A detection method of message injection attack for vehicle CAN bus
A CAN bus and detection method technology, applied in the field of information security, can solve the problems of missed detection of attack data frames, discarding, lack of security mechanisms, etc., to avoid personal safety threats and property losses, and ensure real-time effects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings.
[0036] The normal communication of a certain identifier on the vehicle CAN bus includes the following features.
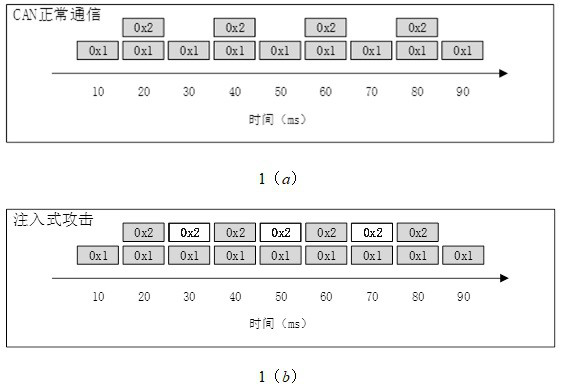
[0037] Periodic feature: In order to ensure the real-time performance and robustness of the system, the ECU connected to the CAN bus periodically sends data frames to the CAN bus. Such as figure 1 As shown, the data frame with the identifier 0x1 appears on the bus every 10ms, and the data frame with the identifier 0x2 appears on the bus every 20ms.
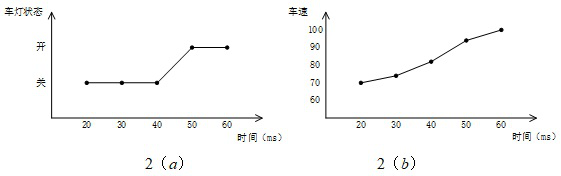
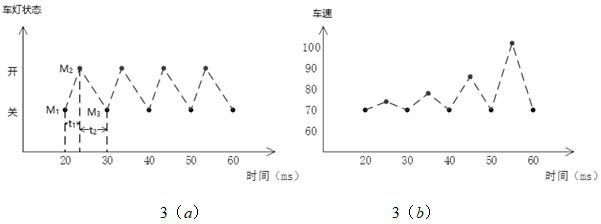
[0038] Stability feature: Over a period of time, the change trend of the data frame data segment with the same identifier does not change much between becoming larger / smaller / unchanged. Such as figure 2 ( a ), the state of the message representing the car light will be relatively stable in a short period of time instead of switching between two states quickly; the trend of the value representing the speed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com