A cross-regional vulnerability library sharing and cooperative processing system and method
A technology of collaborative processing and vulnerability database, which is applied in the field of cross-regional vulnerability database sharing and collaborative processing systems, and can solve problems such as multiple known vulnerabilities and configurations, economic losses, and violations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Embodiments of the present invention will be described in detail below. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
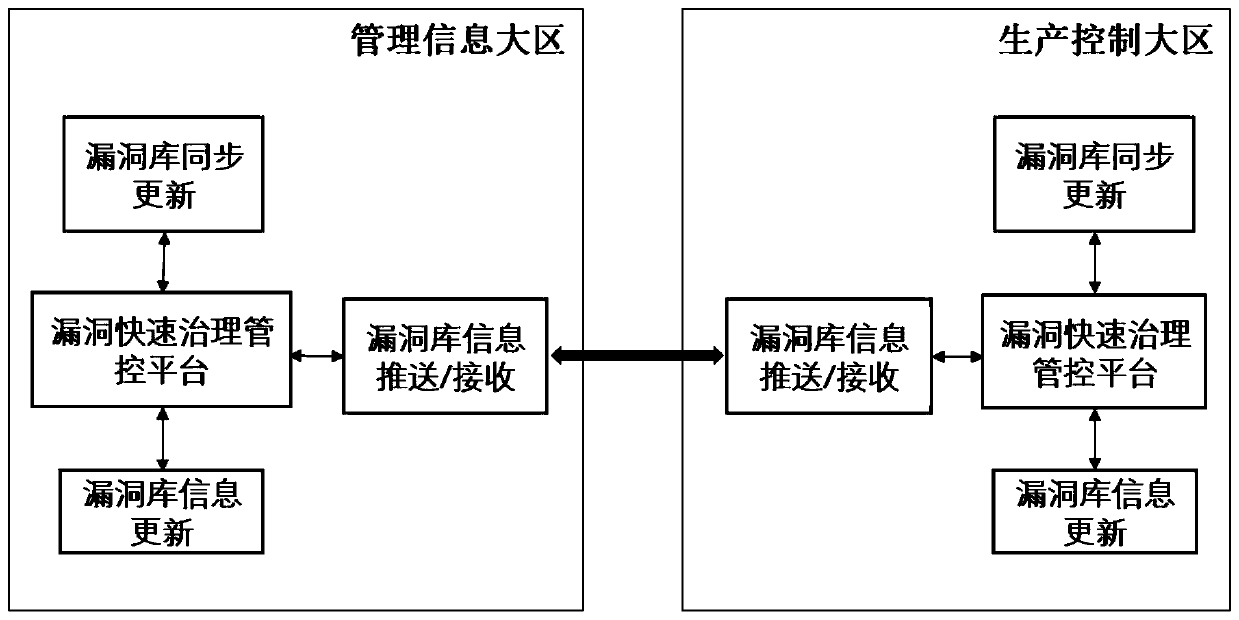
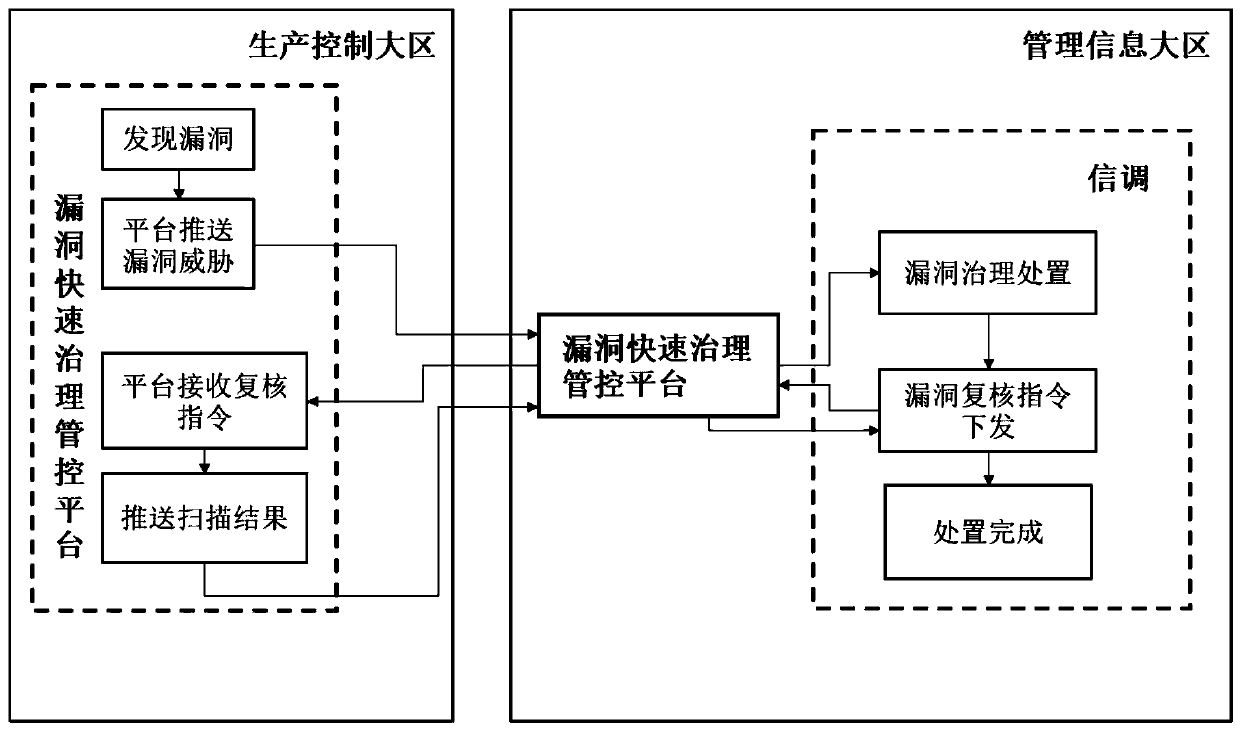
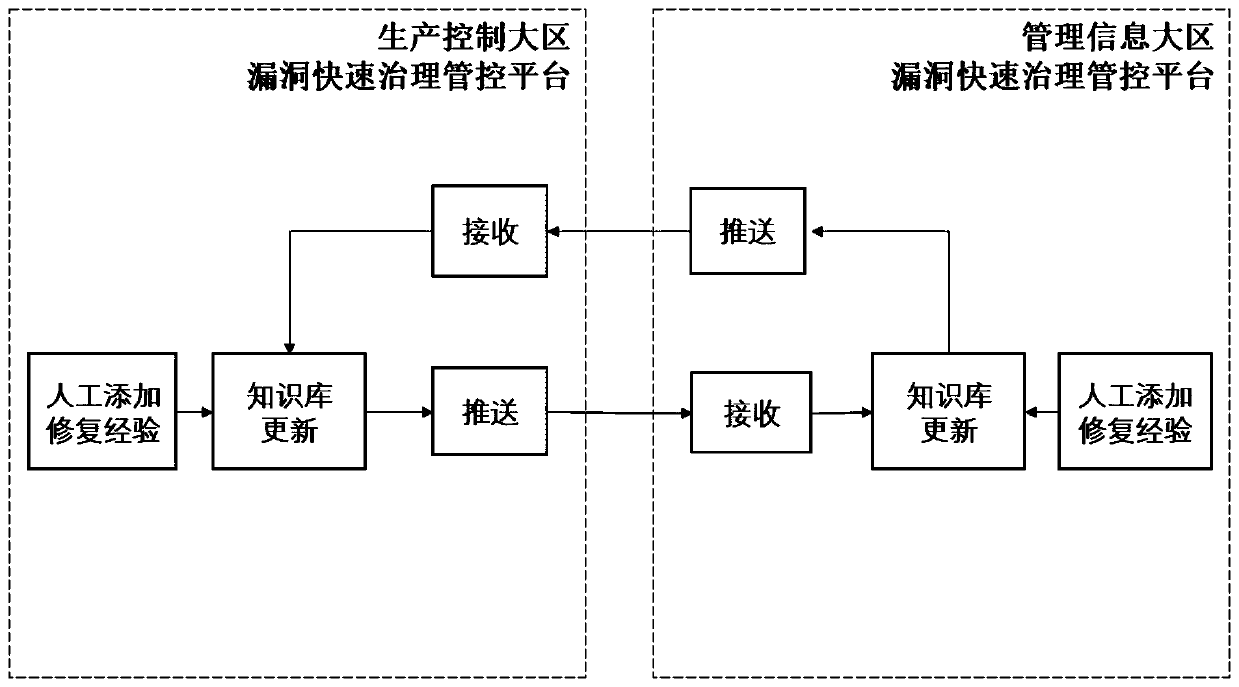
[0045] refer to figure 1 , in one embodiment, a cross-regional vulnerability library sharing and collaborative processing system, including a production control area and a management information area with respective vulnerability rapid governance management and control platforms, the production control area has no Internet connection, and There is an electric power dedicated network security isolation device between the production control area and the management information area, and the vulnerability library information of the vulnerability rapid management and control platform is shared between the two areas through a cross-region vulnerability library synchronization mechanism;
[0046] Among them, the vulnerability library of the rapid vulnerabilit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com