A privacy protection processing method based on modulus component homomorphism
A technology of privacy protection and processing methods, applied in the field of trusted computing, can solve problems such as data leakage, user-side privacy threats, etc., and achieve the effect of fast computing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
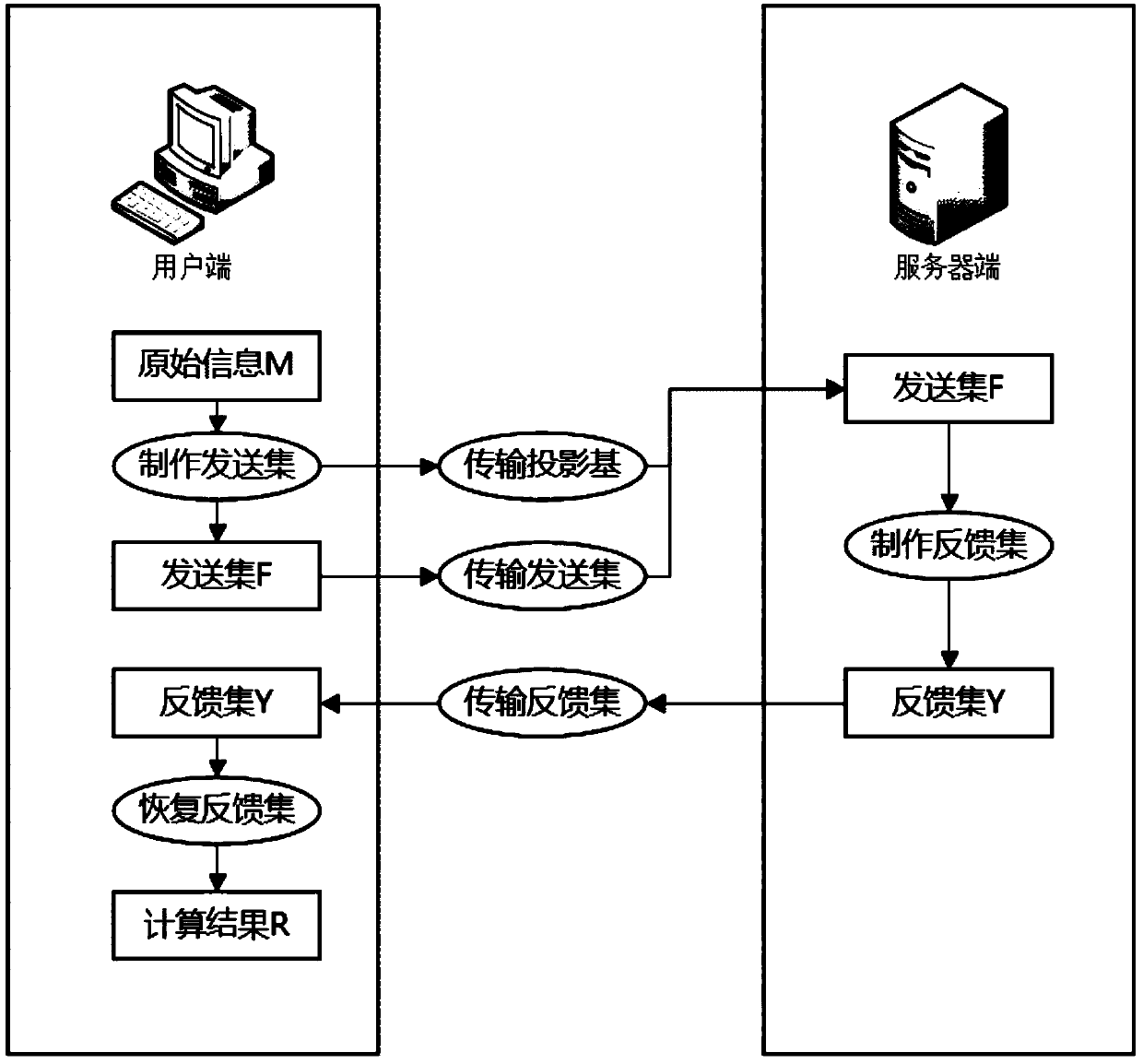
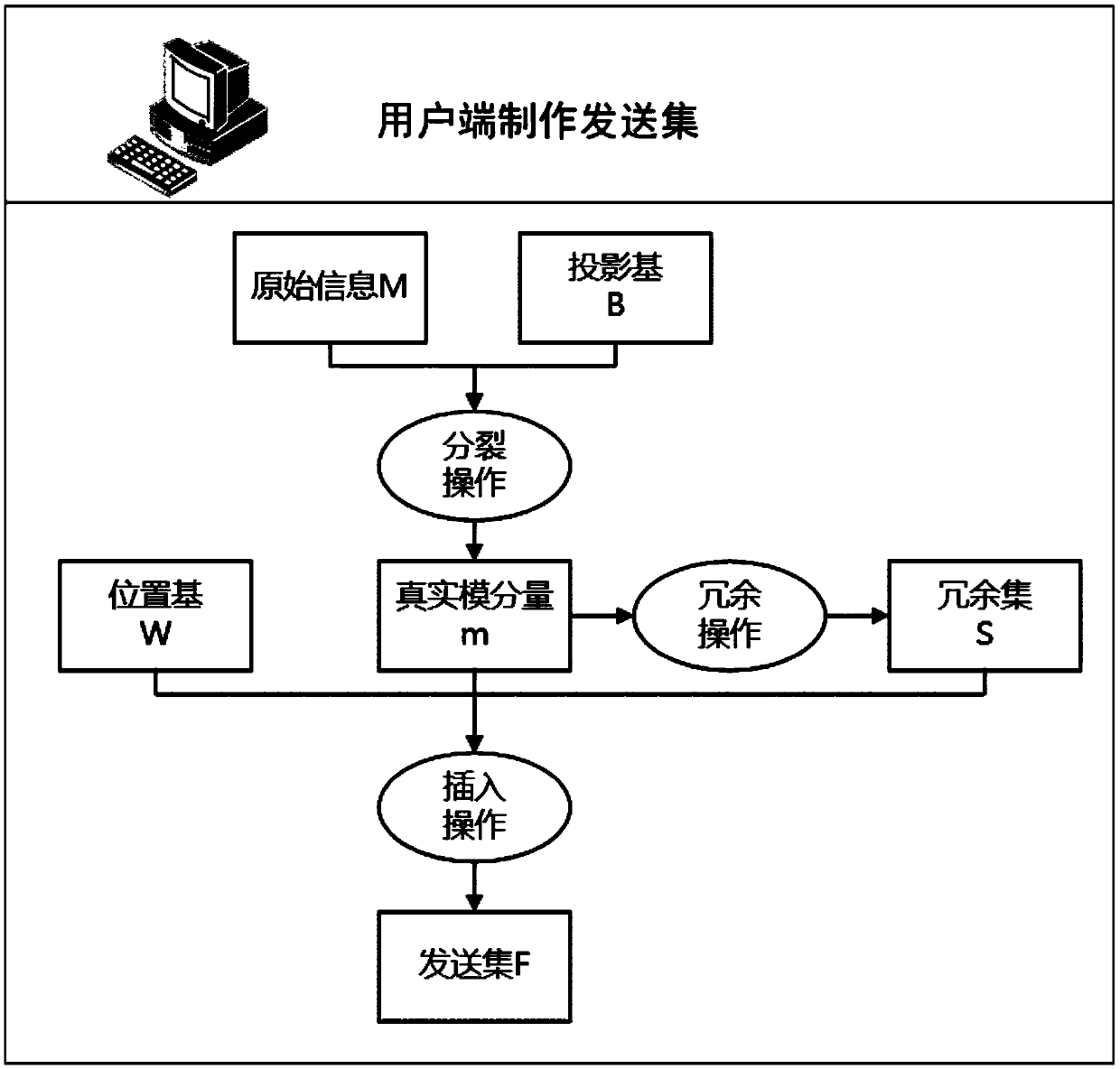
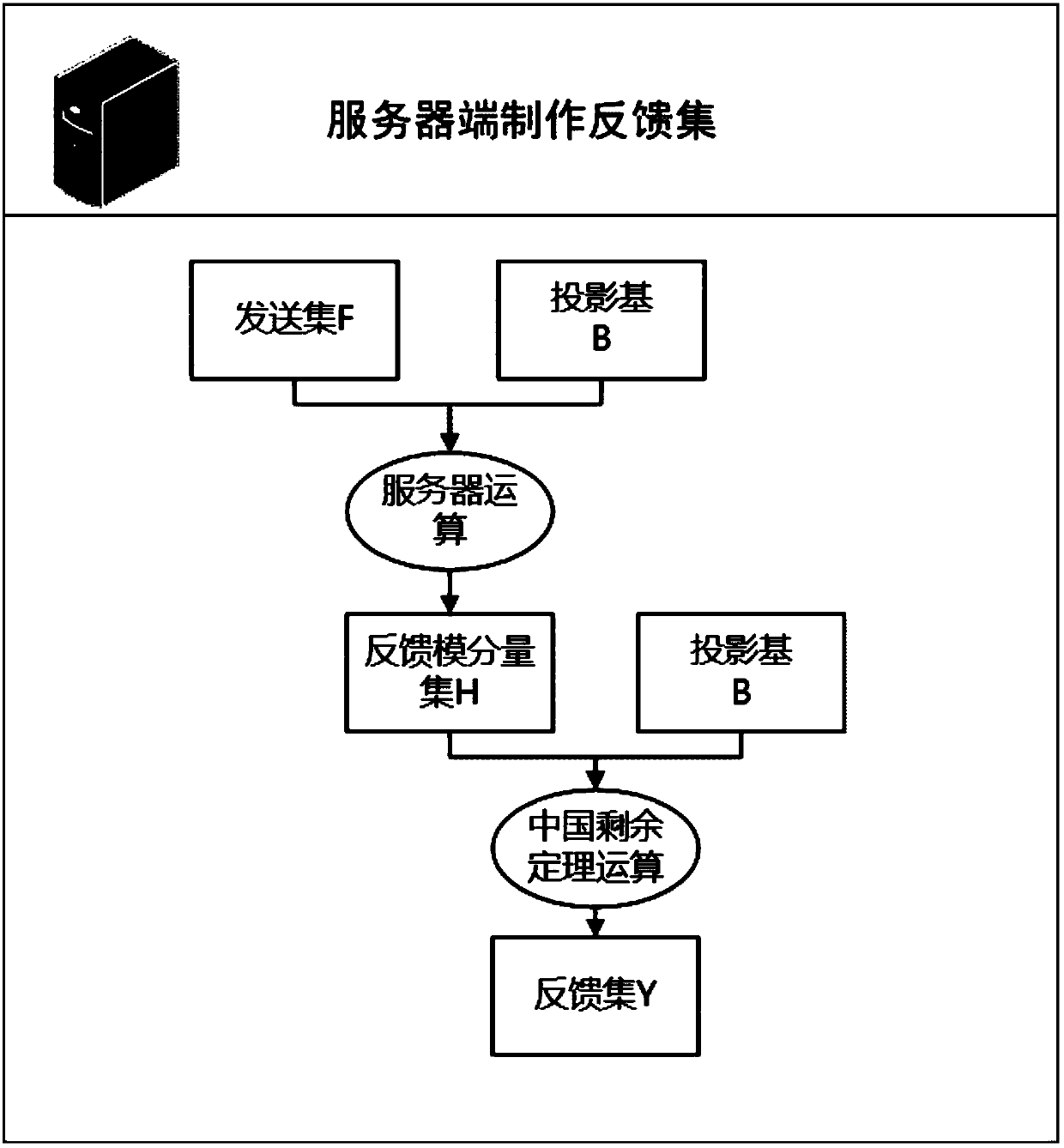
[0036] Such as figure 1 As shown, in the present invention, the client uses the original information to perform modular operations on a group of bases, inserts the obtained modular components into redundant information, and then sends them to the server. The server cannot distinguish which are real modular components and which is redundant information. Due to the homomorphism of modular operations (addition, subtraction, multiplication), the operation on the modular components is equivalent to the operation on the original information. After obtaining the calculation results, the server side obtains the feedback results according to the Chinese remainder theorem, and the user terminal receives the feedback results. The effective information is taken out, and the final server-side calculation result is obtained through calculation. A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com