Intelligent evidence obtaining system and method for suspect interrogation process supervision
A suspect and intelligent technology, applied in the parts of TV systems, cooperating devices, parts of color TVs, etc., can solve the problems of insufficient supervision and unsupervised supervision, and achieve accurate and reliable forensic locations and ensure accurate Effects of Sex and Effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
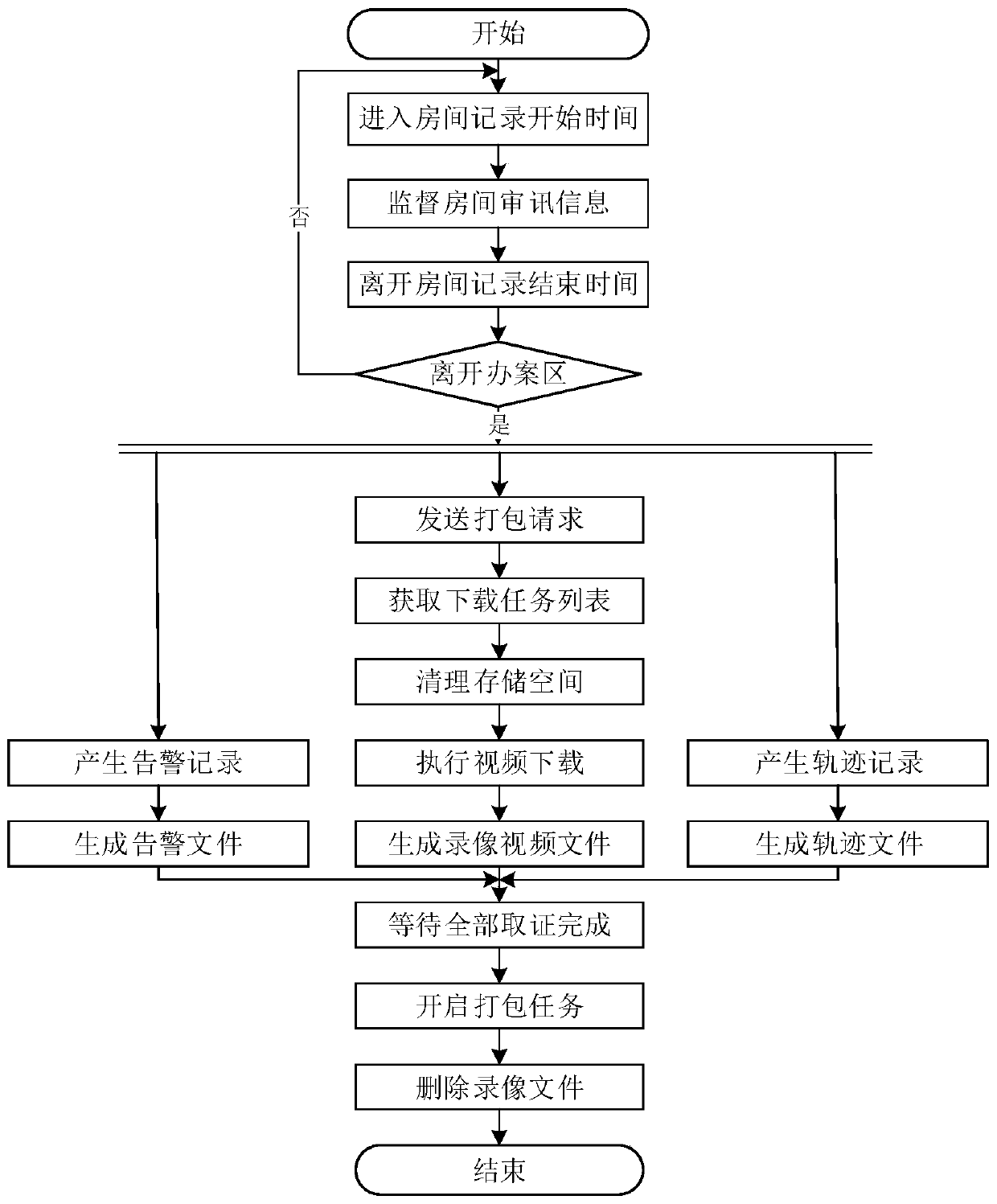
[0098] When the interrogation of the suspect is over and the recorded video file of the interrogation process is downloaded at one time, the specific steps of the intelligent evidence collection method include:
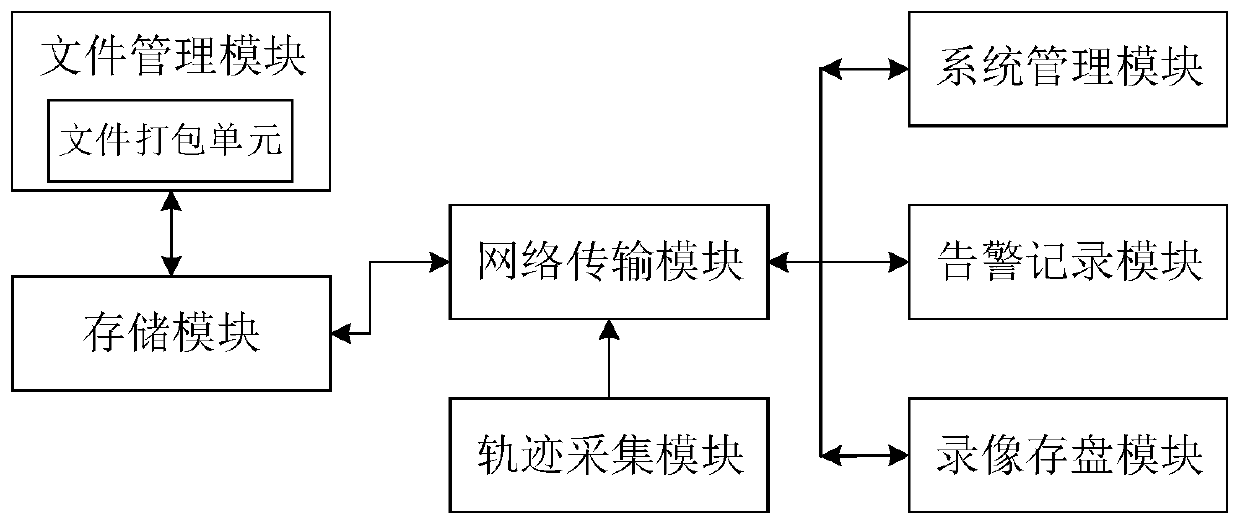
[0099] Step S1. Wear the RFID tag for the person involved, and obtain the information of the RFID tag through the preset positioning base station to obtain the real-time location of the person involved. The real-time location is calculated according to the timeline to generate the behavior track information of the suspect, and the system automatically records the suspect Changes in the location of people, recording the start time and departure time of each room;
[0100] Step S2. According to the obtained real-time location, judge whether there is irregular behavior in the interrogation process, and if so, trigger an irregular behavior alarm and record the alarm information; irregular behavior includes unattended case handling area, single-person interrogation and co-e...
