Cloud storage outsourced decryption attribute-based encryption method capable of limiting access times
A technology of attribute-based encryption and restricted access, applied in the field of cloud storage outsourcing decryption attribute-based encryption, which can solve the problems of not supporting limited access times, high overhead, and reduced decryption overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
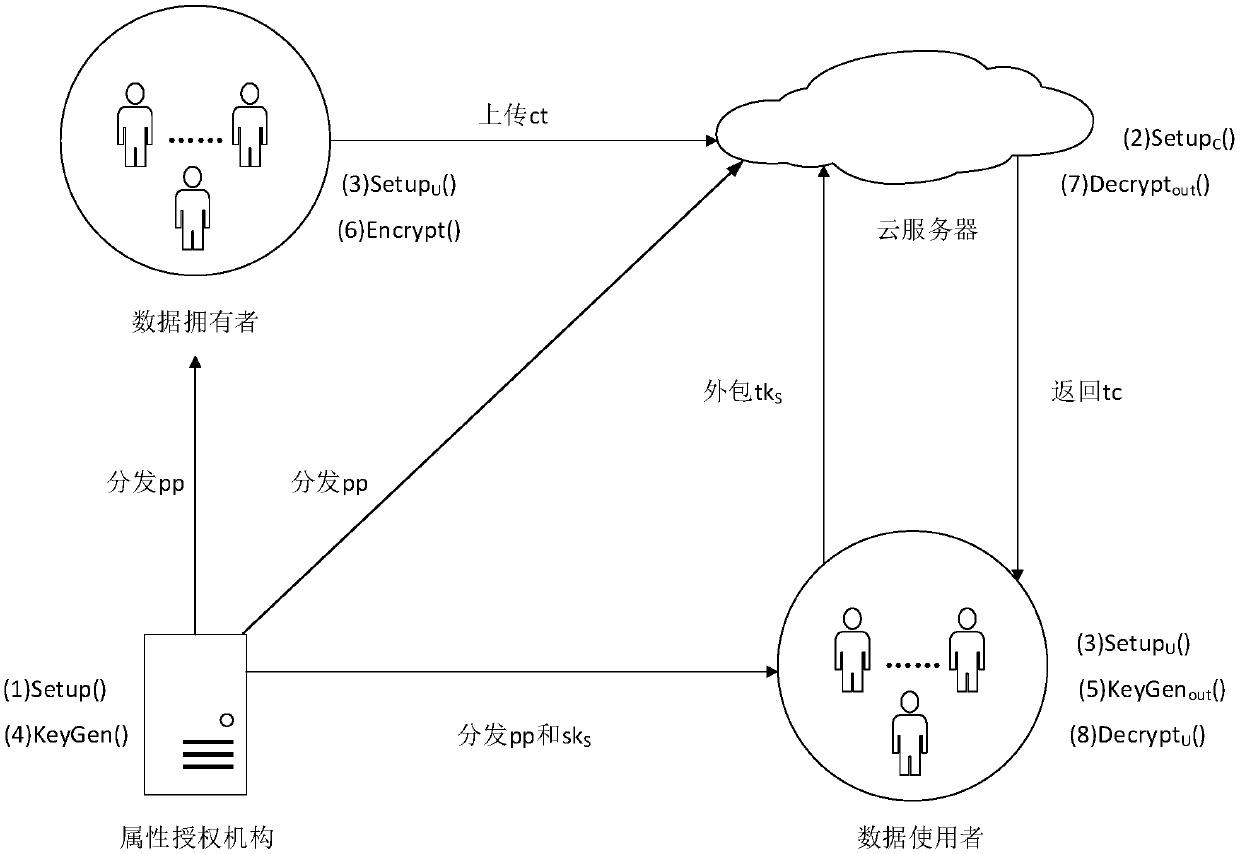
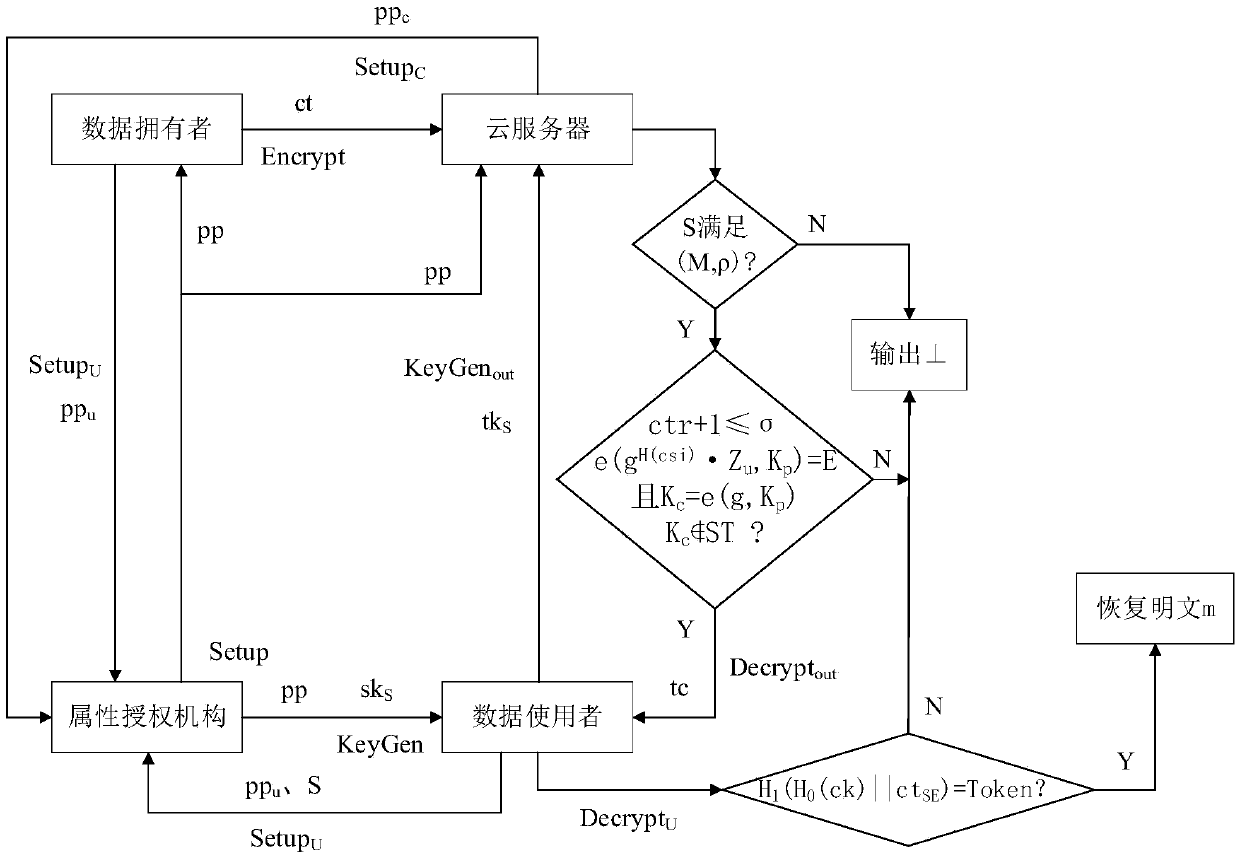
[0052] The embodiment of the present invention provides a cloud storage outsourcing decryption attribute-based encryption method that can limit the number of visits within a certain period of time. The method uses a verifiable random function to limit the number of visits of the user, and uses outsourcing computing technology to outsource the decryption operation of the client to the cloud. Execution, use key blinding technology to realize safe decryption outsourcing service, use the verification token generated by cryptographic hash function to verify the correctness of outsourced decryption, and realize the public verification of the correctness of outsourced decryption in attribute-based encryption.
[0053] The cloud storage data sharing system in the present invention involves 4 entities: attribute authority, data owner, cloud server and data user, see figure 1, the attribute authority is used to generate system public parameters and generate a decryption key according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com