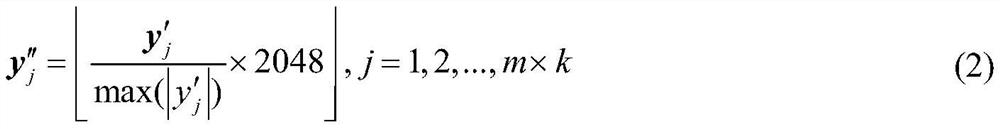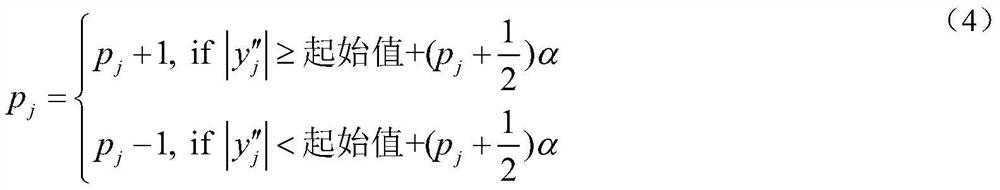A Separable Encryption Domain Information Hiding Method
An information hiding and encryption domain technology, applied to key distribution, can solve problems such as uncertainty, data extraction image recovery error, limited effective embedding capacity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0080] In order to make the purpose, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below.
[0081] We choose Matlab as the software platform, and programming realizes the design of the scheme of the present invention. The implementation process selects the 512×512 standard test image “Lena” as the image to be protected, assuming that the selected observation rate MR=0.25, and the block size B=8.
[0082] The specific operation steps are:
[0083] Ⅰ. The image encryption and secret information embedding part at the sending end, including the following steps:
[0084] The first step is the encryption process based on Block Compressive Sensing (BCS):
[0085] (1). Read in a size 512 * 512 image I that needs to be protected, and divide the image into a plurality of non-overlapping, 8 * 8 size image blocks;
[0086] (2). Arrange each image block into a 64×1 column vector x i , i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com