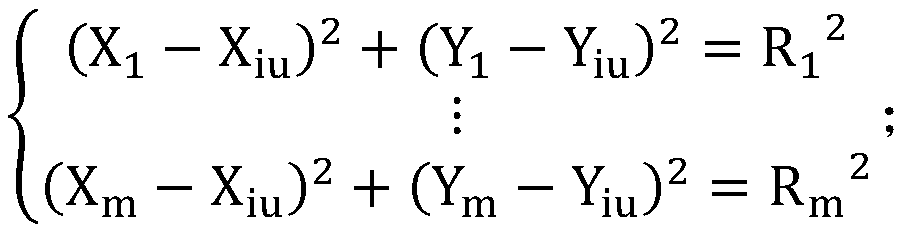Security detection method and device for laboratory internet-of-things management system
A management system and security detection technology, applied in the field of laboratory management, which can solve the problems of few Internet of Things and no in-depth research.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
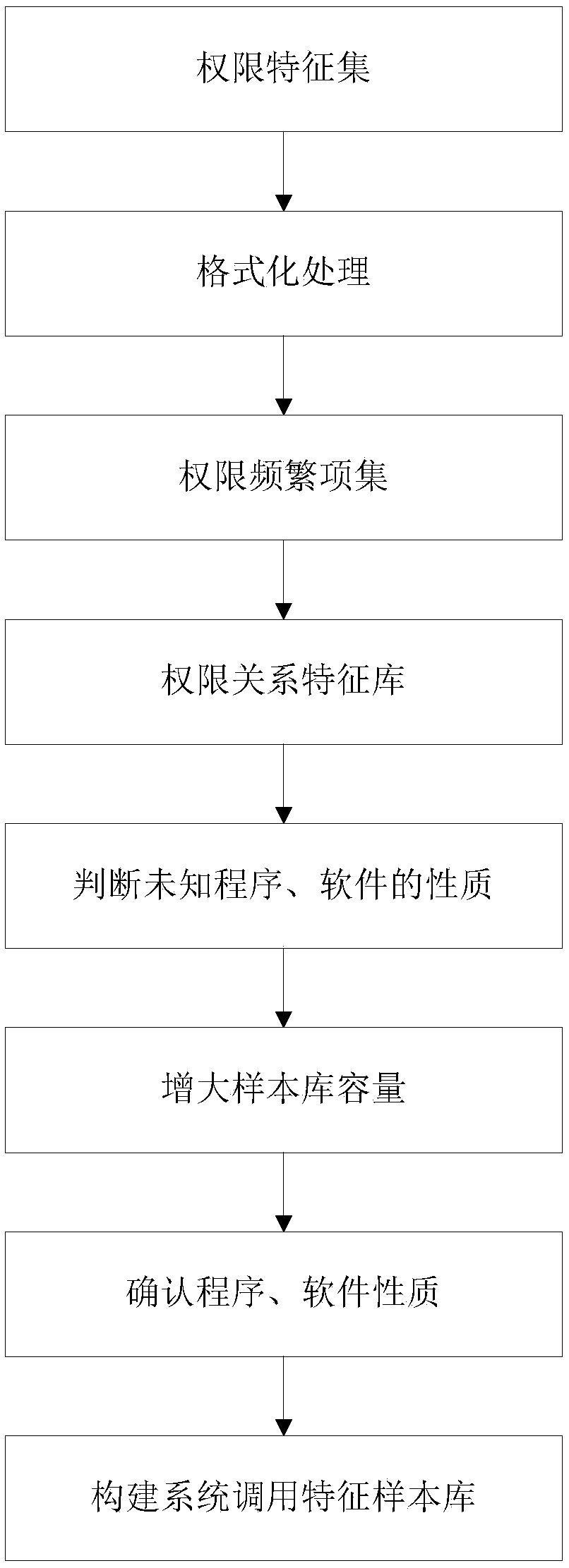
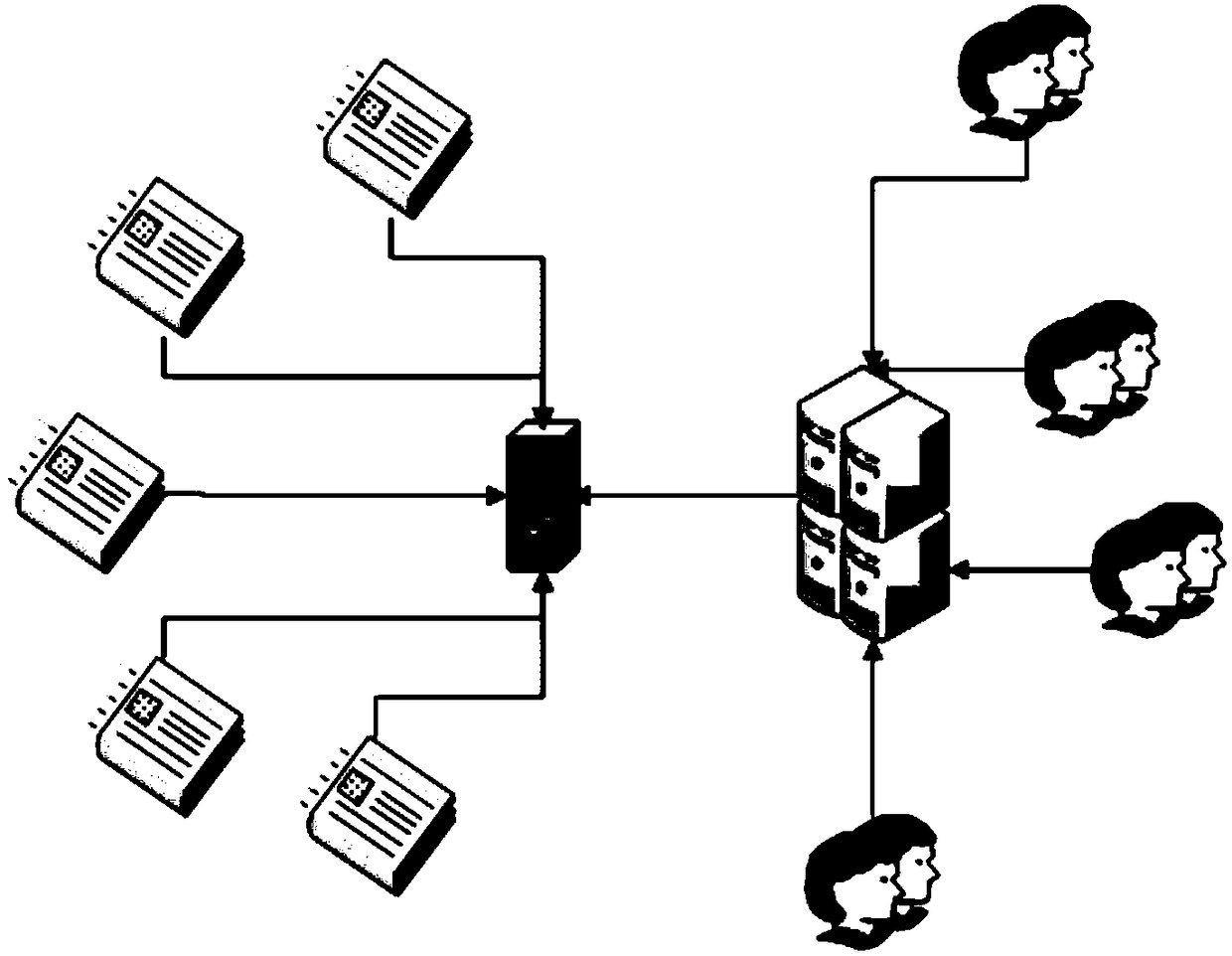
[0099] combine figure 1 , the present invention specifically relates to a safety detection method of a laboratory Internet of Things management system. Usually, the laboratory Internet of Things management system includes the equipment numbers i1, i2, i3...in that the laboratory requires to manage, such as various laboratory equipment, testing equipment, demonstration equipment, processing equipment, etc., where n represents the number of equipment Serial number, laboratory relay system A, laboratory IoT management system server B, and server connection terminal C connected to each other through network information or radio information. It should be noted that: server connection terminal C includes but not limited to: server connection WEB Handheld terminals connected to terminals and servers, including but not limited to: tablets, mobile phones, etc. For the above-mentioned laboratory IoT management system, for example, in a separate laboratory room, a computer host or tablet...
Embodiment 2
[0102] Same as Embodiment 1, further, the server B of the laboratory Internet of Things management system performs real-time classification, processing and storage of the data fed back by the equipment required by the laboratory and the data fed back by the server connection