System and method for detecting violent events in image based on anchor node
An event detection and anchor node technology, applied in computer parts, instruments, characters and pattern recognition, etc., can solve the problems of being easily affected by noise, unable to achieve real-time effects, etc., and achieve the effect of improving efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
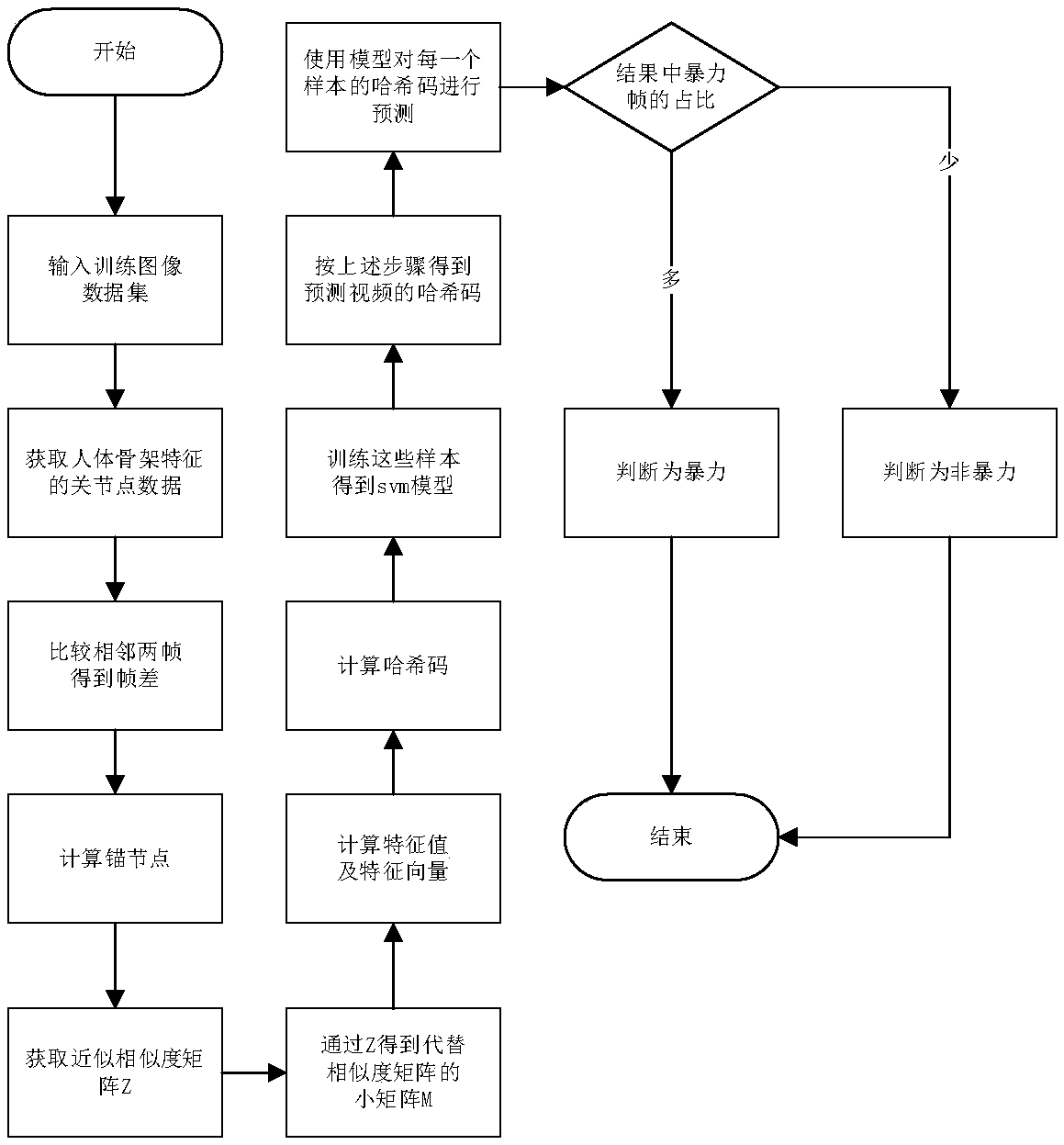
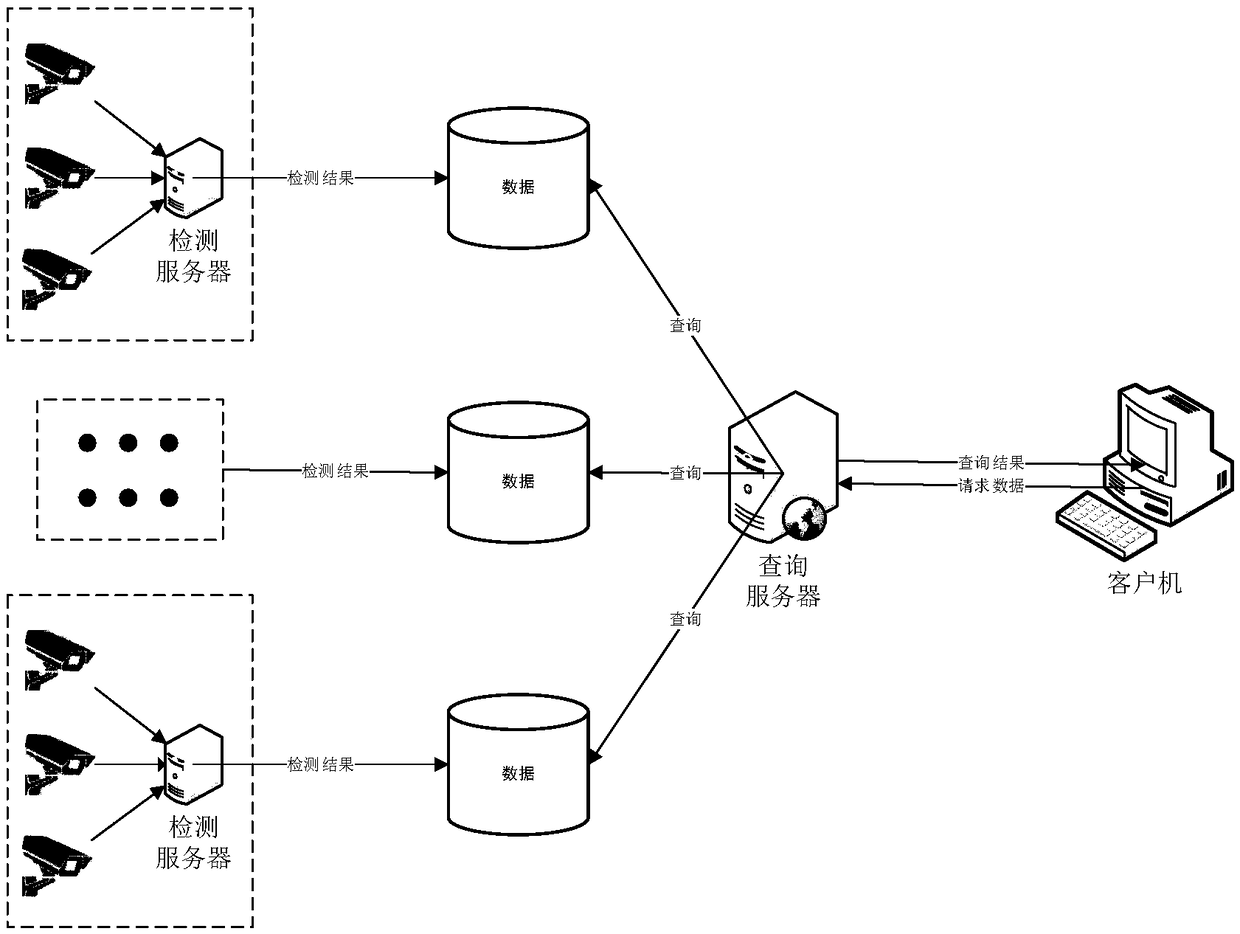
[0068] The scene described in this embodiment is: a distributed application scene that does not need real-time processing, such as after the cameras of several streets capture images, the images are transmitted to a host to store image files, and the host processes the images of a small number of cameras corresponding to it. image and obtain the prediction results, and temporarily store the results locally, and upload the temporarily stored prediction results to their respective databases at regular intervals of several hours, and provide query functions for clients through the reverse proxy server. The client computer does not feel the existence of multiple databases, and can directly access the data of a large number of cameras, such as figure 2 As shown, the specific steps are as follows:
[0069] Before the deployment of the system, collect a large number of image data sets used for training on the network or other channels, organize the data sets, accurately classify all...
