Identity legality detection method and device for host and identity detection equipment
A detection method and legality technology, applied in the field of Internet security, can solve problems such as low reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
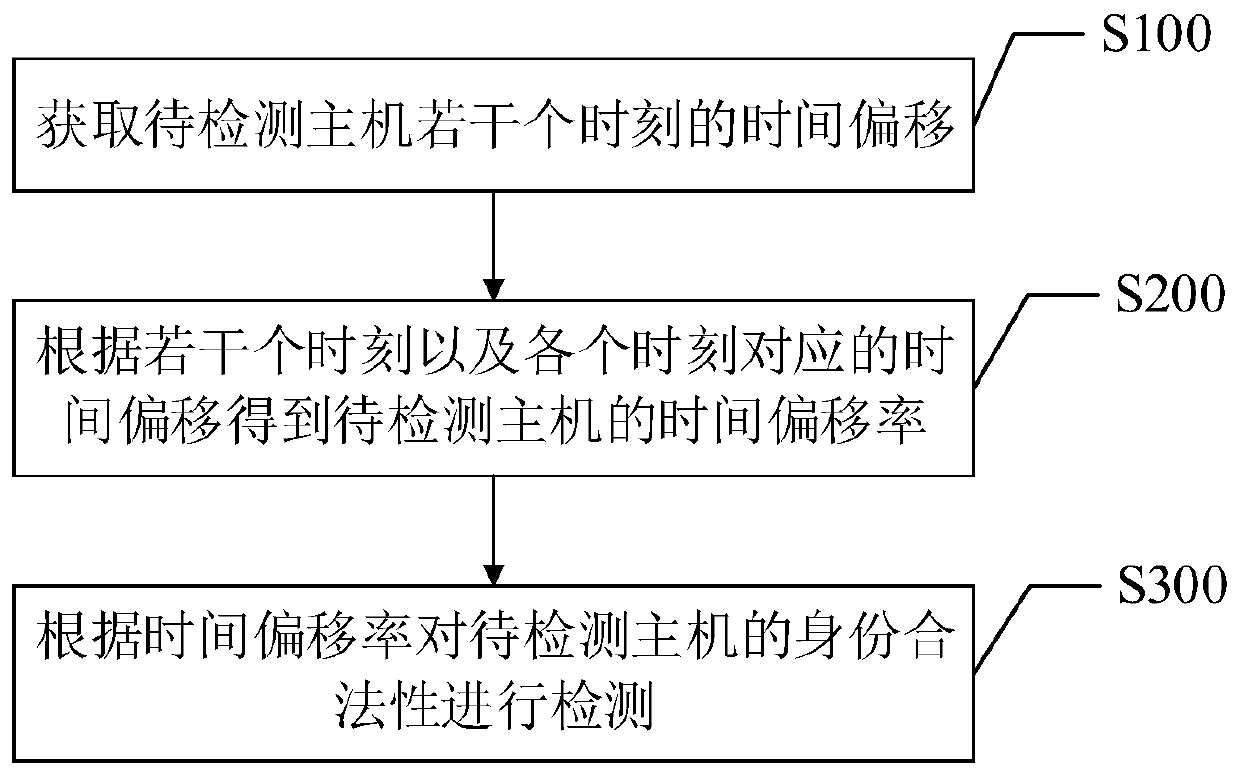
[0031] This embodiment provides a method for detecting the legality of the identity of the host, such as figure 1shown. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here. The process includes the following steps:
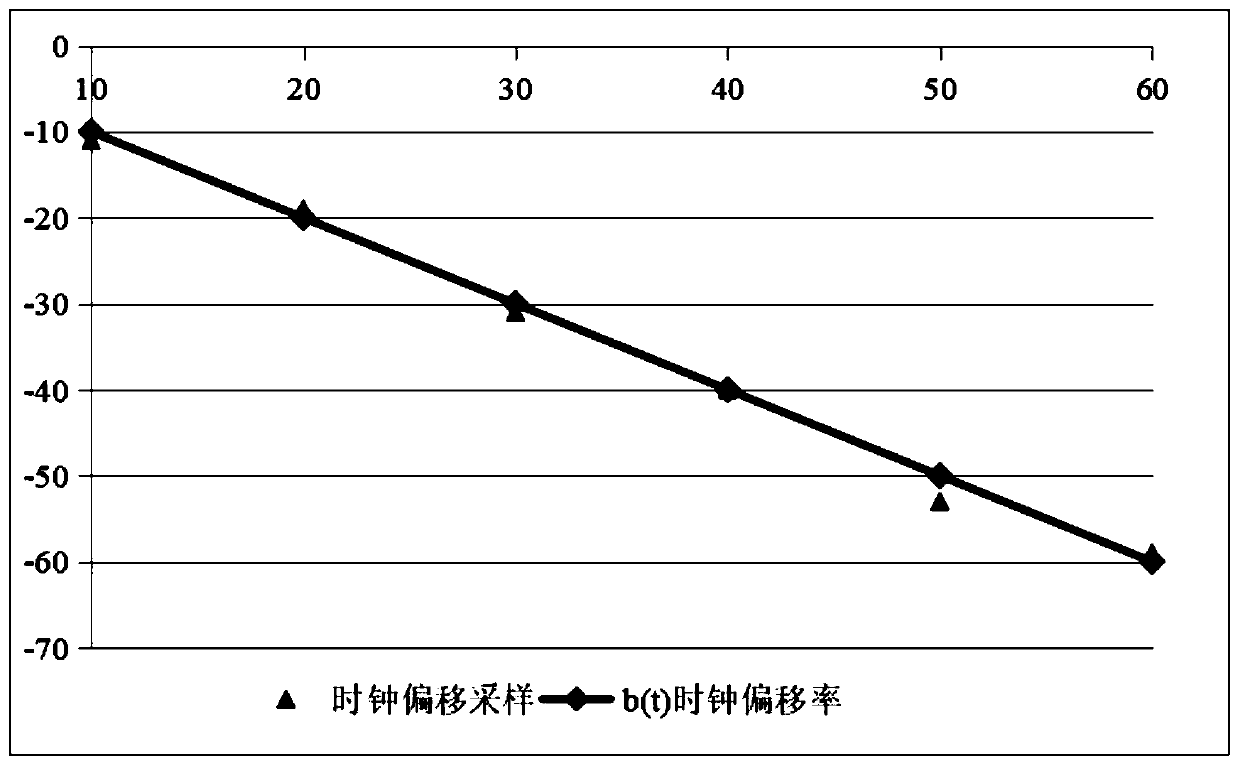
[0032] Step S100, acquiring the time offsets of the host to be detected at several moments. In this embodiment, at least two time offsets of the host to be detected need to be acquired. Specifically, the number of time offsets of the host to be detected to be acquired is represented by character n (n≥2).
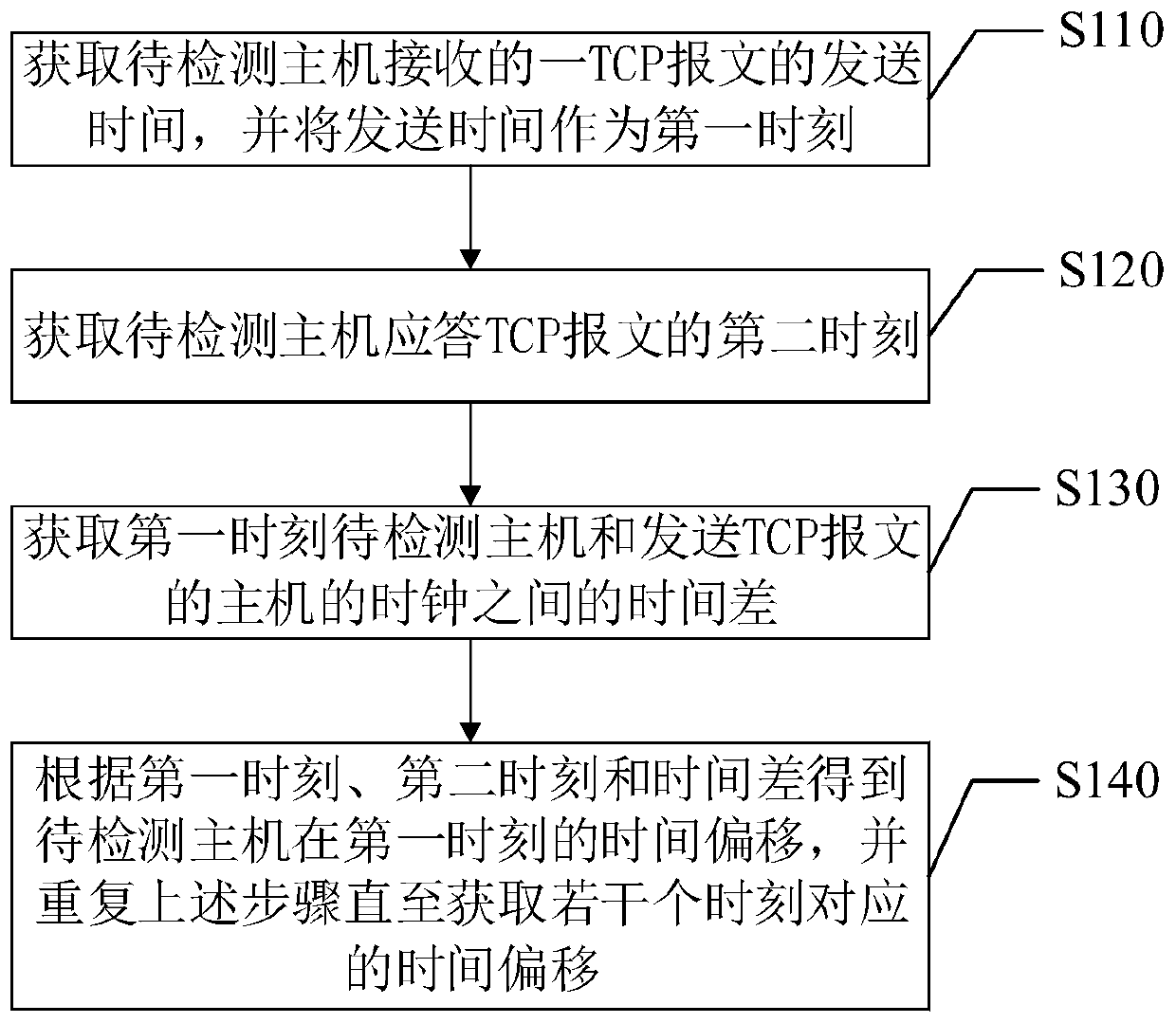
[0033] In a specific example, such as figure 2 As shown, step S100 includes the following steps:
[0034] Step S110, acquire the sending time of a TCP packet received by the host t...
Embodiment 2
[0065] In this embodiment, a device for detecting the legitimacy of an identity of a host is provided, and the device is used to implement the above-mentioned embodiment 1 and its preferred implementation modes, and what has already been described will not be repeated. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
[0066] This embodiment provides a dynamic verification code generation device, such as Figure 6 As shown, it includes: a time offset acquisition module 100 , a time offset rate calculation module 200 and a legality detection module 300 .
[0067] Among them, the time offset acquisition module 100 is used to acquire the time offset of the host to be detected at several moments; the time...
Embodiment 3
[0072] An embodiment of the present invention provides an identity detection device, such as Figure 7 As shown, the identity detection device may include: at least one processor 701 , such as a CPU (Central Processing Unit, central processing unit), at least one communication interface 703 , memory 704 , and at least one communication bus 702 . Wherein, the communication bus 702 is used to realize connection and communication between these components. Wherein, the communication interface 703 may include a display screen (Display) and a keyboard (Keyboard), and the optional communication interface 703 may also include a standard wired interface and a wireless interface. The memory 704 may be a high-speed RAM memory (Random Access Memory, volatile random access memory), or a non-volatile memory (non-volatile memory), such as at least one disk memory. Optionally, the memory 704 may also be at least one storage device located away from the aforementioned processor 701 . The app...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com