terminal C; the data includes laboratory requirements management The report information of the equipment, the environmental information of the reference location, the physiological information of the user, and the positioning information; among them, the report information of the equipment that the laboratory requires management is the network access information that is prompted after the equipment that the laboratory requires management is successfully connected to the network; the positioning information is the network access information. After success, the network ID and the corresponding physical address ID obtained automatically by server B of the laboratory Internet of Things management system, the net...
Embodiment 3
[0106] Same as Embodiment 1, further, the laboratory requires the managed equipment to monitor the location through the laboratory relay system A and the laboratory Internet of Things management system server B, so as to obtain the location of the lost equipment iu. The specific methods include:
[0107] (2.1) Let the coordinates of the lost device iu be (X iu , Y iu ), let the coordinates of the m devices associated with the missing device iu be (X 1 , Y 1 ), (X 2 , Y 2 )…(X m , Y m ), m≥3;
[0108] (2.2) The Euclidean distance R between the lost device iu and the associated m devices j for:
[0109]
[0110] Wherein, j=1,2,...,m; The above formula is deduced:
[0111]
[0112] Calculate the coordinates of the lost device iu by using the simplified structure:
[0113]
[0114]
[0115]
[0116]
[0117] The above parameters all have specific coordinate calculation methods, which are symbolic parameters set for the convenience of formulation;
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com