Token generation method, token-based tracking method and device
A technology with preset algorithm and encryption algorithm, applied in the Internet field, it can solve problems such as low request efficiency, insecure information, and inability to track clients.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
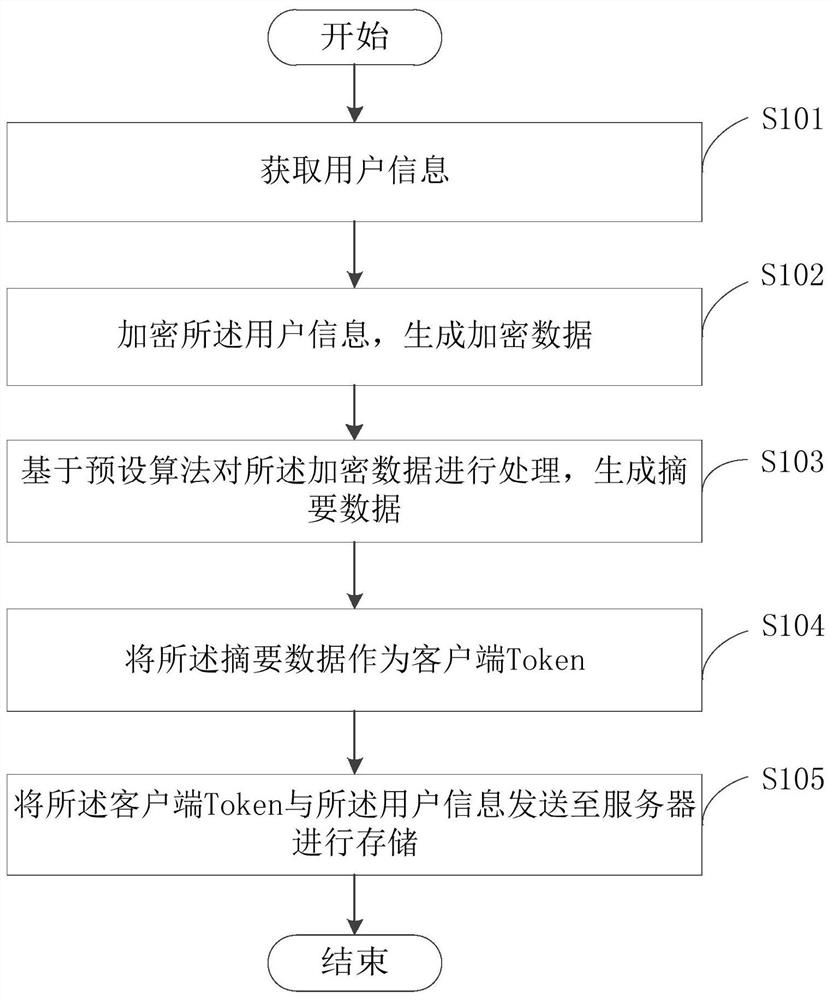
[0030] see figure 1 , is a flow chart of the Token generation method provided by the embodiment of the present invention. The following will be figure 1 The specific process shown will be described in detail.
[0031] Step S101, acquiring user information.
[0032] Optionally, the user information includes, but is not limited to, a user site ID and a MAC (MediaAccess Control or MediumAccessControl) address. For example, the MAC address could be 00:1d:d8:b7:1e:27.
[0033] User information is collected through a pre-installed client program, and the client program is a program delivered to the user by the service platform. The client program is mainly used to query and collect service platform data.
[0034] Wherein, the user site identifier refers to the name of the customer. For example, the customer name is XXX company or business.
[0035] Step S102, encrypting the user information to generate encrypted data.
[0036] As a possible implementation manner, step S102 i...
no. 2 example
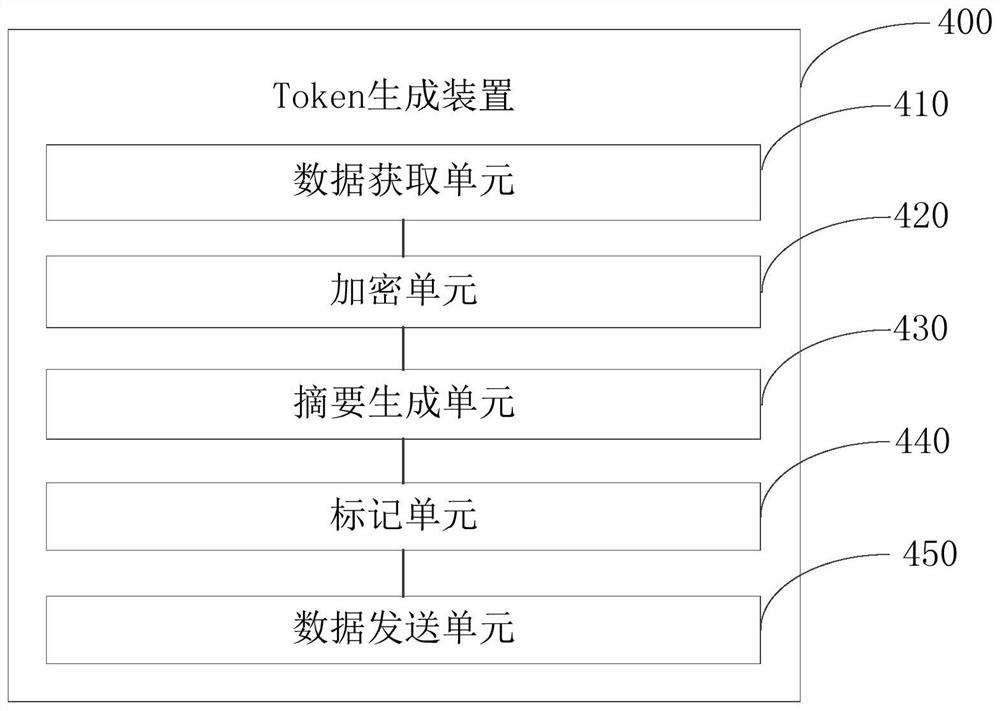
[0047] Corresponding to the Token generation method in the first embodiment, figure 2 It shows a Token generation device that adopts the Token generation method shown in the first embodiment in one-to-one correspondence. Such as figure 2 As shown, the Token generation device 400 includes a data acquisition unit 410 , an encryption unit 420 , a digest generation unit 430 , a marking unit 440 and a data sending unit 450 . Among them, the implementation functions of the data acquisition unit 410, the encryption unit 420, the abstract generation unit 430, the marking unit 440 and the data sending unit 450 correspond to the corresponding steps in the second embodiment one by one. a detailed description.
[0048] The data acquiring unit 410 is configured to acquire user information.
[0049] The encryption unit 420 is configured to encrypt the user information to generate encrypted data.
[0050] Optionally, the user information includes a user site ID and a MAC address, and t...
no. 3 example
[0056] see image 3 , is a flow chart of the Token-based tracking method provided by the embodiment of the present invention. The following will be image 3 The specific process shown will be described in detail.
[0057] In step S201, the server receives the request information sent by the client, and the request information includes the client Token and behavior information.
[0058] Optionally, each time the client requests an operation from the server, it will POST the client Token to the server. That is, the server obtains the client Token and behavior information sent by the client by requesting a session.
[0059] Wherein, for the specific implementation manner of the client Token, please refer to the content recorded in the first embodiment, which will not be repeated here.
[0060] The behavior information may be operation information requested by the user, such as update, query and other operation information.
[0061] For example, the client token is 2FE6A8A20D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com