Mobile terminal trusted isolation environment core control method
A core control and mobile terminal technology, applied in program control design, instruments, electrical and digital data processing, etc., can solve the problem that resources and data cannot be truly isolated, improve scalability and portability, and ensure security. , the effect of reducing security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the purpose, advantage and technical solution of the present invention clearer, the present invention will be further described in detail through specific implementation descriptions below.
[0020] For the convenience of description, some abbreviations used in the present invention will be introduced first.
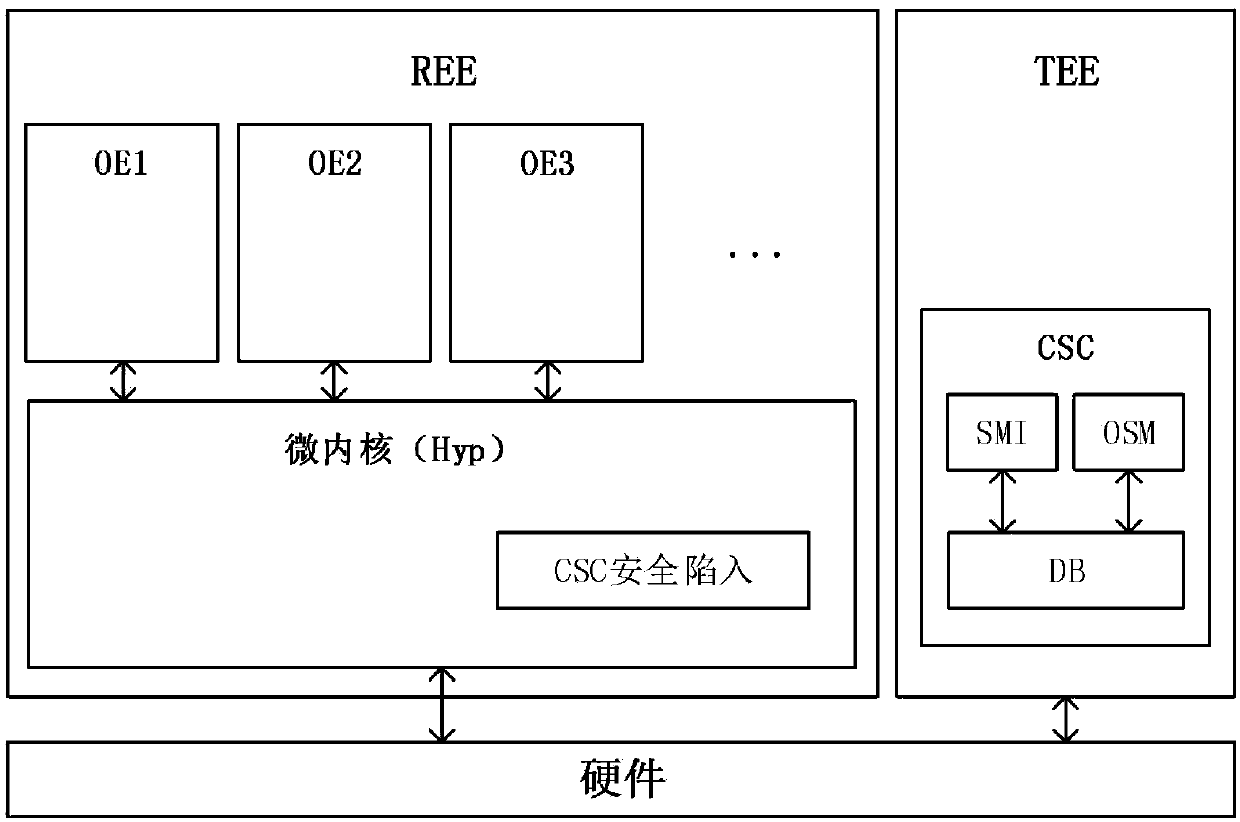
[0021] CSC Core Security Control Core Security Controller
[0022] Hyp Hypervisor microkernel
[0023] SMI Security Memory Isolation Secure Memory Isolation
[0024] TEE Trusted Execution Environment Trusted execution environment
[0025] OE Operating Environment Operating environment
[0026]OMM Operating Status Monitor operating status monitoring
[0027] The present invention is mainly to construct a general core control framework of high-trust mobile terminal isolation execution environment. In this framework, TrustZone and virtualization security isolation are combined, and SMI, OSM and corresponding security policies of TrustZone in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com