A software authorization license implementing method and apparatus
A software authorization and implementation method technology, applied in computer security devices, program code conversion, instruments, etc., can solve problems such as unusable software, inability to connect the client to the server, failure to start the server, etc., to avoid reuse of license , to achieve security control, increase the effect of difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
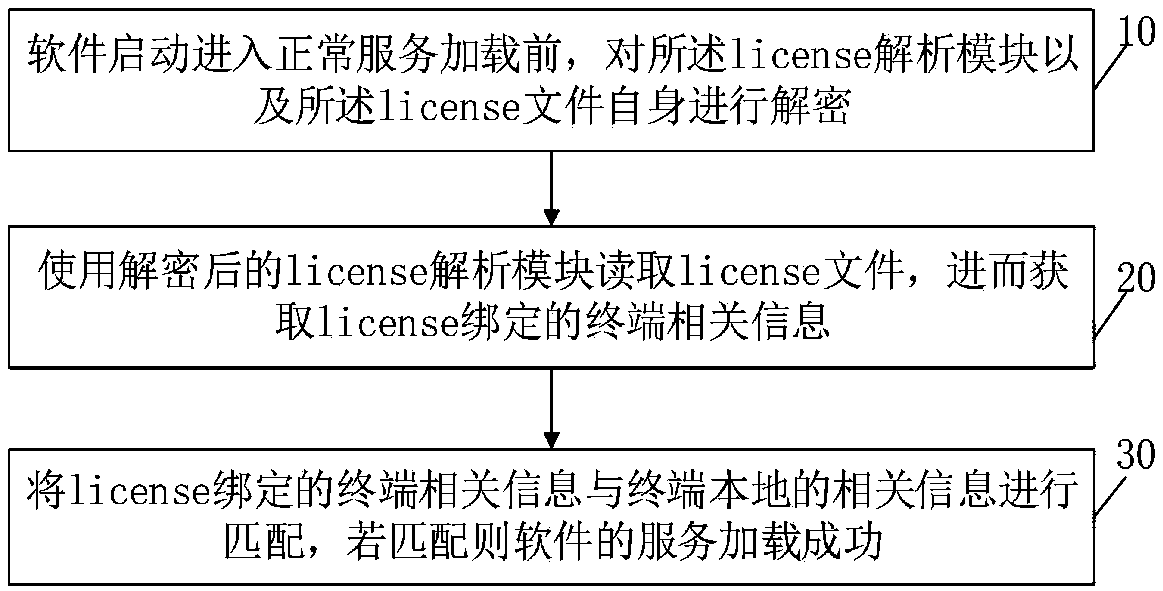
[0049] The embodiment of the present invention provides a method for implementing software authorization. First, when the software is packaged as an installation file, the license analysis module is encrypted by the license encryption module, and the license file itself is encrypted during the license production process. The encryption algorithm Both are DES algorithms; the difficulty of directly decompiling java class files is increased through double encryption, and a certain degree of security control over license files is achieved. Second, when making a license, bind terminal-related information to the license. The terminal is the end that runs the software, that is, the user side that buys the license. The terminal can be a server or a PC, and the end that sells the license is recorded as the remote server.
[0050] In the embodiment of the present invention, the terminal-related information includes product type, product version, operating system, expiration date, and ph...
Embodiment 2
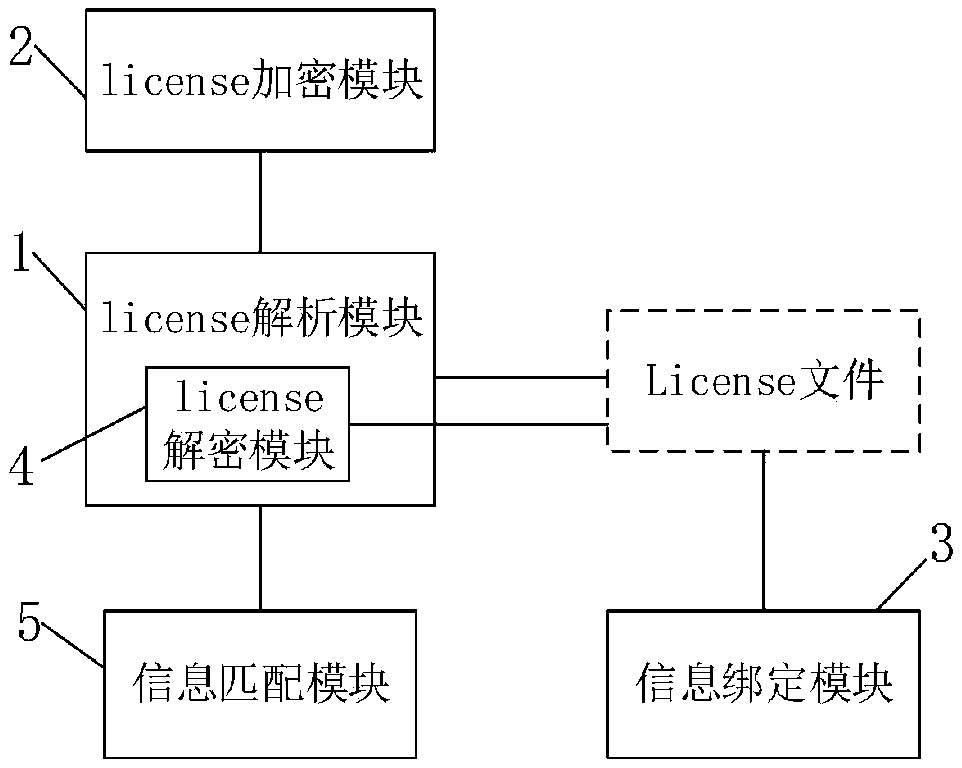
[0078] On the basis of the above-mentioned embodiment 1, the embodiment of the present invention also provides a system for implementing a software authorization license, which is used to implement the method for implementing a software authorization license described in Embodiment 1, such as image 3 As shown, the system includes:
[0079] The license parsing module 1 is used to read the information of the license file.