Embodiment 2
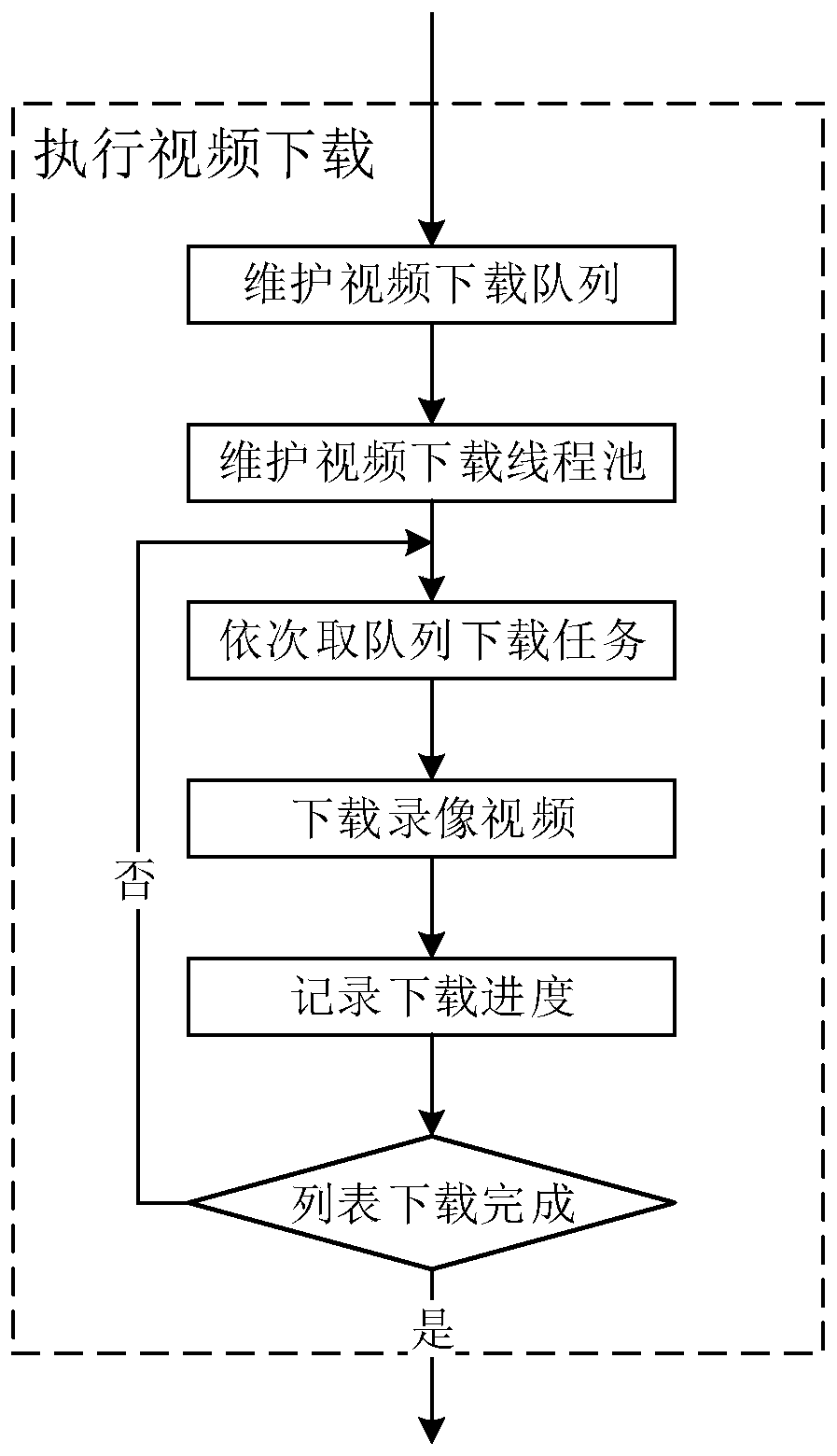
[0116] When the video files of the interrogation process are downloaded multiple times based on the time period in which the suspect is in each interrogation room, each time the suspect leaves a room, the download of the video video of the interrogation process in that room will be triggered. This operation is scattered throughout the suspect's interrogation process, which greatly shortens the time for obtaining evidence.
[0117] The specific steps of the intelligent forensics method include:
[0118] Step S1. Wear the RFID tag for the person involved, and obtain the information of the RFID tag through the preset positioning base station to obtain the real-time location of the person involved. The real-time location is calculated according to the timeline to generate the behavior track information of the suspect, and the system automatically records the suspect Changes in the location of people, recording the start time and departure time of each room;
[0119] Step S2. Acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com