Hot patching method and hot patching device
A hot patch and patch file technology, applied in software deployment, platform integrity maintenance, etc., can solve the problems of increasing the security risk of patch files, unable to verify the signature of patch files, unable to guarantee the security of patch files, etc., to prevent attacks and ensure High reliability and safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
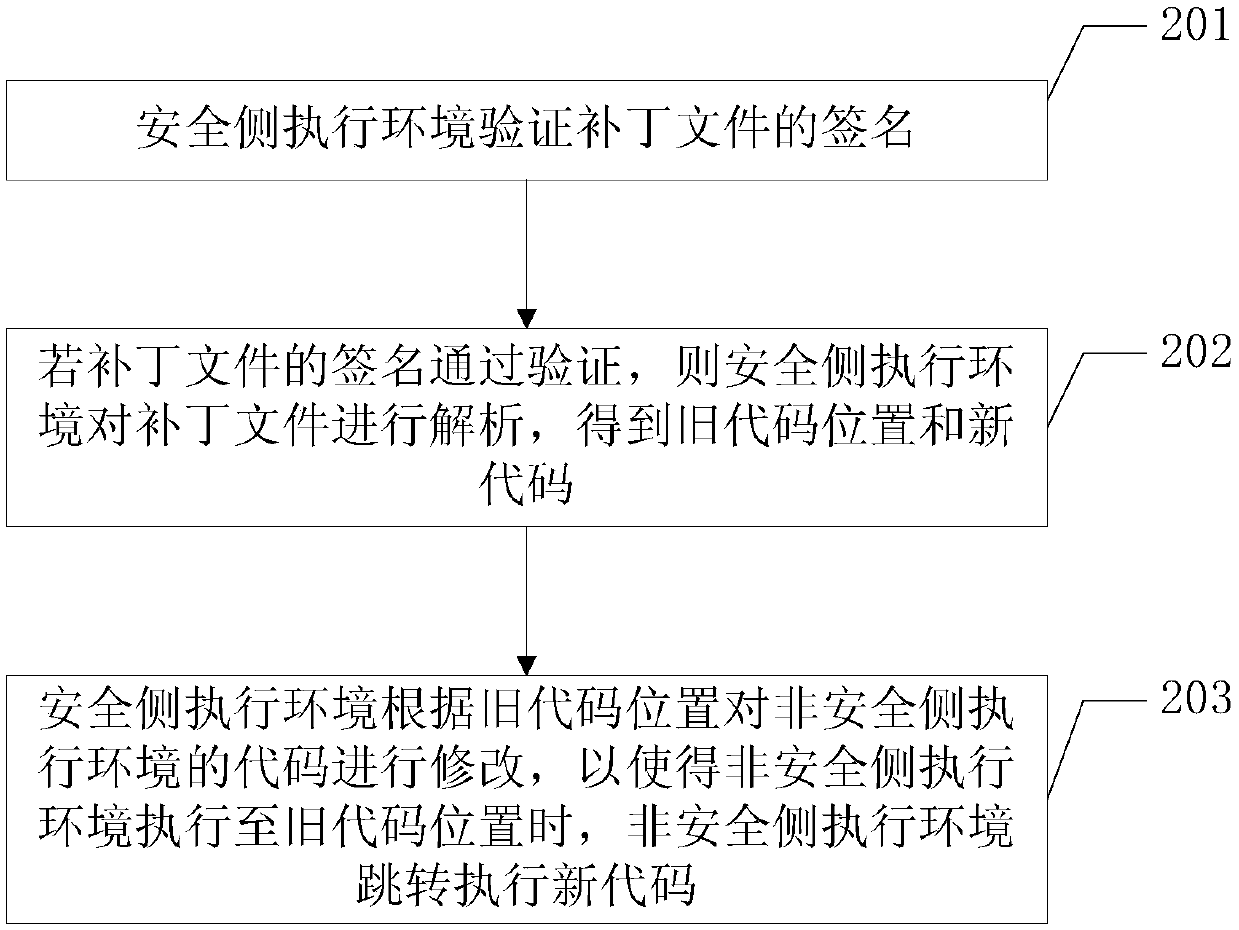
[0051] Embodiment one, such as figure 2 As shown, an embodiment of the hot patch method of the present application includes:
[0052] 201. The security side executes the signature of the environment verification patch file.
[0053] The execution environment on the security side (for example, the trusted execution environment TEE above) uses the private key to check the signature of the patch file to verify whether the issuer of the patch file is credible. If the patch file passes the signature verification, it is determined that the patch file If the issuer of the patch file is a trusted issuer, the execution environment of the security side executes step 202; if the signature verification fails, it is determined that the issuer of the patch file is an untrusted issuer, and the execution environment of the security side stops loading the patch file. In addition, the patch file is used to repair security vulnerabilities of codes in the execution environment of the non-secure ...
Embodiment 2
[0069] Embodiment 2, as shown in Figure 3 (a), another embodiment of the hot patch method of the present application includes:
[0070] 301. The execution environment on the non-secure side sends the patch file to the secure executable environment.
[0071] When the code in the non-secure side execution environment has security vulnerabilities that need to be repaired, the non-secure side execution environment sends the patch file for repairing the above-mentioned security holes to the secure executable environment, so that the security side execution environment executes the loading of the patch file operate. Specifically, the Rich OS sends the patch file from the REE to the TEE.
[0072] 302. The security side executes the signature of the environment verification patch file.
[0073] 303. If the signature verification of the patch file passes, the security side execution environment analyzes the patch file to obtain the old code location and the new code.
[0074] Step 3...
Embodiment 3
[0098] Embodiment three, such as Figure 4 Shown, an embodiment of hot patch device among the present application, comprises:
[0099] Integrity measurement unit 401, used to verify the signature of the patch file;
[0100] The parsing unit 402 is configured to parse the patch file to obtain the old code location and the new code if the signature verification of the above patch file is verified;
[0101] The modifying unit 403 is configured to modify the code of the non-secure execution environment according to the position of the old code, so that when the non-secure execution environment executes to the position of the old code, it jumps to execute the new code.
[0102] In one example, such as Figure 5 As shown, the above hot patch device also includes:
[0103] The configuration unit 504 is configured to configure the physical memory of the update code to be non-writable in a non-secure state.
[0104] In one example, such as Figure 5 As shown, the above system also...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com