Code clone detection method based on hash value, electronic device and storage medium
A detection method and hash value technology, which are applied in software engineering design, electrical digital data processing, instruments, etc., can solve the problems of lack of migration, can only detect a specific version of the language, and cannot detect COBOL, and achieve good migration. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Below, the present invention will be further described in conjunction with the accompanying drawings and specific implementation methods. It should be noted that, under the premise of not conflicting, the various embodiments described below or the technical features can be combined arbitrarily to form new embodiments. .
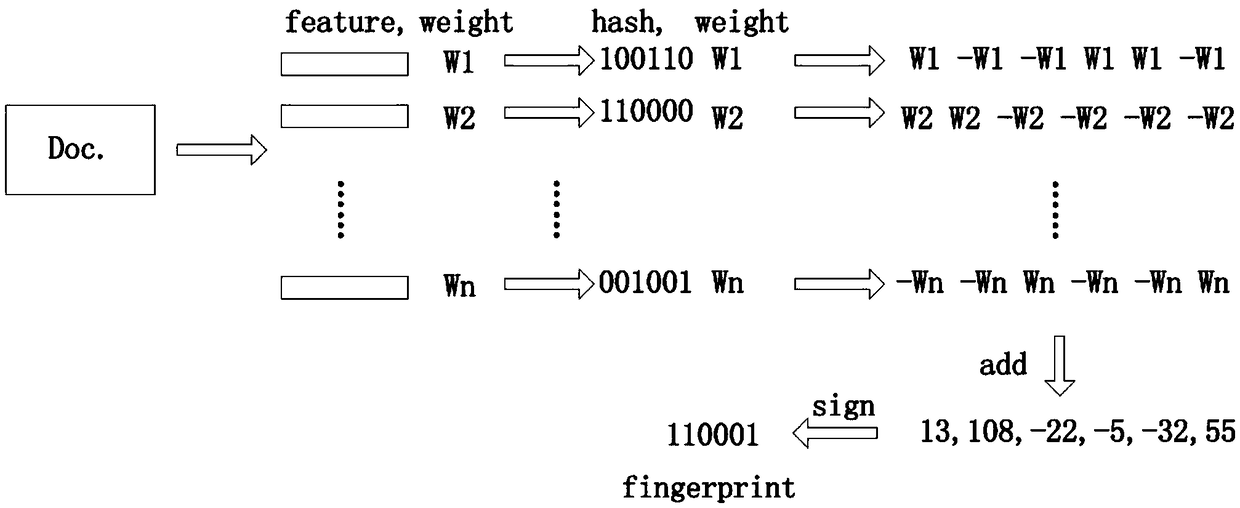
[0025] In one embodiment, given a software system that needs to be checked, the set of all source code files it contains is F=[f 1 ,f 2 ,..., f m ], where f i represents the i-th source code file. in f i In the source code file there is f i (j) code snippets [c 1 ,c 2 ,...,c fi(n) ], where code fragment c refers to the smallest granularity code block that needs to detect code cloning, such as a paragraph in COBOL, or a method in JAVA. The total number of all code fragments in a system is represented by m, and its set is C. Code cloning is described in the form of w, a pair of code cloning w=(c 1 ,c 2 ). The set of all code clones in the sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com