Target vulnerability analysis method
An analysis method and vulnerability technology, applied in the field of damage theory analysis, can solve the problems of insufficient accuracy, high cost, and large resource consumption, and achieve the effect of less resource occupation, short time consumption and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
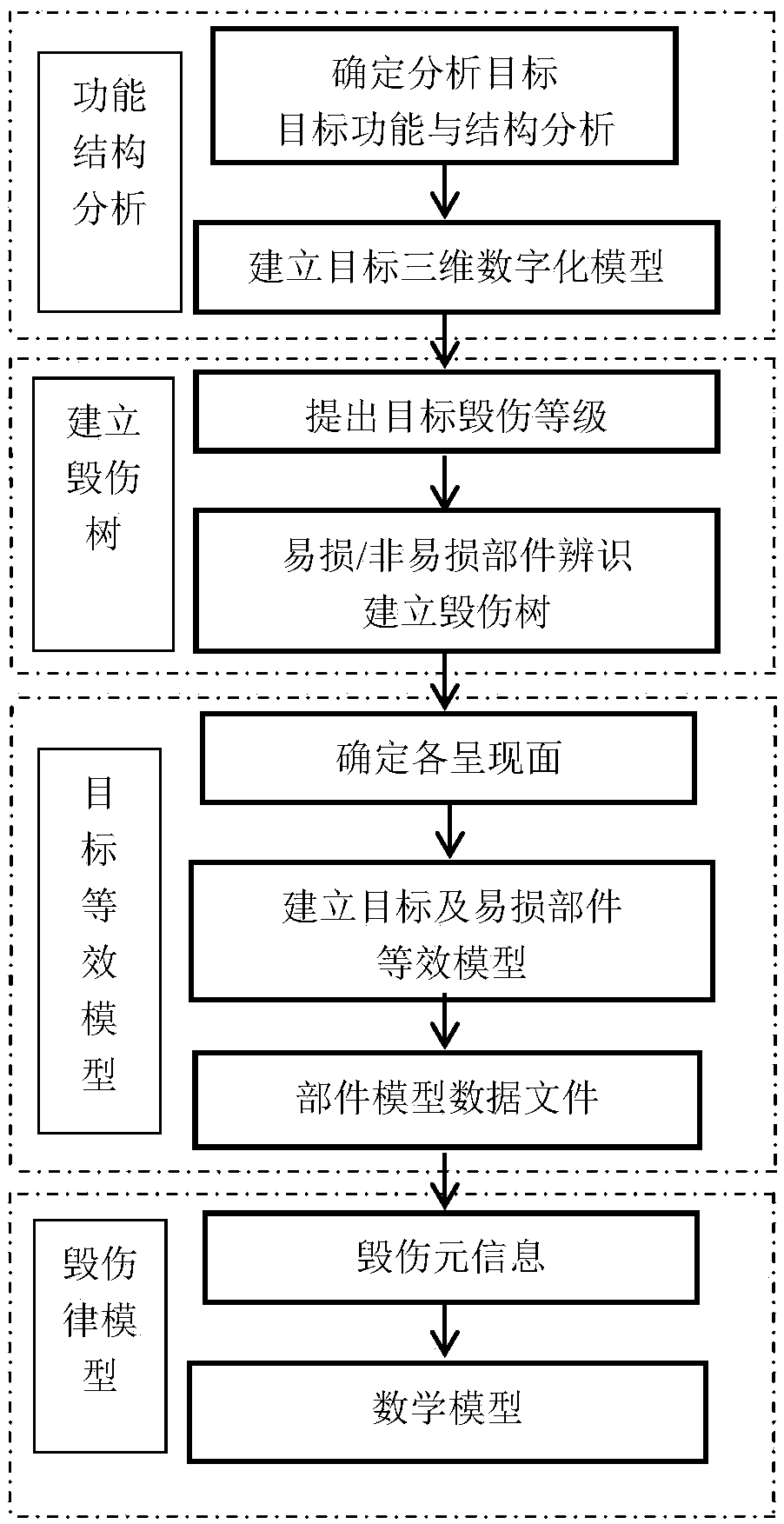
[0022] Target vulnerability refers to the possibility of the target being damaged under the action of ammunition damage elements under the condition that the target is detected. Use is very important. Vulnerability modeling avoids various characteristics of previous vulnerability models, such as too simple or complex modeling and long calculation time, which can effectively improve the efficiency and accuracy of vulnerability analysis.
