A process behavior monitoring device and method free of superuser privilege
A technology of super user authority and monitoring device, applied in hardware monitoring, instrumentation, error detection/correction, etc., can solve problems such as inability to monitor native layer operations, detection of malware, etc., to achieve efficient and stable monitoring, concealment of monitoring systems, The effect of monitoring a large range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0092] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
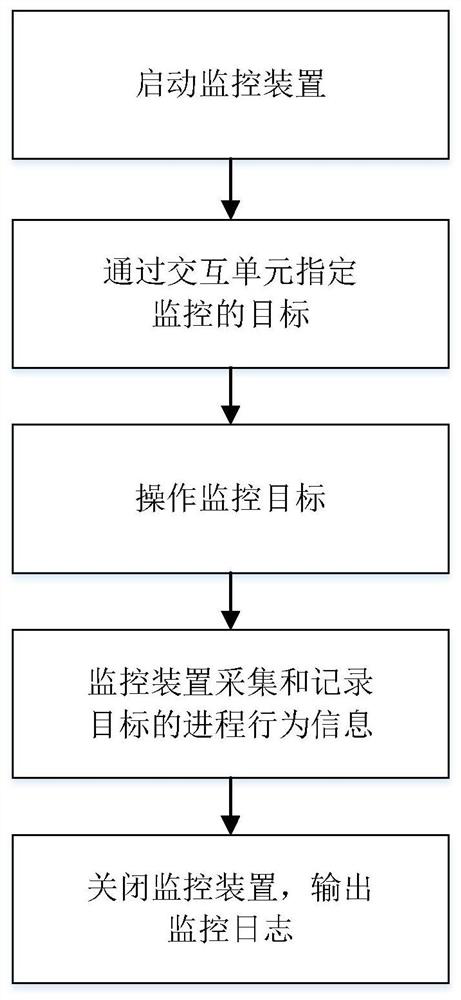
[0093] refer to figure 1 , the present invention is a process behavior monitoring method exempt from superuser authority, and the flow process is as follows:
[0094] activate the monitoring device;
[0095] Specify the target of monitoring;
[0096] Action goals, trigger behaviors;
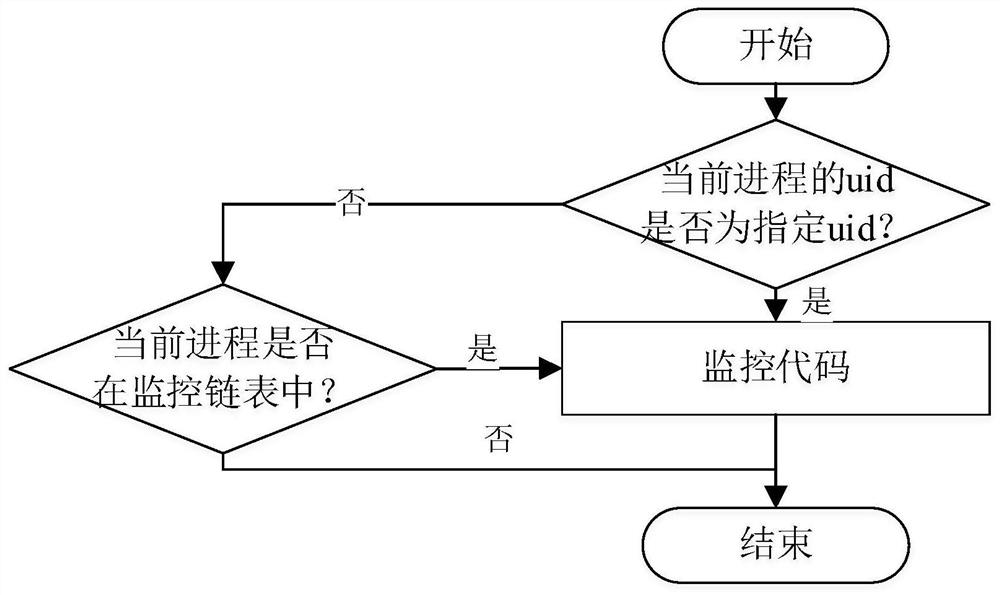
[0097] The monitoring device collects and records the process behavior information of the target, and generates a monitoring log;
[0098] Close the monitoring device and output the monitoring log.
[0099] The process behavior monitoring device exempt from super-user authority of the present invention, the detailed introduction of each unit of it is as follows:
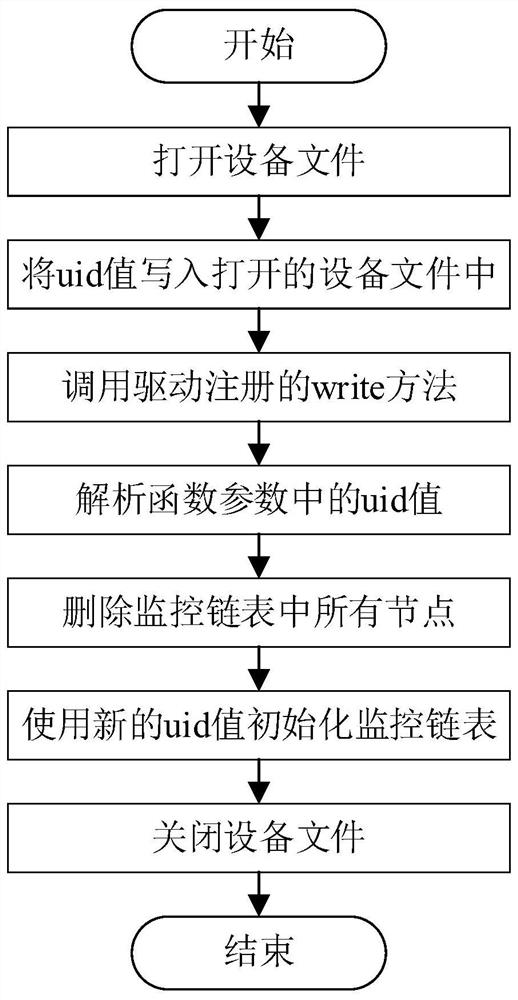
[0100] 1. Interactive unit
[0101] Write an interactive tool, which can interact with the monitoring device when the system is running, and dynamically modify the monitoring target. Process such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com