Data interaction method and system based on dual-system shared memory
A shared memory and data interaction technology, applied in the field of data interaction to ensure orderliness, prevent data leakage, and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
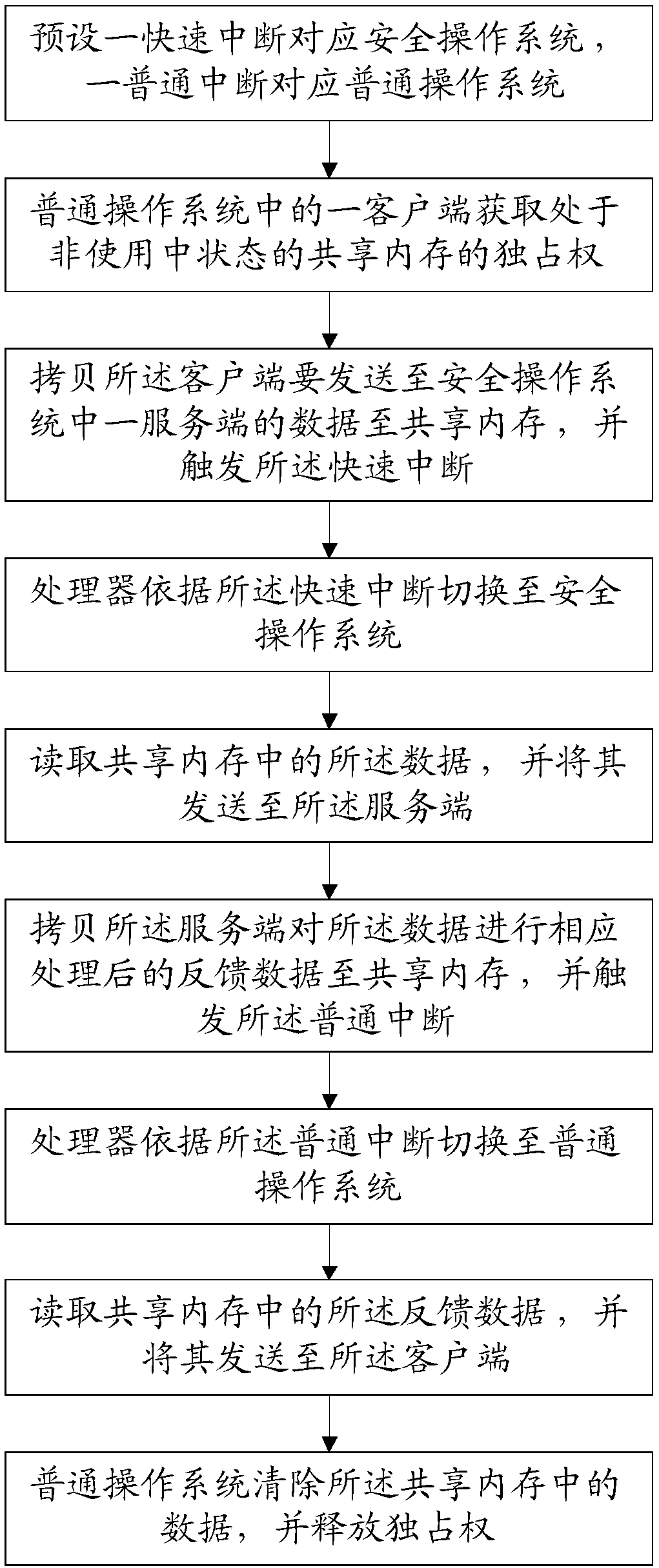
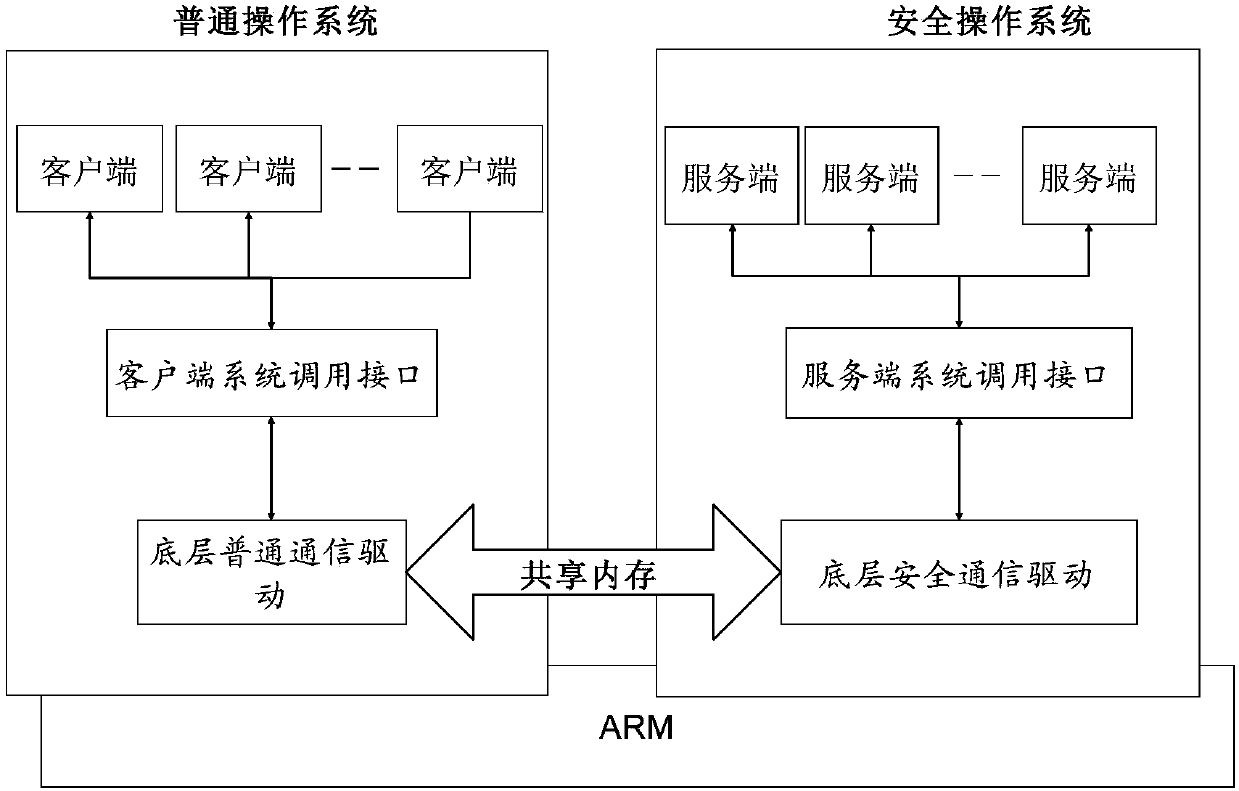
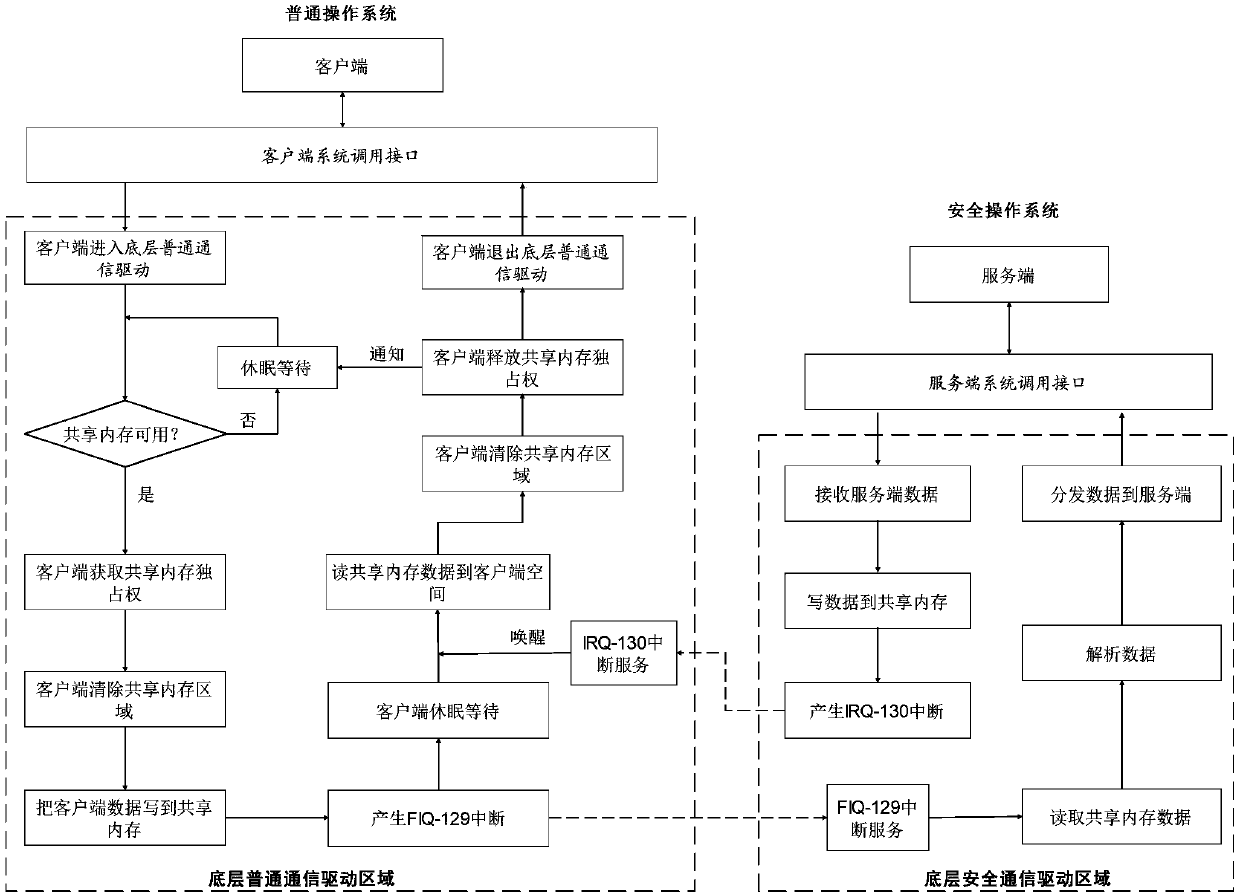
[0100] Please refer to figure 2 and image 3 , this embodiment provides a data interaction method based on the shared memory of the dual systems, which solves the problem of how to coordinate the dual systems and protect data in the shared memory by using the shared memory for communication between the two systems. This embodiment can not only effectively prevent other client programs from reading data in the shared memory, but also coordinate multiple clients and two operating systems to perform orderly operations on shared memory processes.
[0101] This embodiment is based on figure 2 The data communication model of the two systems shown is realized. Call the server system call interface (GPTEE Internal API) through the server program of the