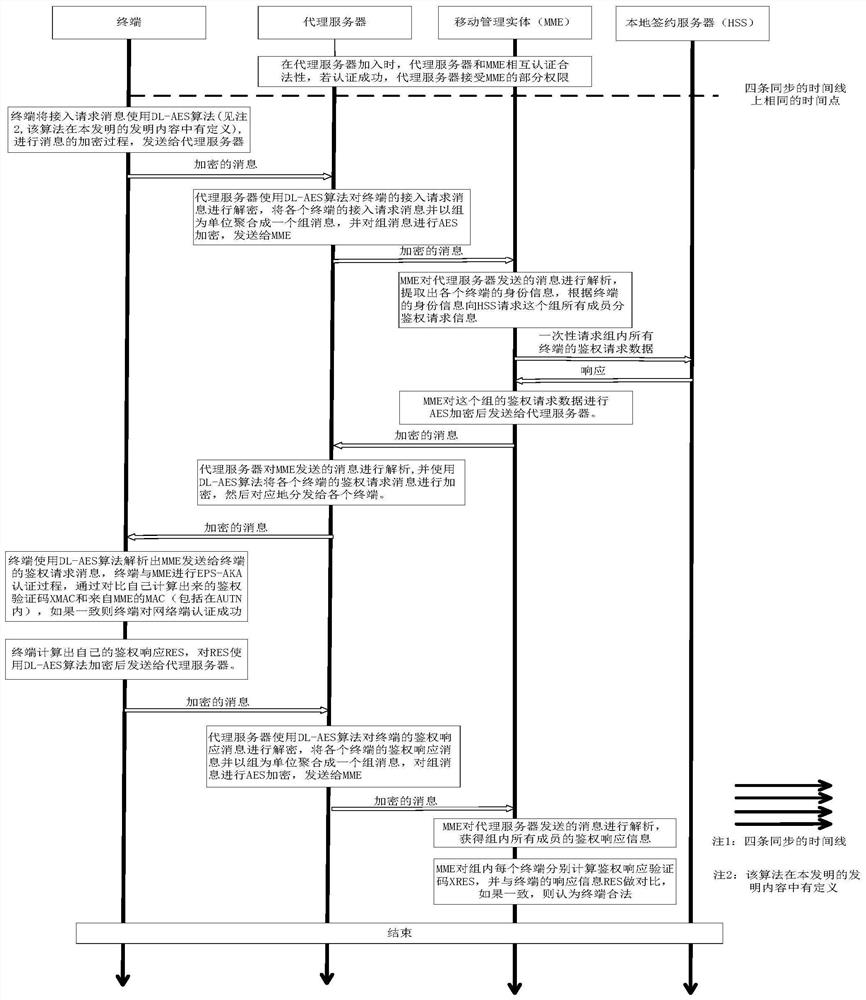
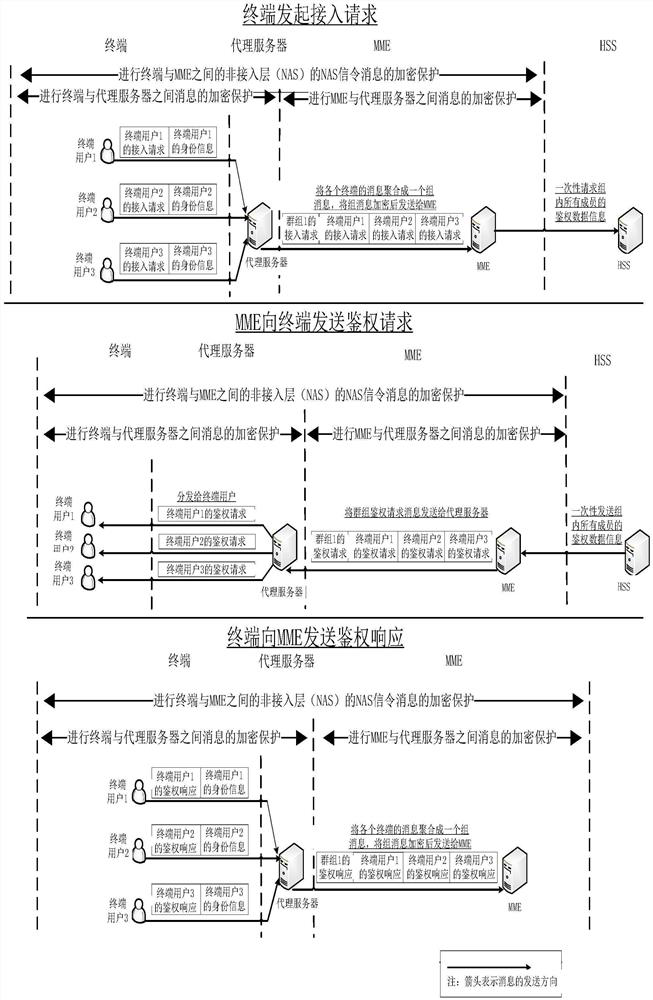
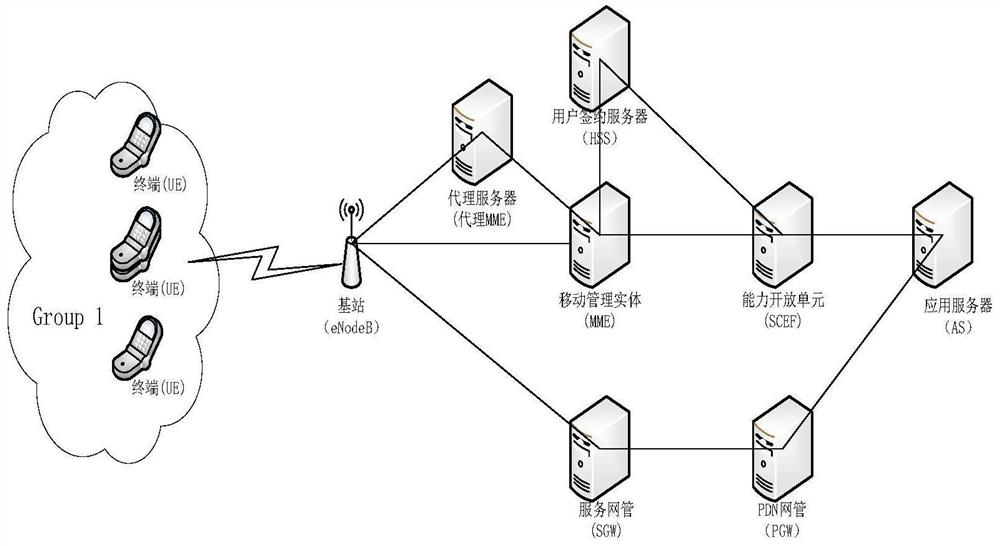
[0041] Such as figure 2 , 3, 4, a method for group authentication of NB-IoT narrowband Internet of Things, including: adding a network element of a proxy server in the NB-IoT core network, and the mobility management entity (MME) and the proxy server pass mutual authentication Authentication ensures the legitimacy of the proxy server, and the legal proxy server accepts the authorization of MME-related permissions. Each proxy server has independent identity information and related keys to ensure the communication security between the proxy server and MME.
[0042] The proxy server establishes a secure channel with each terminal, and uses the encryption method combining the AES symmetric encryption algorithm and the public-private key generated by the discrete logarithm to ensure the security of the information. The DL-AES algorithm is used as the code name of the encryption method mixed with the AES symmetric encryption and the discrete logarithm public key system of the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com