Stack safety detection method and device and mobile equipment
A detection method and security technology, applied in the security field, can solve problems such as inaccurate detection of compilation protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
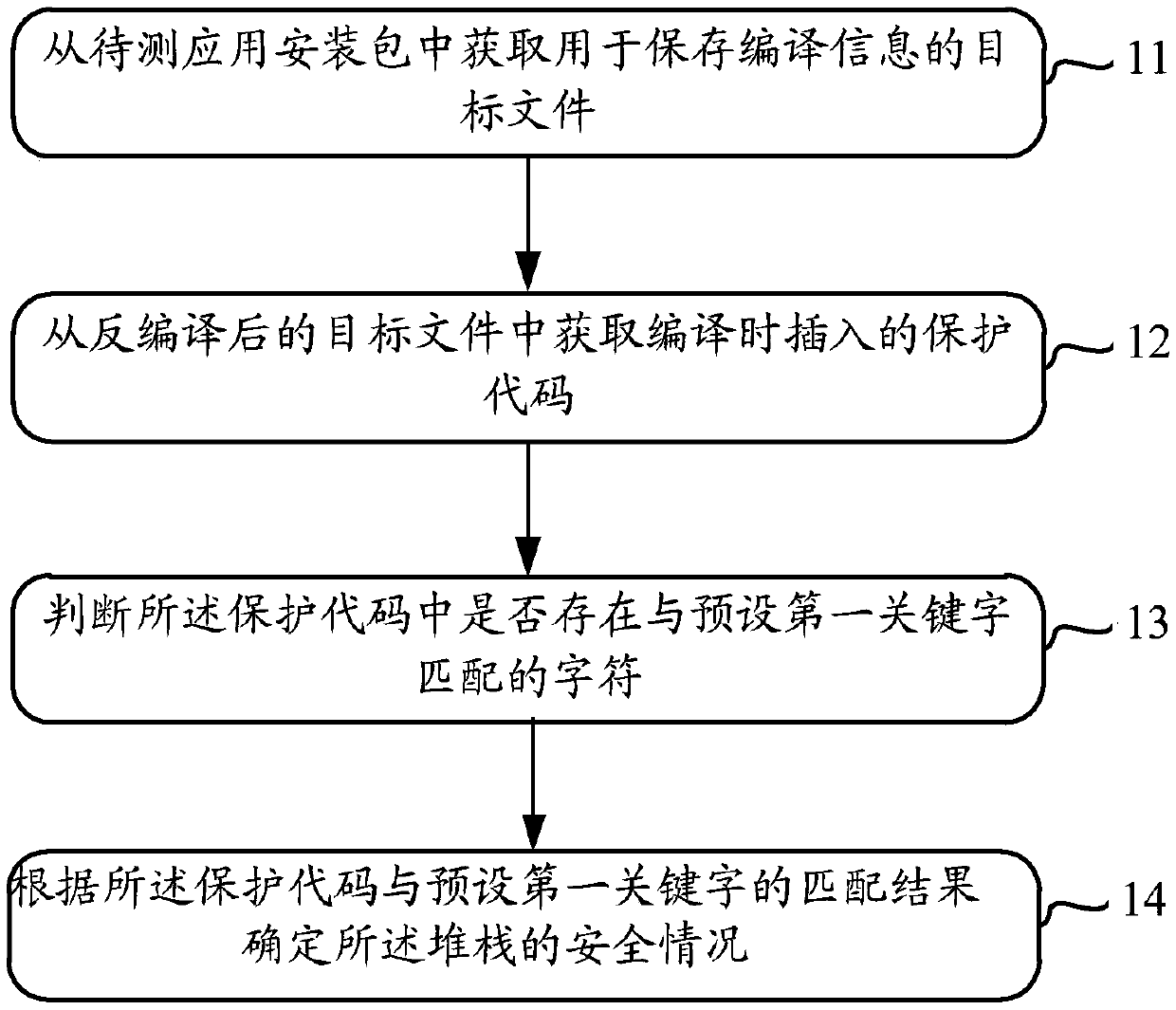
[0032] In order to solve the problem in the prior art that the protection code only inserts the protection code for a certain type of specific function and checks the protection code in the process of compiling the stack protection, the rest of the functions are safe by default (that is, no protection code is inserted for the rest of the functions), resulting in only When a specific function is attacked, the attack can be accurately detected; if other functions are attacked, the method cannot accurately detect the attack. The embodiment of the present invention provides a stack security detection method.