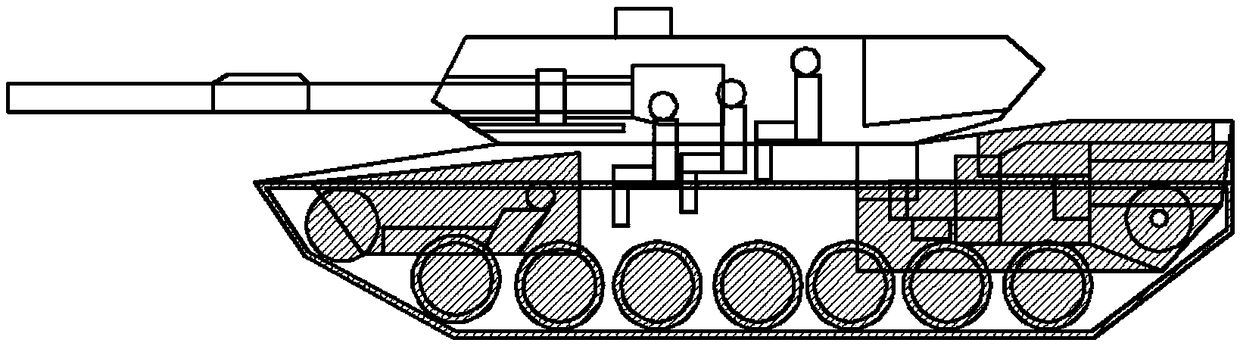
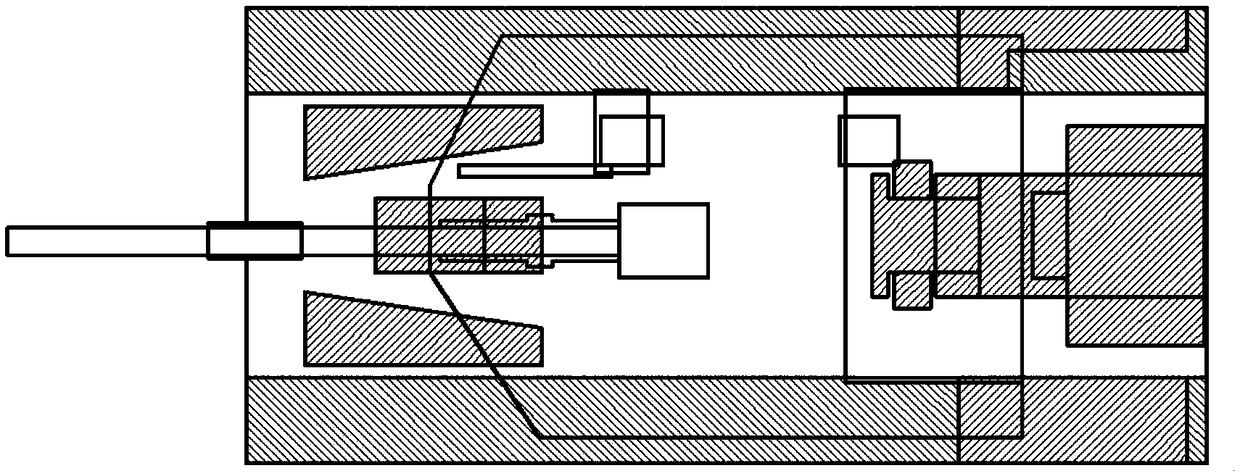
[0023] Such as Figure 1 As shown, the specific process of the present invention is: analyze the function and structure of the determined research target, establish a three-dimensional digital model of the target, and give the target structure tree; based on the target analysis and structure tree, propose damage levels and identify vulnerable / non-destructive Establish the damage tree corresponding to the vulnerable parts; judge the typical attack direction of the damage element on the target according to the shape and structure characteristic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com