SDN information access control method based on certifiable hierarchical attribute encryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be described in detail below in conjunction with the accompanying drawings and examples.
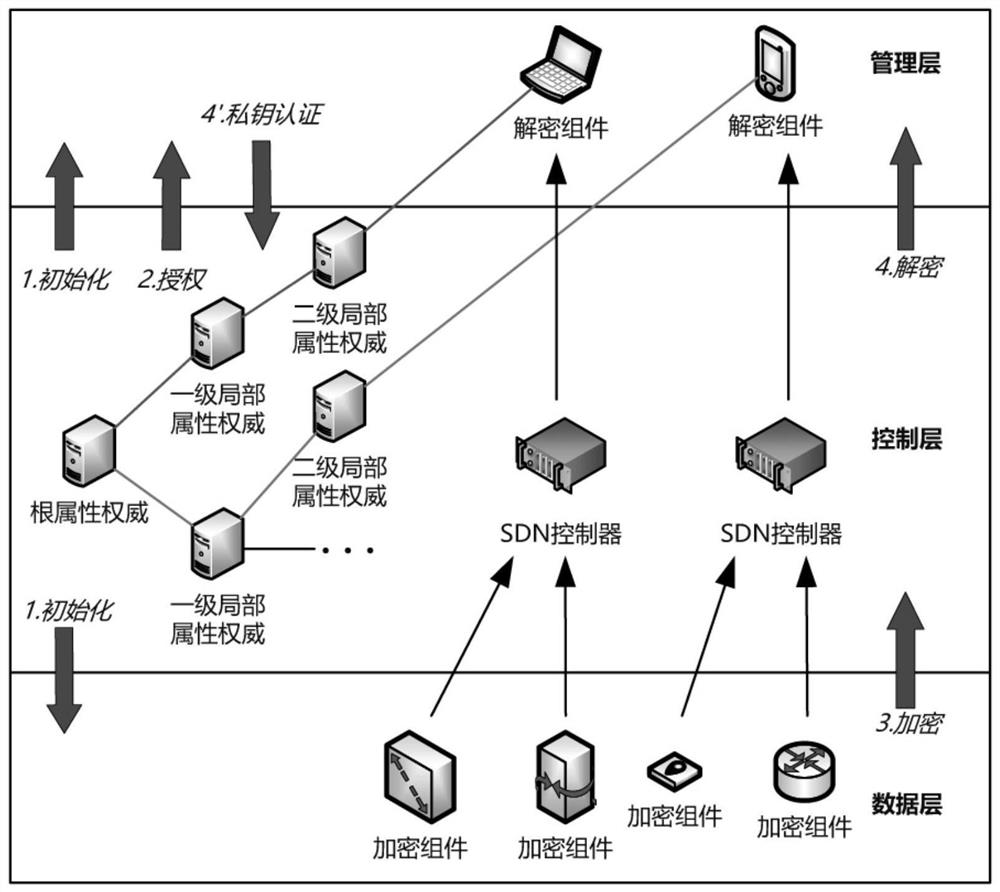
[0071] see figure 1 , the method system of the present invention is distributed in the data layer, control layer and management layer of SDN, including a control system composed of four roles: attribute authority, SDN controller, encryption component and decryption component, wherein the attribute authority includes root attribute authority and local attribute authority. When the method of the invention is started, the root attribute authority first executes the initialization operation and transmits parameters to the encryption component of the data layer and the decryption component of the management layer. Secondly, starting from the root attribute authority, iteratively realizes the authorization operation layer by layer, including local attribute authority authorization and user authorization. Then the encryption component located in the data lay...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com