blacklist processing method and system based on a POS machine
A POS machine and processing method technology, applied in the field of data processing, can solve the problems of poor user experience, inability to remove duplicates, and large traffic, and achieve the effects of reducing time consumption, improving user experience, and solving storage space.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
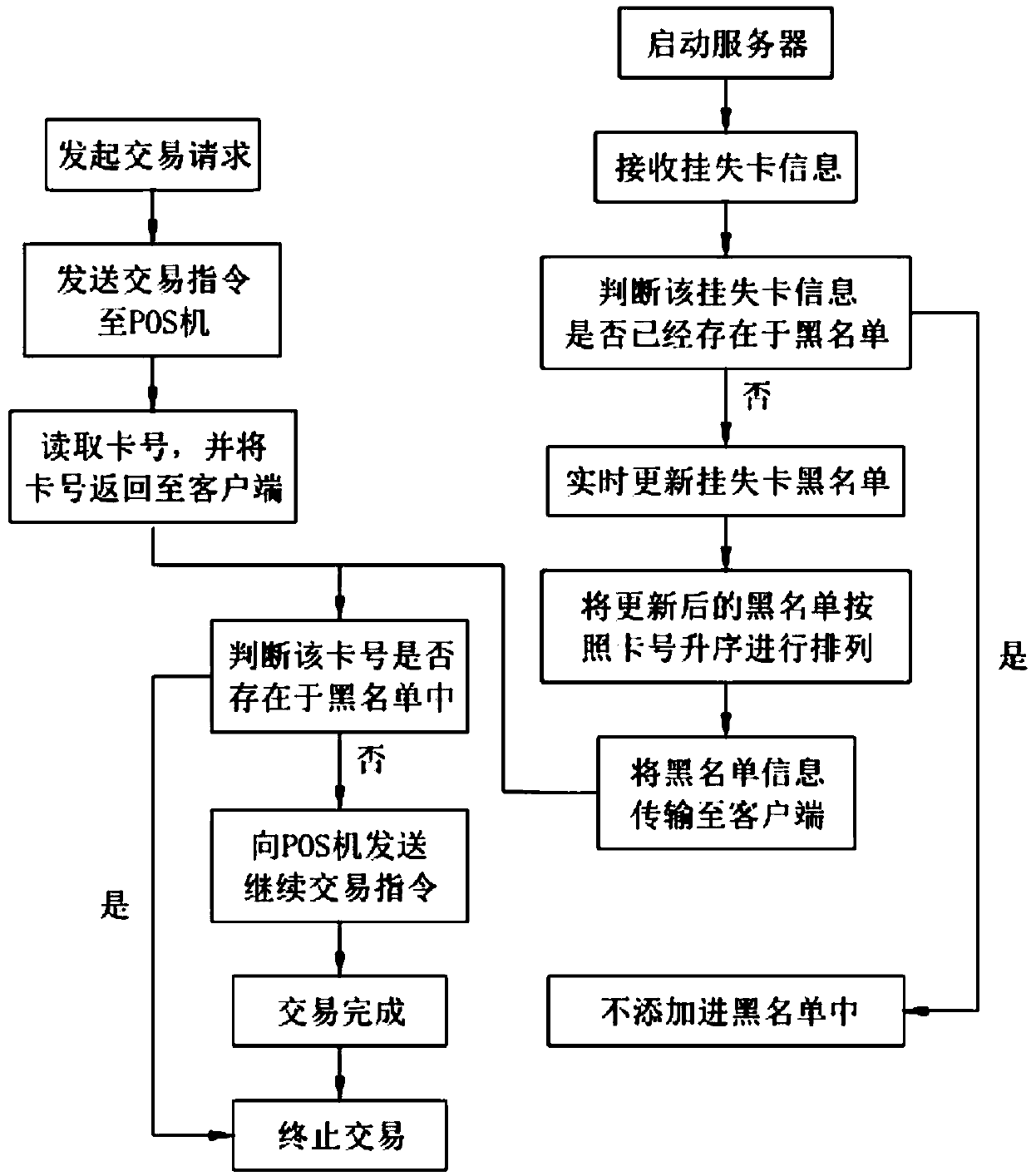
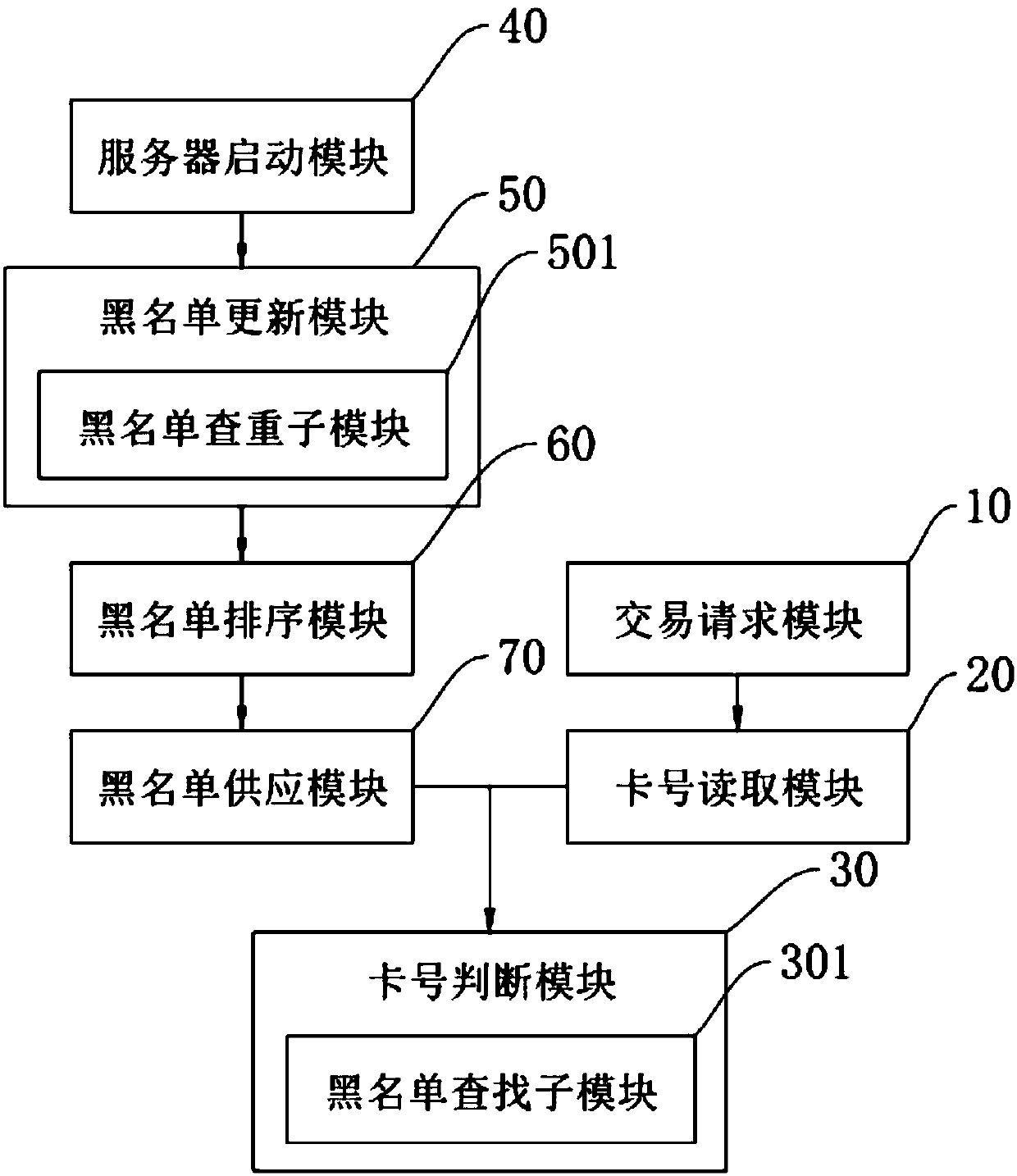
[0052] Such as figure 1 Shown, a kind of blacklist processing method based on POS machine comprises the following steps:
[0053] a. Receive a transaction request, convert the transaction request into a transaction instruction, and send it to the POS machine;
[0054] b. Read the card number and return the card number to the client;
[0055] c. Determine whether the card number exists in the blacklist, if yes, terminate the transaction; if not, send a continuation transaction instruction to the POS machine.
[0056] In this embodiment, the client adopts the mode of PC+POS machine, or PC+password keyboard (SP30 and the like); the logic of directly discriminating the blacklist of the traditional POS machine is modified to the POS machine feedback card number, which is judged by the PC, and then The PC side decides the follow-up transaction steps (blacklist to terminate the transaction or the whitelist to continue the transaction); the blacklist download and judgment mechanism ar...
Embodiment 2
[0058] On the basis of embodiment 1, this embodiment also includes the following steps before said step a:
[0059] S10. Receive a server startup instruction, and start the server;
[0060] S20. Receive the card loss report information, and update the card loss report blacklist in real time;
[0061] S30. Arranging the updated blacklist in ascending order of card numbers;
[0062] S40. Transmit the updated and sorted blacklist information to the client.
[0063] In this embodiment, the client is used to separate the blacklist download part and make it into a separate module, which can be a PC terminal or an independent thread developed by a POS machine; therefore, the problem of storage space is completely solved; abandoning ISO8583, Using a custom simple protocol for downloading saves a lot of traffic and reduces a lot of interaction (the size of each download package can reach several M); at the same time, because there may be tens of thousands of connections (tens of thou...
Embodiment 3
[0065] In this embodiment, on the basis of Embodiment 2, the step S20 also includes the following steps:
[0066] If new loss reporting card information is received, it is judged whether the loss reporting card information already exists in the blacklist, if yes, it is not added into the blacklist; if not, it is added into the blacklist, and arranged according to step S30. Sorting and deduplication by the server can solve the problem that the blacklist data cannot be sorted, the downloaded blacklist data is out of order, and each blacklist judgment needs to traverse the entire record, and it solves the problem that it cannot be deduplicated, which may cause blacklist files to appear Several problems with the same data reduce time-consuming and improve user experience.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com