[0033] The execution subject of the method may be a server used to detect the application installation package or a detection system (or detection program) running on the server; or, the execution subject of the detection method of the stack security may be a The client (or client) of the package, etc.
[0034] For the convenience of describing Embodiment 1 of the present ap...
Embodiment 2
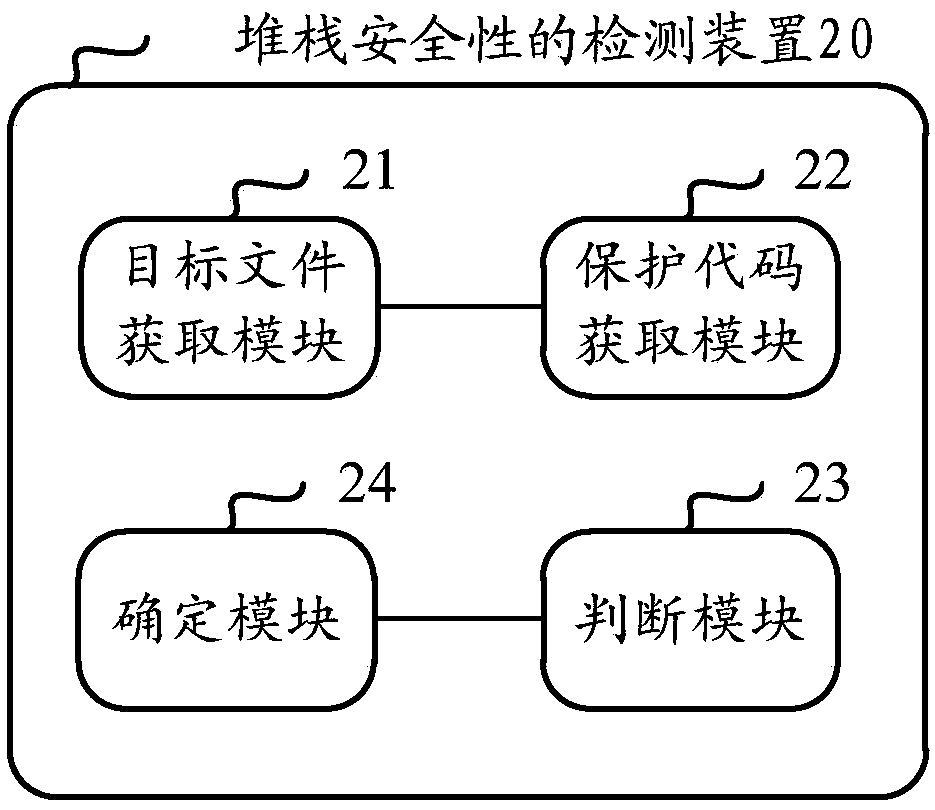
[0071] In order to solve the problem existing in the prior art that the stack security cannot be accurately detected, an embodiment of the present invention provides a stack security detection device 20. The specific structural diagram of the device is as follows figure 2 Shown, comprise target file acquisition module 21, protection code acquisition module 22, judgment module 23 and determination module 24, the function of each module is as follows:
[0072] The target file obtaining module 21 is used to obtain the target file used to save the compilation information from the application installation package to be tested;
[0073] Preferably, in the implementation of the present invention, the target file acquisition module can include:
[0074] The source file acquisition unit is used to decompress the installation package of the application to be tested to obtain the source file of the application;
[0075] The target file obtaining unit is used to obtain the target file f...