security operating system, call the client system call interface (GPTEE Client API) through the client program of the ordinary operating system, and pass the underlying ordinary communication driver of the ordinary operating system ...
Embodiment 2
[0133] This embodiment provides a specific application scenario corresponding to Embodiment 1. The application scenario is that the client A requests the server A to encrypt data.
[0134] Specifically, the following steps may be included:
[0135] 1. Client A enters the doscom-driver area through the GPTEE Client API interface (assuming that the shared memory is idle at this time);
[0136] 2. Client A obtains the exclusive right to shared memory;
[0137] 3. Client A clears the shared memory data;
[0138] 4. Client A encapsulates the data that needs to be sent to server A, and copies the encapsulated data to the shared memory area;
[0139] 5. Client A generates a fast interrupt FIQ-129 (the processor will automatically switch to the safe operating system for operation), and then enters dormancy and waits;
[0140] 6. The safe operating system enters the FIQ-129 fast interrupt service program, and the interrupt service program notifies the tee-driver to read the shared m...
Embodiment 3
[0152] see Figure 5 , this embodiment corresponds to Embodiment 1, and provides a data interaction system based on dual-system shared memory, including:
[0153] The preset module 1 is used to preset a fast interrupt corresponding to a safe operating system, and a common interrupt corresponding to a common operating system;
[0154] In a specific embodiment, the preset module is specifically used to preset a fast interrupt and its corresponding fast interrupt processing program, a normal interrupt and its corresponding normal interrupt processing program, and the fast interrupt processing program is located in the security In the underlying security communication driver of the operating system, the common interrupt handler is located in the underlying common communication driver of the common operating system;
[0155] The obtaining module 2 is used for a client in the common operating system to obtain the exclusive right of the shared memory in the non-use state;
[0156] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com