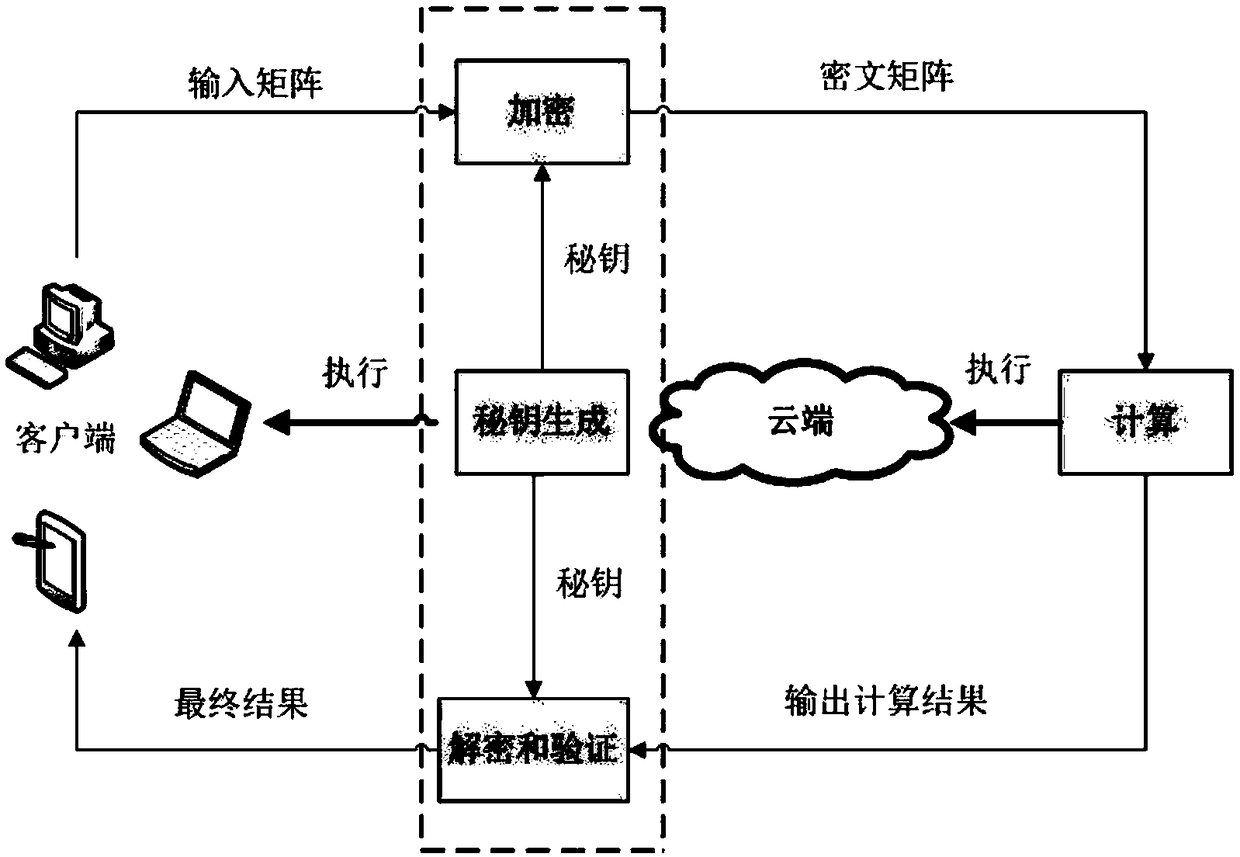
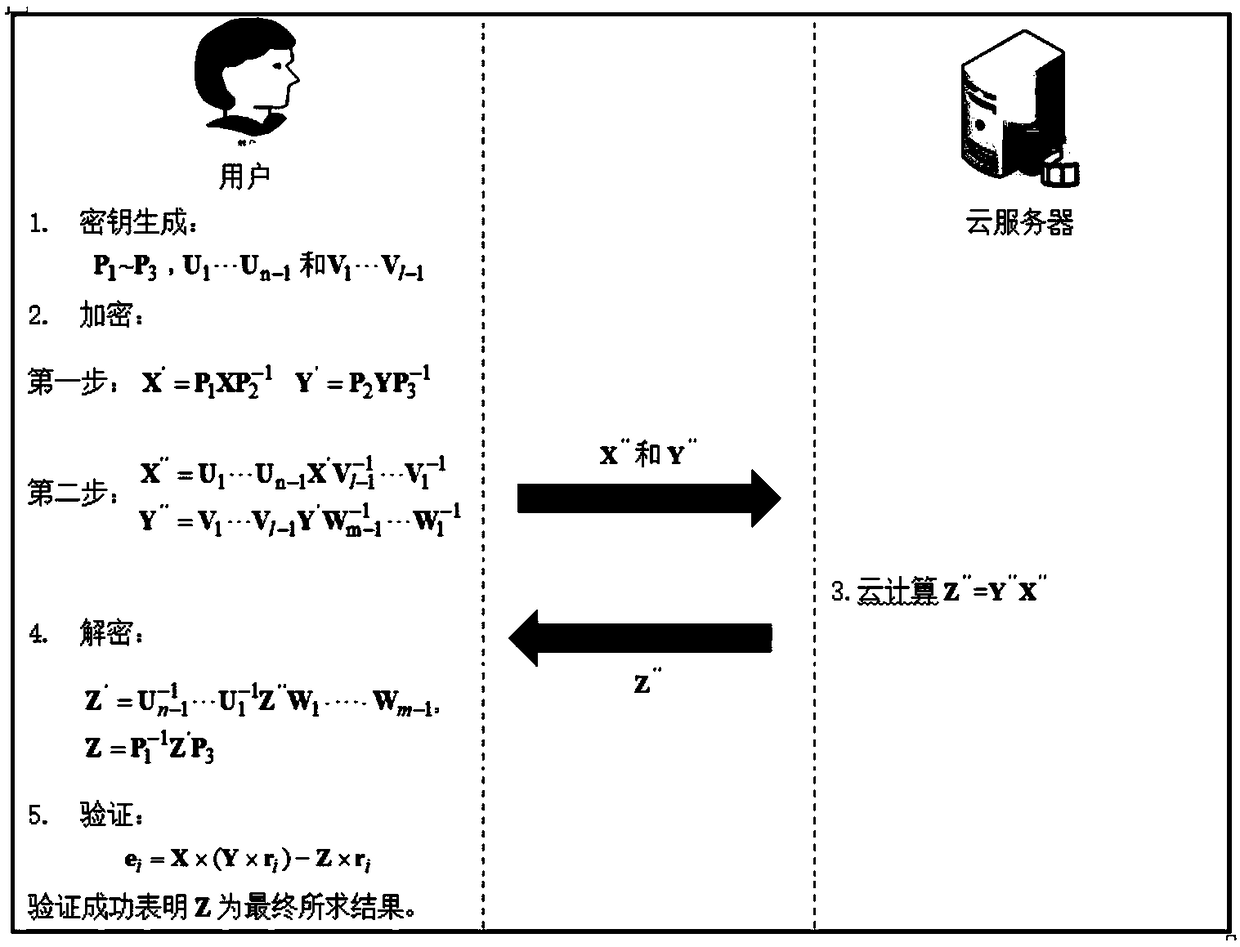
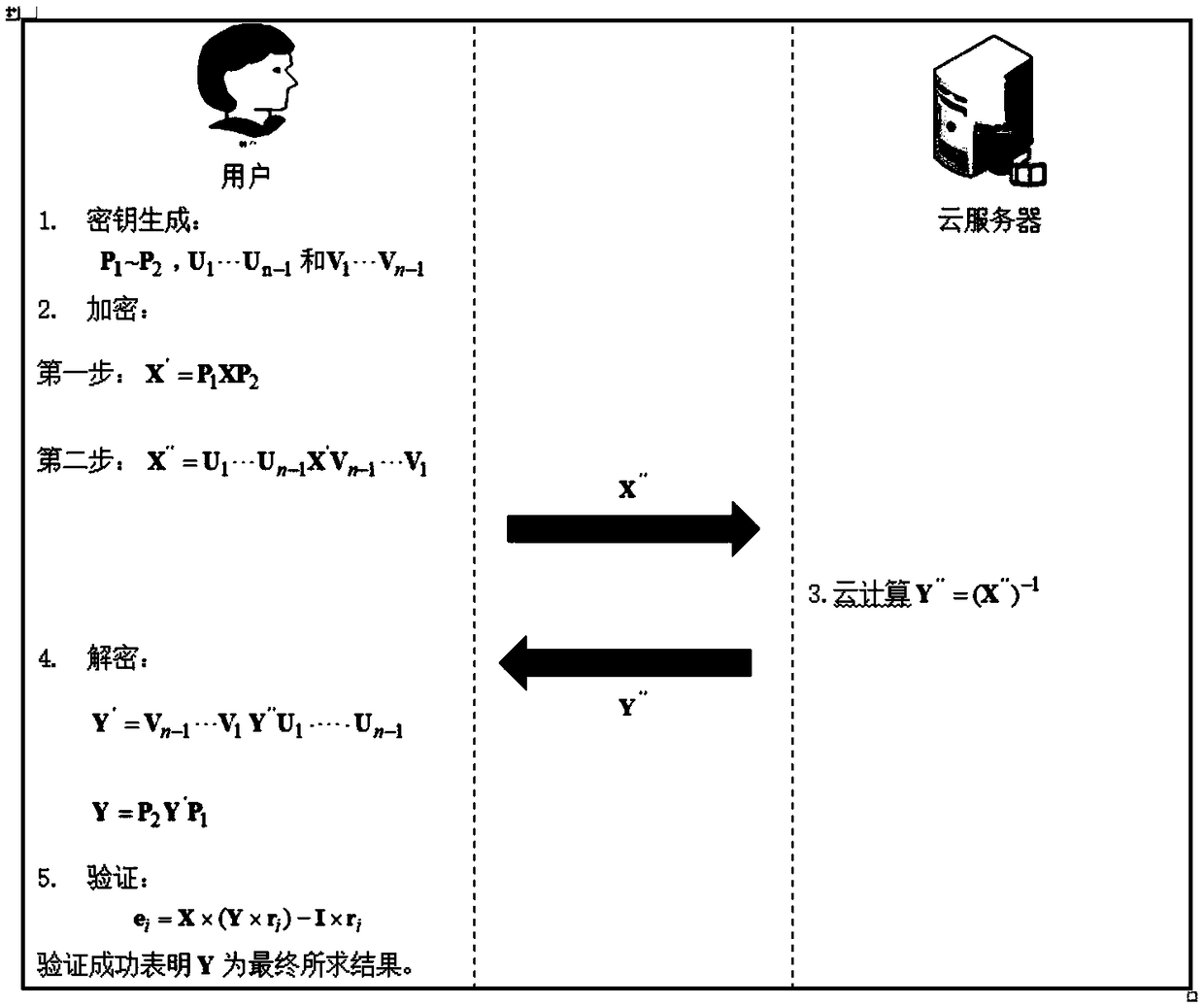
Secure outsourcing algorithm for large-scale matrix operation
A security outsourcing, matrix operation technology, applied in the field of cloud computing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] One, the relevant theory applied in the present invention
[0057] (1) Definition of finite field
[0058] Finite field or Galois Field (Galois Field), is a finite set containing q elements It defines two operations of addition (.) and multiplication (+), which satisfy the following properties
[0059] ① collection The Abelian group is formed under the addition operation, and its addition identity element is denoted as
[0060] ② collection The non-zero elements of form an Abelian group under the multiplication operation, and its multiplicative identity element is
[0061] ③ Multiplication satisfies the distributive law with respect to addition, that is, for any Satisfy
[0062] a·(b+c)=a·b+a·c and (b+c)·a=b·a+c·a
[0063] (2) Permutation and permutation matrix
[0064] Permutation functions are widely used in group theory and combinatorics. The permutation function is a bijection on the finite set {1, 2, ..., n}, which can be written as follows:
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com