Embodiment 3
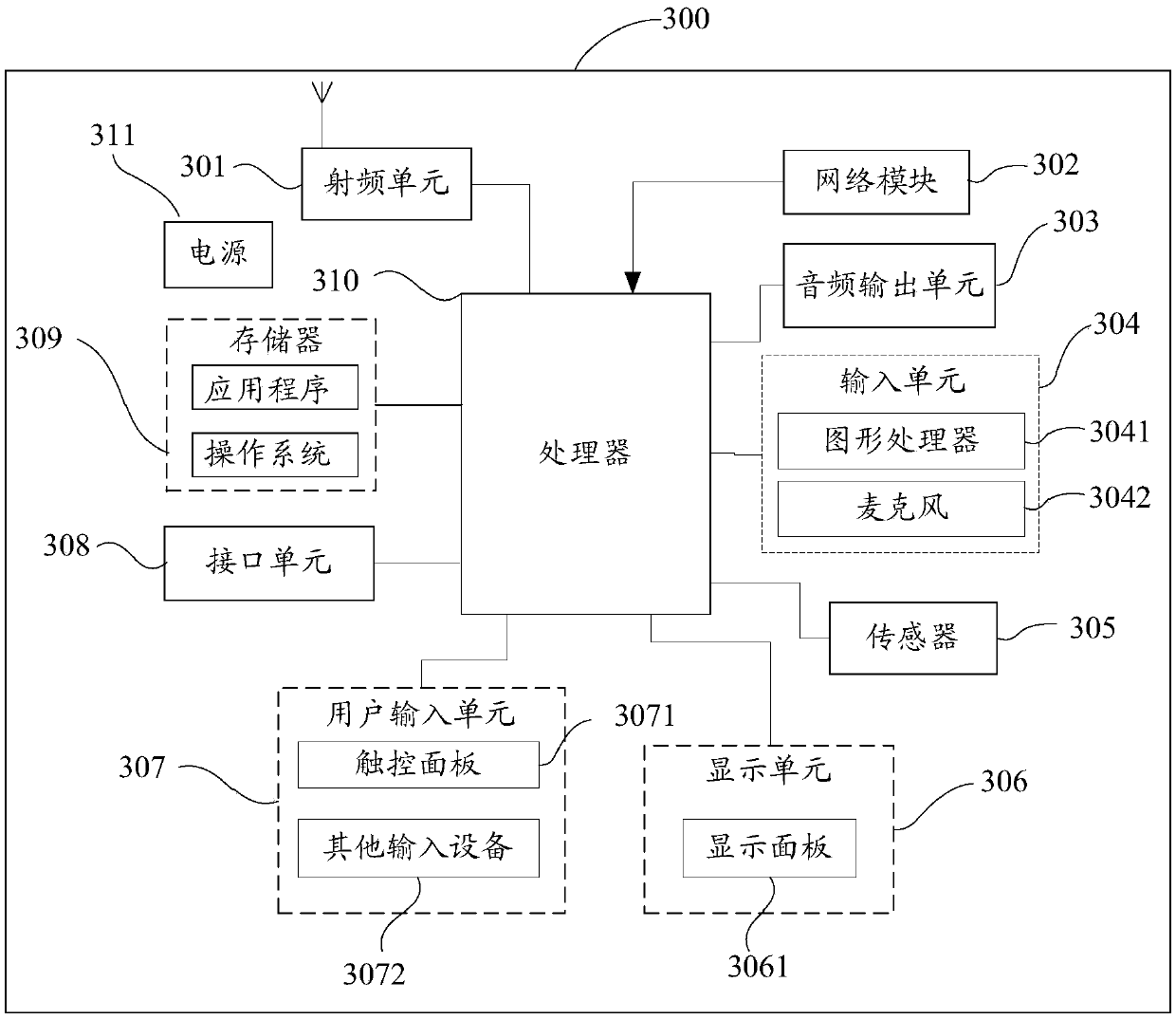
[0087] Preferably, the embodiment of the present invention also provides a mobile device 300, including image 3 The shown processor 310, the memory 309, and the computer program stored in the memory 309 and operable on the processor 310, when the computer program is executed by the processor 310, realize the stack security described in the above-mentioned embodiments Each process of the detection method can achieve the same technical effect, and will not be repeated here to avoid repetition.
[0088] image 3 A schematic diagram of the hardware structure of a smart device for realizing various embodiments of the present invention, the smart device 300 includes but not limited to: a radio frequency unit 301, a network module 302, an audio output unit 303, an input unit 304, a sensor 305, a display unit 306, User input unit 307, interface unit 308, memory 309, processor 310, power supply 311 and other components. Those skilled in the art can understand that, image 3 The str...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com