[0080] The license encryption module 2 is used to encrypt the license analysis module 1 during the software production process, and the encryption algorithm is the DES algorithm.
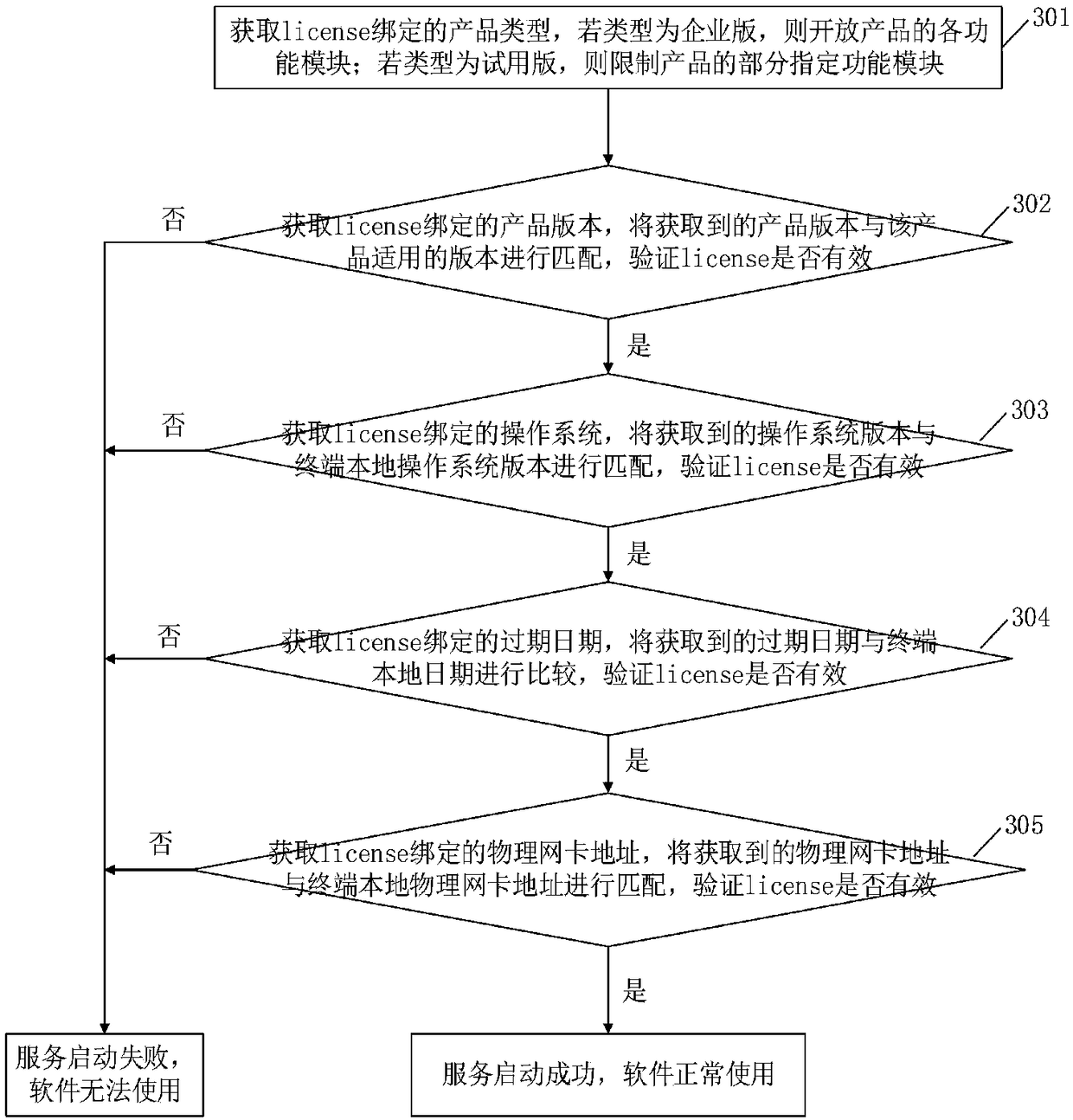
[0081] The information binding module 3 is used to bind the license and terminal related information when making a license; in the embodiment of the present invention, the terminal related information includes product type, product version, operating system, expiration date and physical network card address, Bind the above information separately when making the license. On the b...
Embodiment 3
[0092] On the basis of the software authorization implementation method provided in Embodiment 1 and the software authorization implementation system provided in Embodiment 2, the present invention also provides a software authorization implementation device, which can be used to implement the software authorization license implementation described in the embodiment. The software authorization license implements the functions of the terminal described in the method. Such as Figure 5 As shown in FIG. 2 , it is a schematic diagram of the architecture of the device for implementing software authorization in the embodiment of the present invention. The apparatus for implementing software authorization in this embodiment includes one or more processors 21 and memory 22 . in, Figure 5 A processor 21 is taken as an example.
[0093] The processor 21 and the memory 22 may be connected via a bus or in other ways, Figure 5 Take connection via bus as an example.
[0094] The memory...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com