Embodiment 2
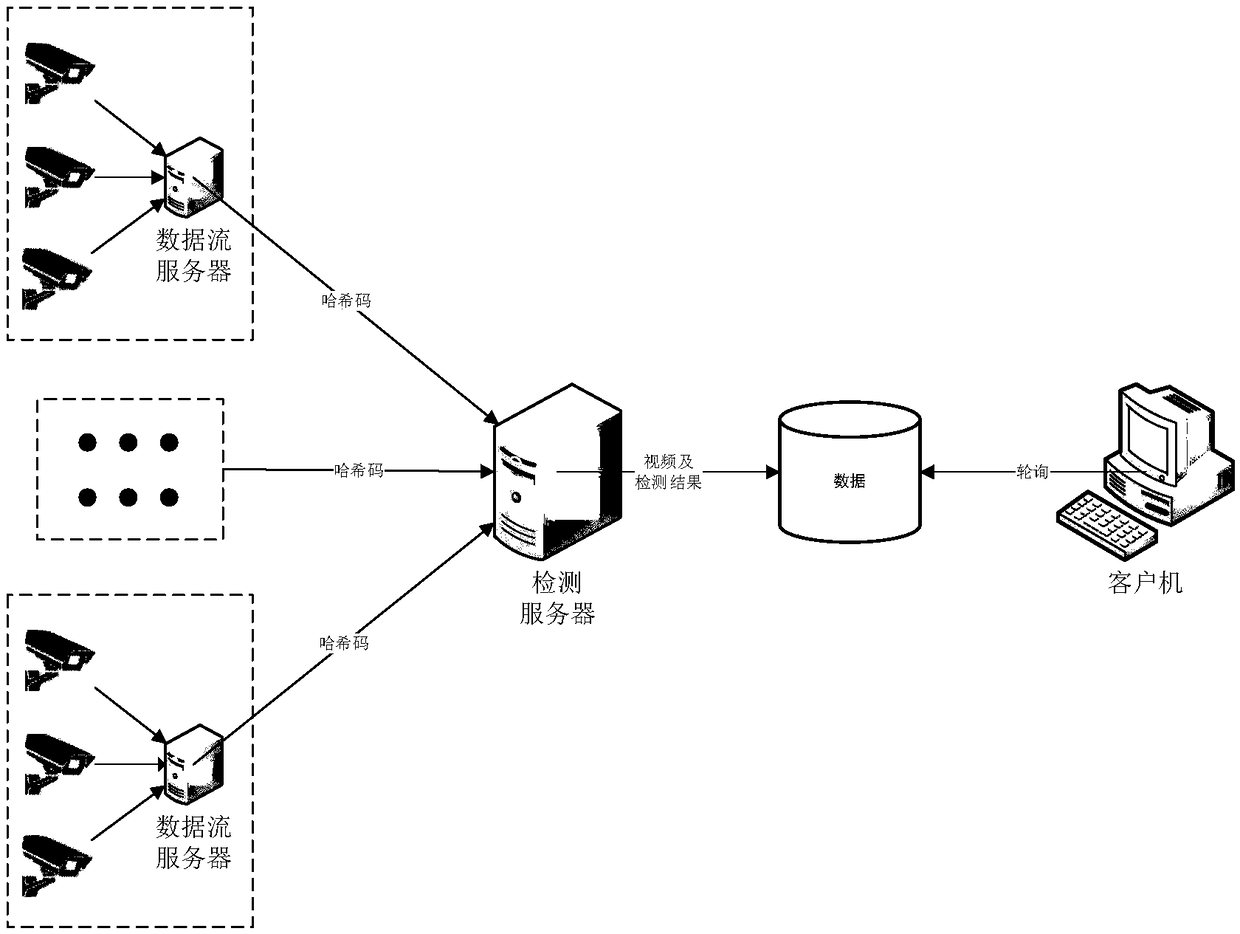
[0074] The scene described in this embodiment is: some special places that require real-time centralized processing of images. Since the area is generally small and there are fewer cameras overall, the demand for real-time monitoring of violent events is high. Therefore, centralized real-time prediction of these images is required. Each video streaming server is only connected to a small number of cameras. These servers are only responsible for image storage and a small amount of processing to obtain hash codes. These hash codes will be marked and sent to the same detection server. The server quickly detects and simultaneously Stored in the database, the client will poll the database and issue a warning when a violent event is found. refer to image 3 ,Specific steps are as follows:
[0075] Before the deployment of the system, collect a large number of image data sets used for training on the network or other channels, organize the data sets, accurately classify all image da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com